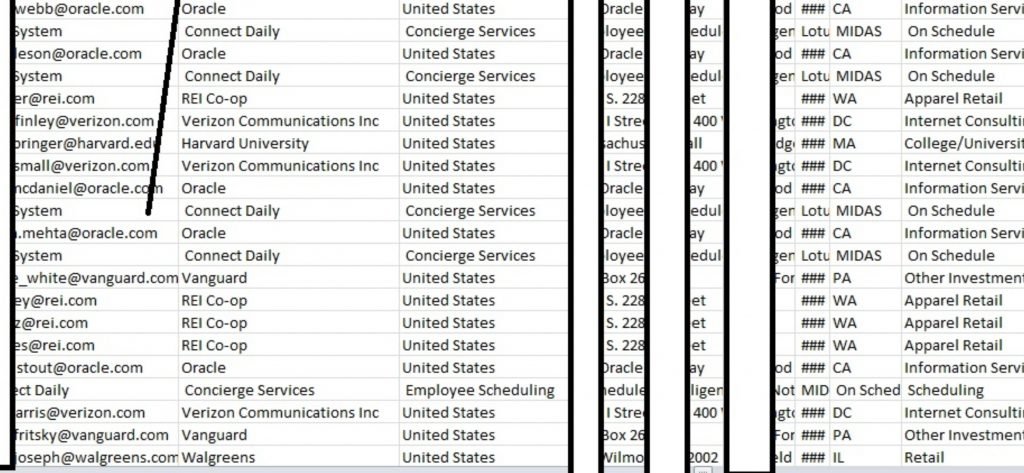
Cyber forensics research team has found a sale of database containing 2GB of records detailing information on employees of big corporate companies like Apple, Google, Microsoft, LinkedIn, Intel Cisco, Verizon, oracle and HP.
International institute of cyber security research team of Jim Gill and RSU found the database for sale on a deep web forum. The database contains extremely detailed information about individual homes ranging from the name, office address, home address, phone number, age, birthdates and official and personal email.
Data broker/hacker named Bastardlord has posted an advertisement for his database. The hacker mentions that the database is available over bidding.
Cyber forensics experts mentioned “Unlike previous leaks we’ve discovered, this time, we have no idea how the hacker got this database.
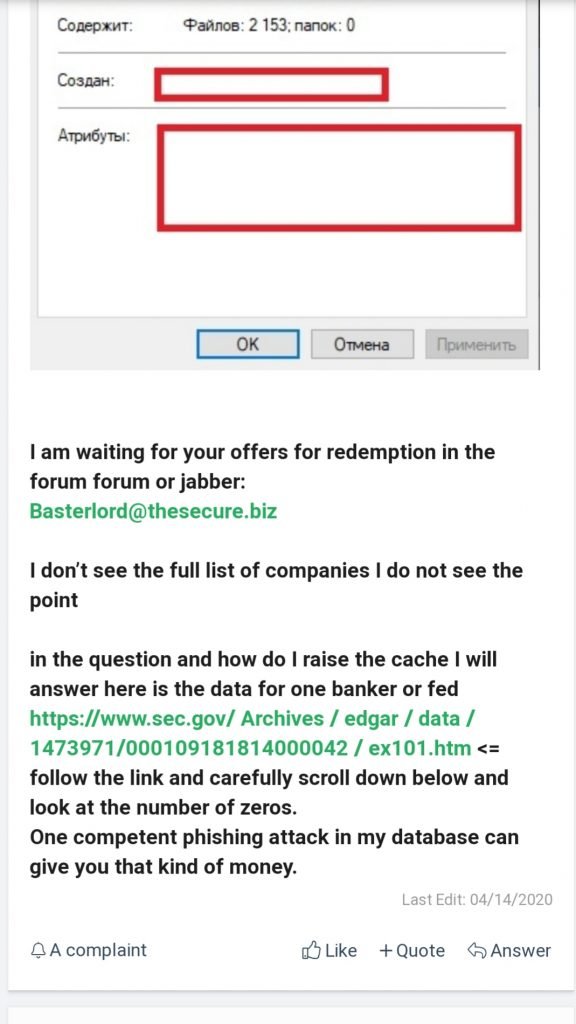
However, there are a few clues. Each records contains a employee ID indicating it could be from a some human resource database company, also there is a category for income level leading, cyber forensics experts to think it could be from a HR solutions company that provide HR ERP to big corporate companies like Apple, Google, Microsoft, LinkedIn, Intel Cisco, Verizon, oracle and HP.
