The Coronavirus/COVID-19 worldwide pandemic has forced governments and private organizations to work from home, which has help millions of citizens to be secure from this health threat, but has brought its own issues, as secure data erasure specialists mentioned.
Zoom has recently become one of the most useful tools for remote work, as users can stay in touch with colleagues. However, the increasing use of this platform has attracted the attention of threat actors. Also, while Zoom has become incredibly popular, it has an embarrassing user tracking record, which its users should consider.
In this document, the secure data erasure specialists describe some recently found and security privacy flaws that affect the version of Zoom for macOS; if exploited, these vulnerabilities could affect millions of users worldwide.
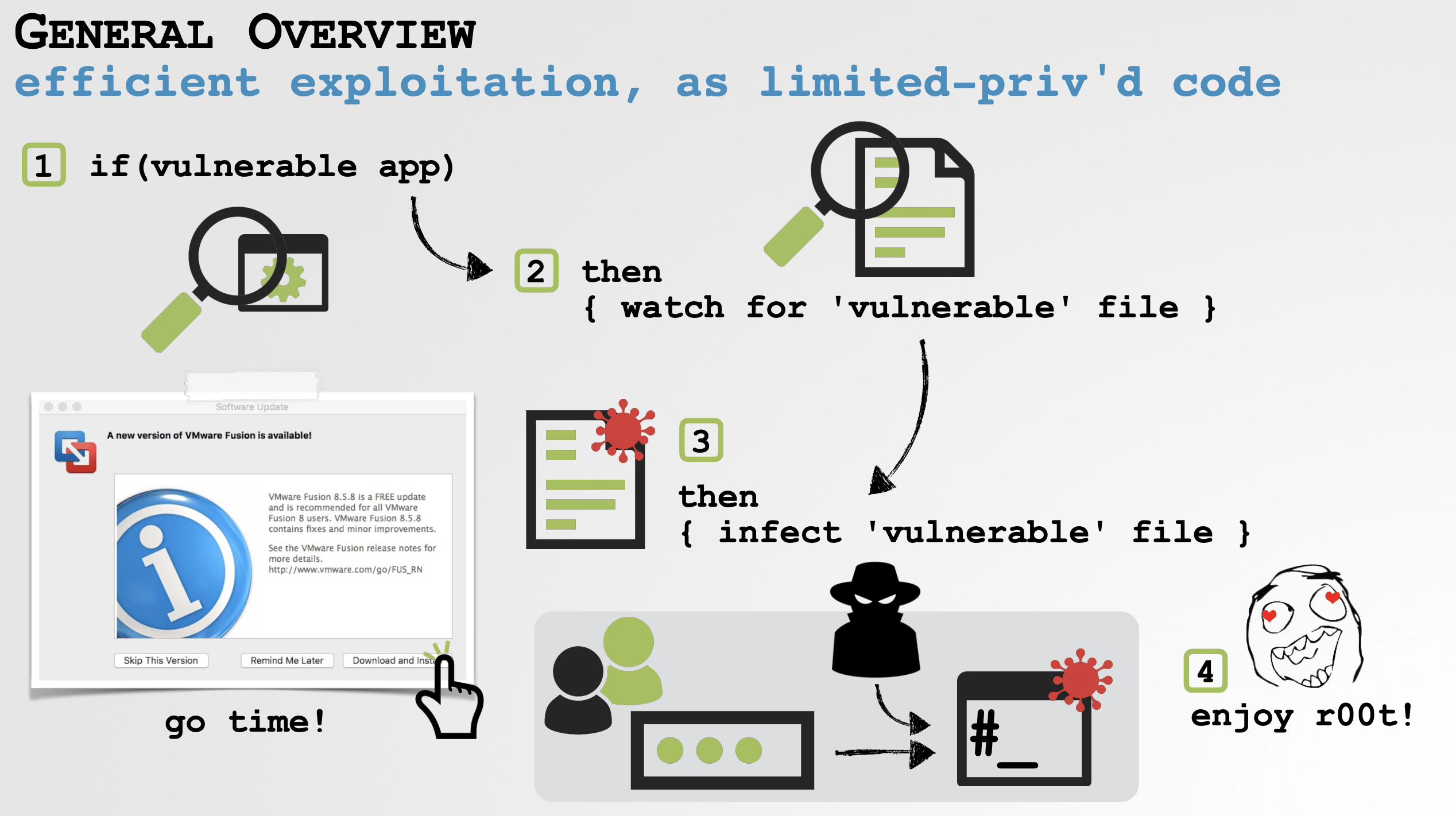
A team of researchers recently reported a zero-day flaw that allows webcam hijacking in the macOS version of the platform. According to the report, the vulnerability lets any website to forcibly join a user to a Zoom session, invoking the camera without target user’s permission.
