A team from a security testing course has revealed a persistent security flaw that could compromise deployments of popular cached distributed data storage software (popularly known as “Memcached“).
This is a buffer overflow vulnerability in the binary protocol header in Memcached versions 1.6.0 and 1.6.1 that could be exploited to cause the compromised software to collapse. Project developers were not alerted prior to the public disclosure of the flaw.
In this regard, one of Memcached maintainers revealed that the vulnerability was corrected just hours before the disclosure of its existence. In addition, users of affected deployments can now find the updated version (1.6.2) on their official platforms.
Instructors from the security testing course mentioned that the flaw exists due to a missing check on the extlen parameter during a call to the mamcpy () function.
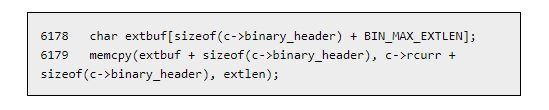
If threat actors could make the extlen extension larger, buffer overflow would be triggered to paralyze the software completely; experts suggest that this could also lead to remote code execution, although it has not been proven.
The developers of the project even took their time to criticize the decision of security testing course specialists who decided to disclose this flaw (announcing it as a zero-day vulnerability) without previously notifying them. It should be remembered that the cybersecurity community establishes a private notification period to developers of a vulnerable project prior to public disclosure of errors.
The International Institute of Cyber Security (IICS) reminds administrators of affected deployments to update as soon as possible, and advise against exposing Memcached on the Internet as an additional security measure.
Unfortunately this is a common practice, as it is estimated that there are currently tens of thousands of servers running Memcached exposed through port 11211. In a superficial analysis with Shodan, specialists found at least 83,000 systems exposed by the port, a poor safety practice.
It is not known how many of these deployments are vulnerable, although one reference that could help in this calculation is that the flaw was introduced with the release of version 1.6.0, so administrators of this release, and later 1.6.1, are recommended, update as soon as possible.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