Having no luck on there own research they have decided to crowd source the problem by asking others to put on their detective hats and ponder the clues available.
“What HR software is used by companies like Apple, Google, Microsoft, LinkedIn, Intel Cisco, Verizon, Oracle, HP, Nvidia, United stated department of transportation. What provider would be common among all these companies.?” He asked.
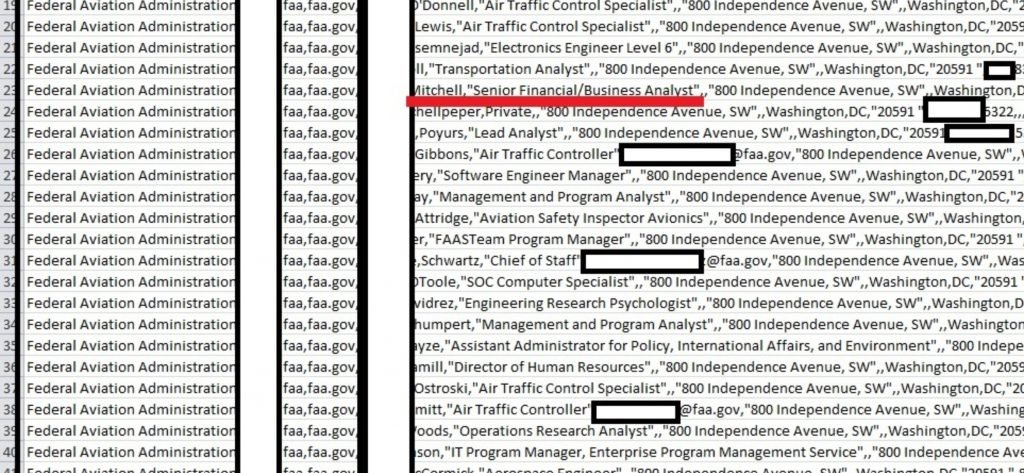
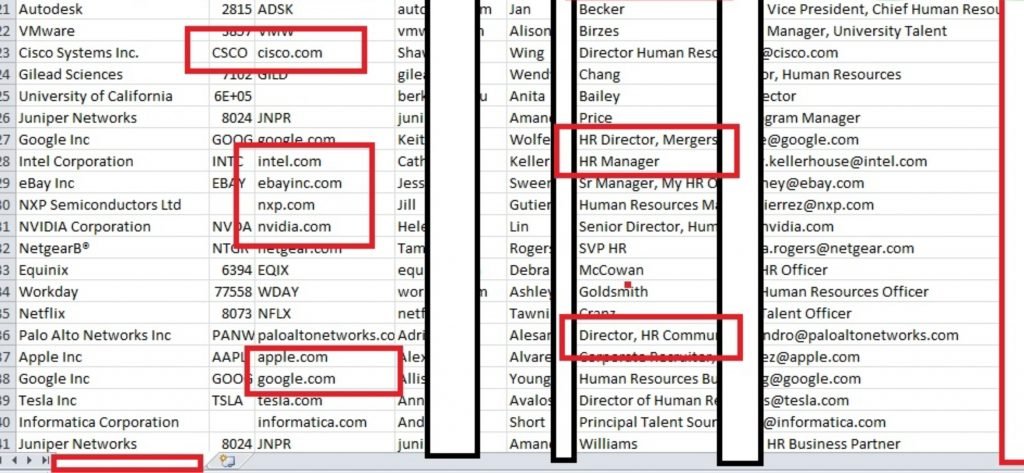
Even though the records do not include truly damaging information such as Social Security numbers or payment card information, the data available could still prove dangerous if in the wrong hands.
- There are enough data contained in the database to do vishing and phishing attacks.
- A name and address are enough to find out if a person lives in a wealthy area, and can lead to public social media accounts. With home address this info could be used to conduct burglaries.
- All the information together can be used to build a social engineering snapshot making a person vulnerable to a variety of exploits.
The database was discovered while the cyber forensics experts were conducting a deep web-mapping project.

Cyber Security Specialist with 18+ years of industry experience . Worked on the projects with AT&T, Citrix, Google, Conexant, IPolicy Networks (Tech Mahindra) and HFCL. Constantly keeping world update on the happening in Cyber Security Area.