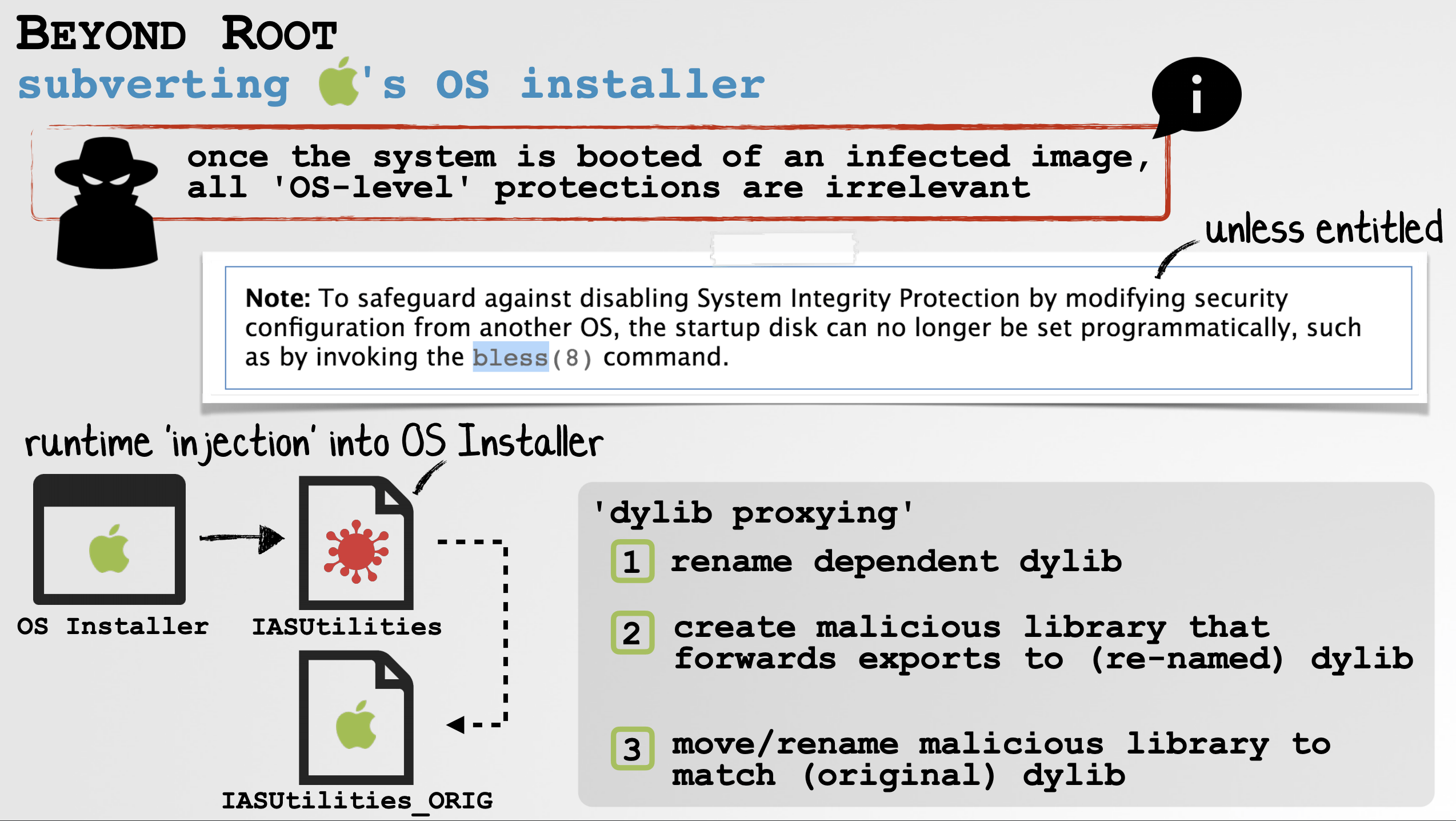
As if that were not enough, users who have ever installed a Zoom client and then uninstalled it, still have a localhost web server on their computers. As secure data erasure specialists mentioned, this localhost could reinstall the Zoom client without users’ interaction.
