Introduction
Maryam framework tool is an OSINT (open source investigation) tool. Mostly this tool is used for web application penetration testing to recon the information about the web application. This Maryam tool is built in the python programming language. It is easy to understand and every penetration tester can use this tool for collecting the best information about target.
Environment
- OS: Kali Linux 2019.3 64 bit
- Kernel version: 5.2.0
Installation steps
- Use this command to clone the tool git clone https://github.com/saeeddhqan/Maryam.
root@kali:/home/iicybersecurity# git clone https://github.com/saeeddhqan/Maryam Cloning into 'Maryam'... remote: Enumerating objects: 188, done. remote: Counting objects: 100% (188/188), done. remote: Compressing objects: 100% (119/119), done. remote: Total 263 (delta 100), reused 115 (delta 64), pack-reused 75 Receiving objects: 100% (263/263), 261.68 KiB | 492.00 KiB/s, done. Resolving deltas: 100% (126/126), done.
- Use cd command to enter into the Maryam directory.
root@kali:/home/iicybersecurity# cd Maryam/ root@kali:/home/iicybersecurity/Maryam#
Tool Execution
- Use command ./Maryam. To lunch the tool.
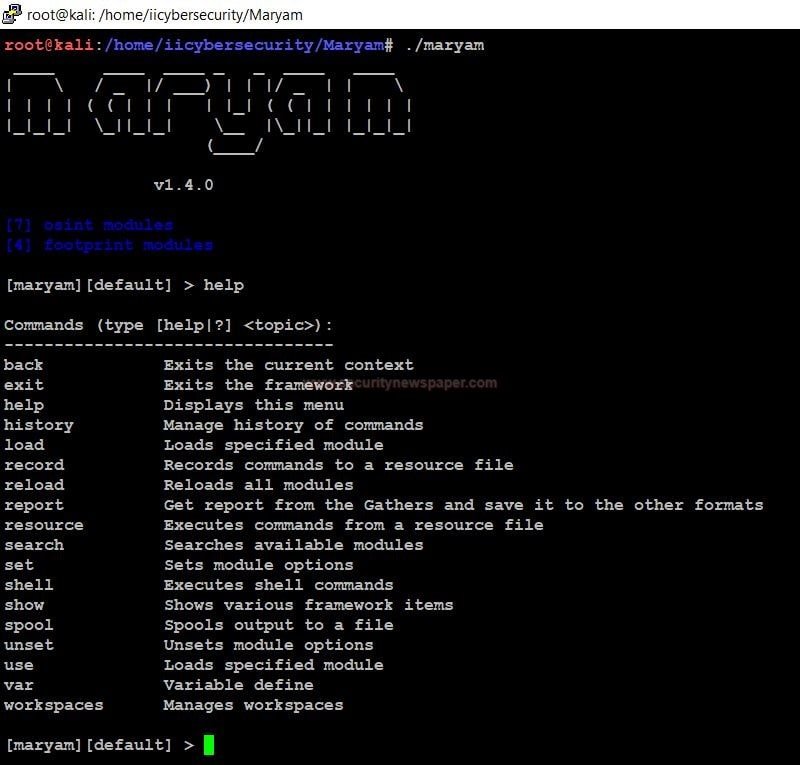
- Use command help, to view the all help option in the tool
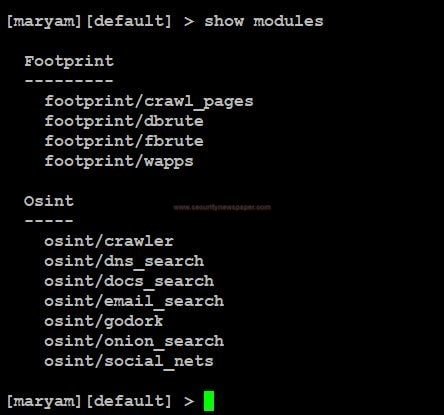
- Next, use command show modules. To view all the modules in the tool
- In this tool, we have two types of modules
- Footprint
- OSINT
- When we use the above command to see modules and it’s sub-classifications
Fingerprint Module
- Fingerprint module is used to collect information about any domain.
