Social media users have always been exposed to malicious campaigns. This time, specialists in GDPR training report the appearance of a hidden virus variant in Facebook Messenger voice messages. This is part of a campaign to distribute Trojans and other types of malware via supposed voice messages sent to users of this messaging platform. It is mentioned that threat actors have already infected users all over the world.
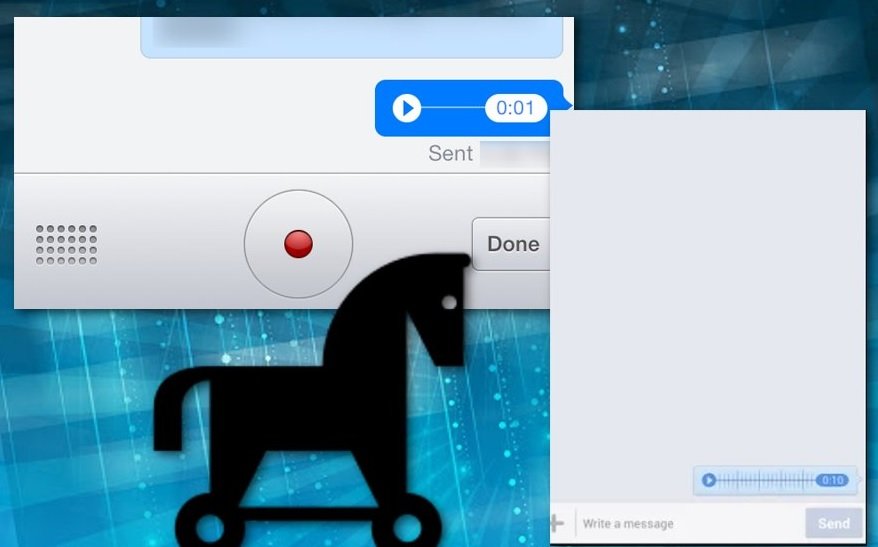
GDPR training specialists warn users about the possibility of receiving this voice message virus from a hacked or fake Facebook Messenger account. While the message does not trigger the malware installation by itself, it could redirect the user to other websites, controlled by threat actors and infested with computer threats such as Trojans, ransomware, cryptocurrency mining software and adware.
This could be a highly severe security threat, as users would never imagine that a voice note received via Facebook Messenger may contain malware or a malicious link. Also, in the worst cases, the malware could run directly by pressing the received voice message.
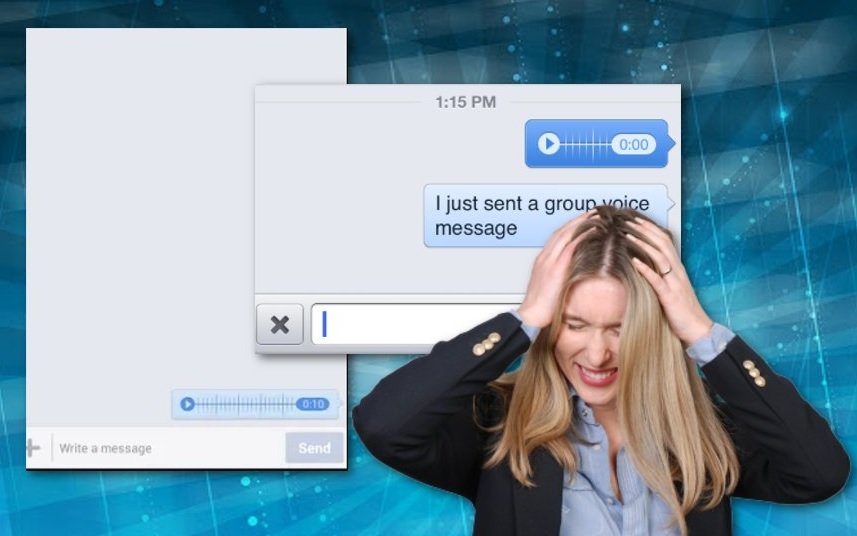
Sending messages to individual users is not the only attack vector used by threat actors. Experts in GDPR training point out that cybercriminals could also post across multiple groups, tag hundreds of users, and redirect them to external sites.
According to the International Institute of Cyber Security (IICS), this type of infection can go completely unnoticed by users with little knowledge of cybersecurity, so they won’t detect anything abnormal until the infection is complete. In addition, this malware variant has been shown to be able to disable antimalware systems on mobile devices, so the risk increases.
On the other hand, users with greater knowledge can detect signs such as increased device resource consumption, appearance of unknown application icons, or unidentified processes in the task controller. So far the company has not spoken out about it.
By prevention, Facebook Messenger users are advised to ignore any messages sent by an unknown user, in addition to ignoring suspicious posts. Not clicking on links to third-party sites is also a recommended option.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