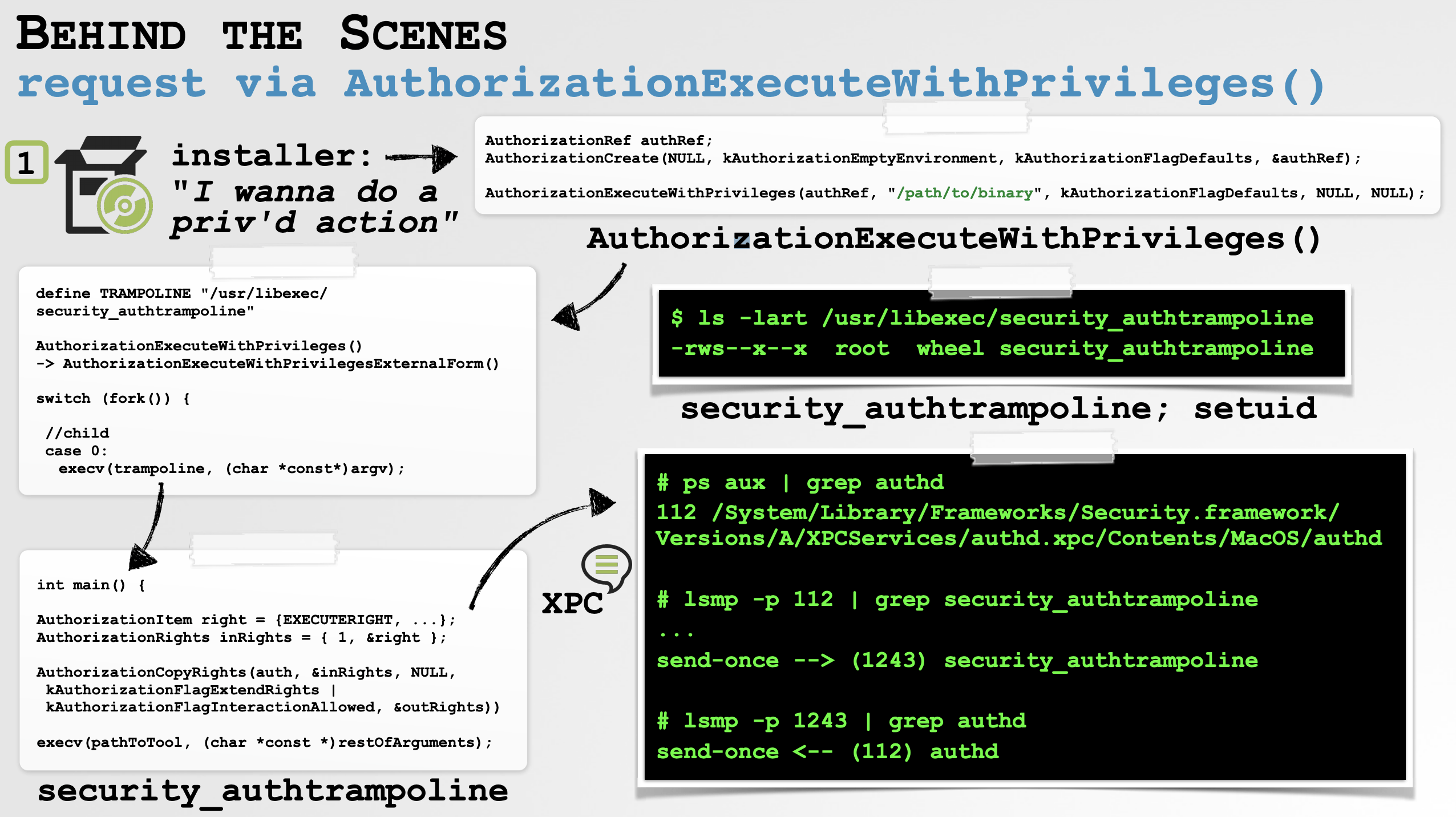
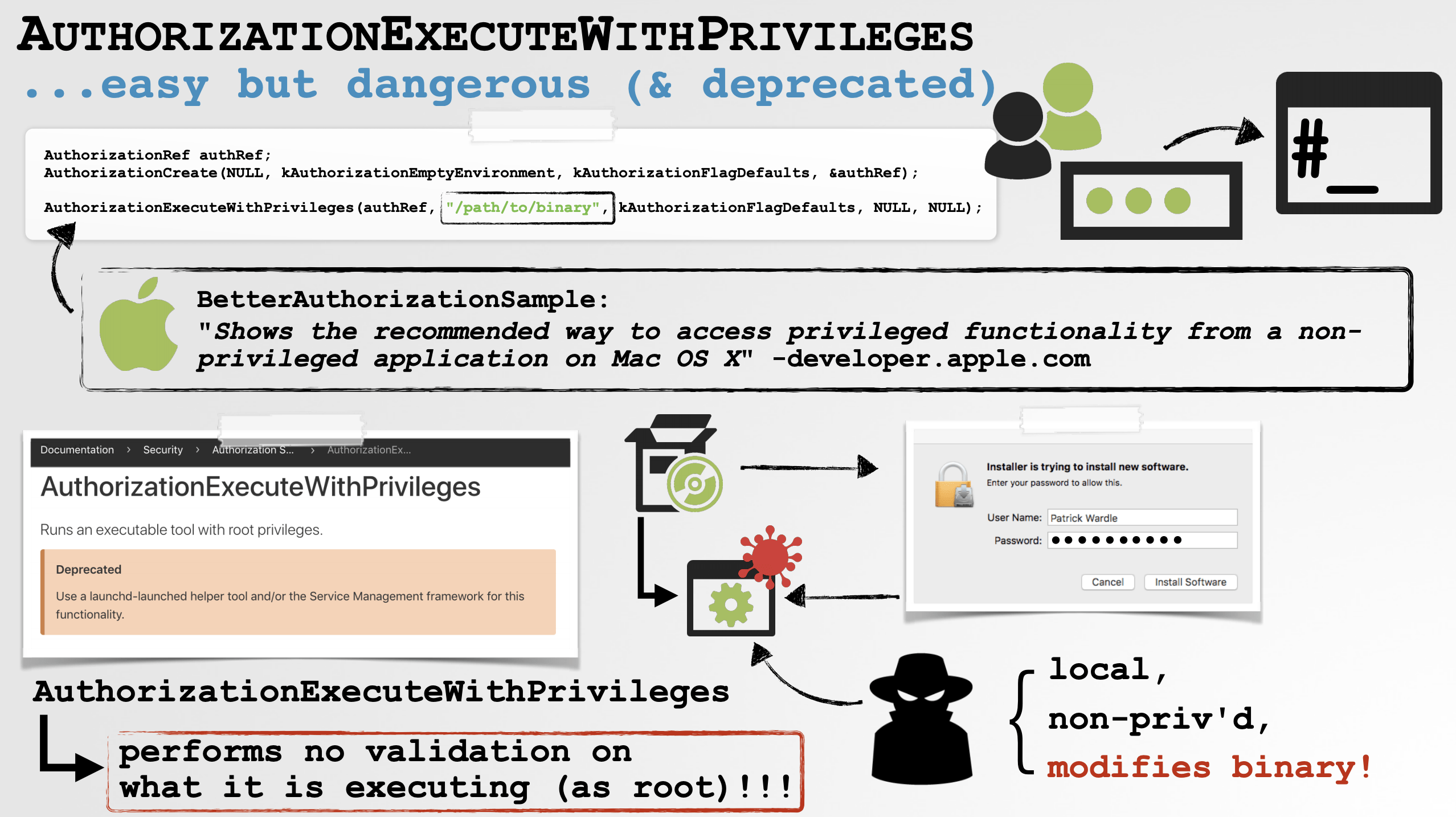
As experts recently explained, the easiest way to deploy such an attack is simply running a process monitor, execute the installer package and observe the arguments that are passed to the security_authtrampoline.
So far, no attacks have been detected in the wild, although this could be a matter of time.
These are critical security issues for any Zoom for macOS user. These are complex times that threat actors, and even companies, could take advantage of to take questionable actions or even border on illegality. The International Institute of Cyber Security (IICS) recommends that users consider the possibility of stopping using this platform, if they are really concerned about their privacy; for the time being, avoiding the use of Zoom may be the only way to avoid these invasive practices.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