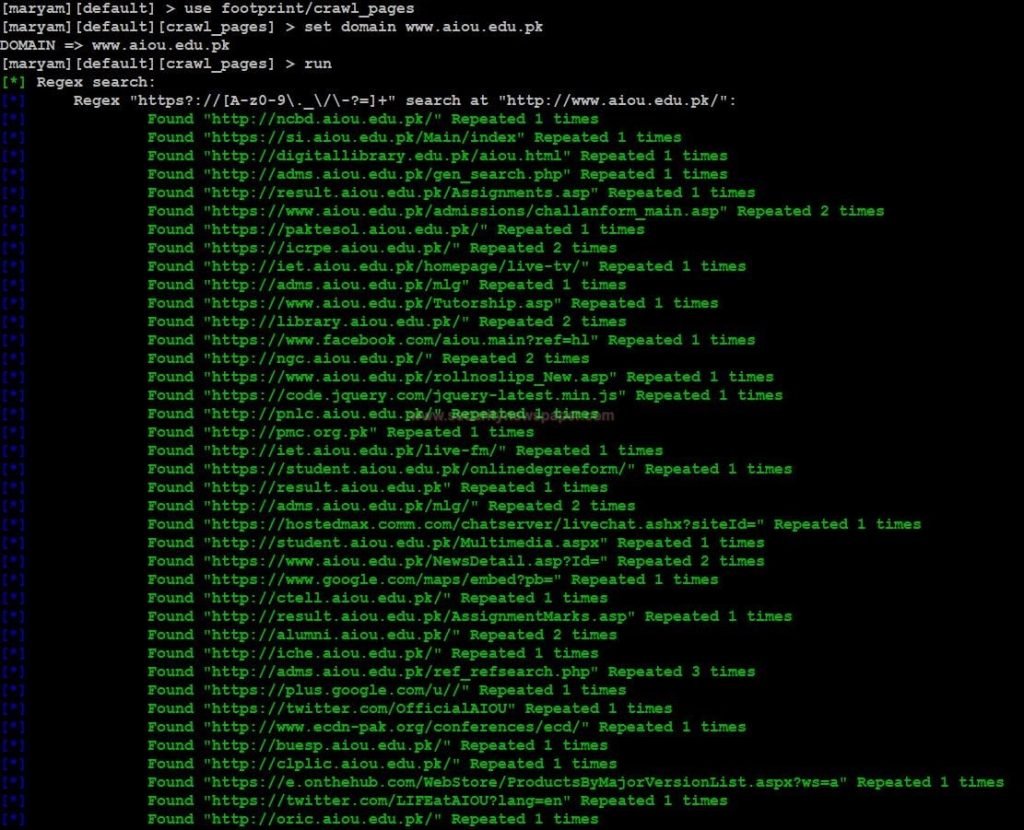
Crawl Pages Module
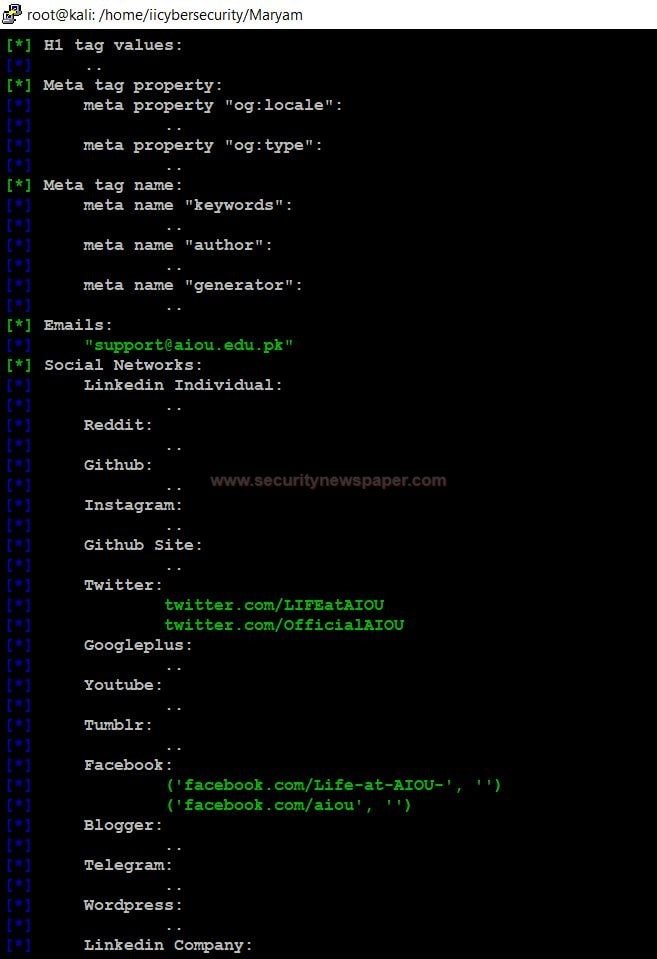
This module is used to crawl details about a particular website. In the results, we see all the URLs about the domain, Emails and social network details in this.
- Commands to set the module and execute
- Use this command to set the module Use footprint/crawl_pages
- Enter show options, to view requirements for executing the module
- Use <set option name > to change any option in the module.
- Use the run command to execute the module.
WAPPS Module
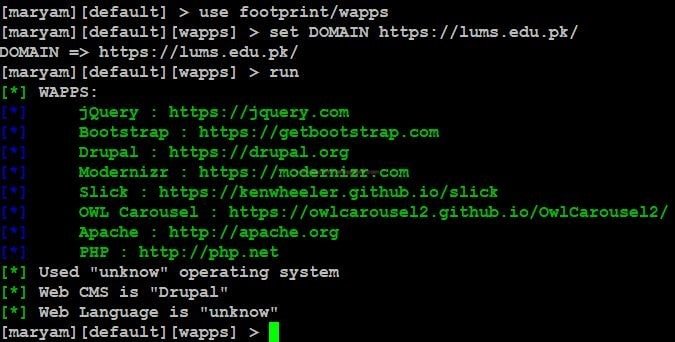
This wapps is tool that collects the details about website built-up.
- Commands to execute the module
- Use this command to set the module use footprint/Wapps
- Enter show options, to view requirements for executing the module
- Use <set option name> to change any option in the module.
- Use the run command to execute the module.
- If any website is built on some specific framework, then using static analysis of code we can find issues in web application, as commented by ethical hacking researcher of International Institute of Cyber Security.
Fbrute Module
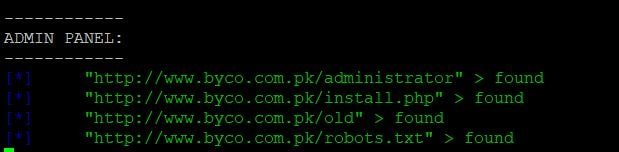
This Fbrute modules check in all types of modes like General, PHPINFO File, Log files, Apache status and, admin panel.
- Commands to set the module and execute
- Use this command to set the module use footprint/fbrute
- Enter show options, to view requirements for executing the module
- Use <set option name > to change any option in the module.
- Use the run command to execute the module.
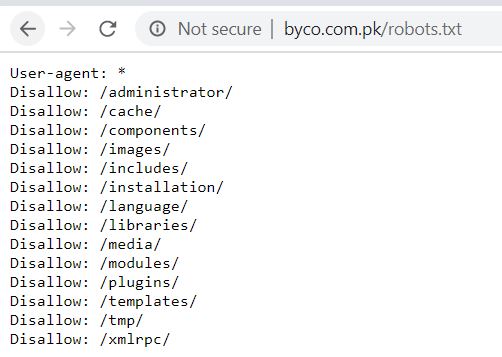
- Now, lets open any URL in the browser and check whether we can find any data
OSINT Module
OSINT is also called an open-source investigation. This is used to collect the details, which are publicly available on the internet.
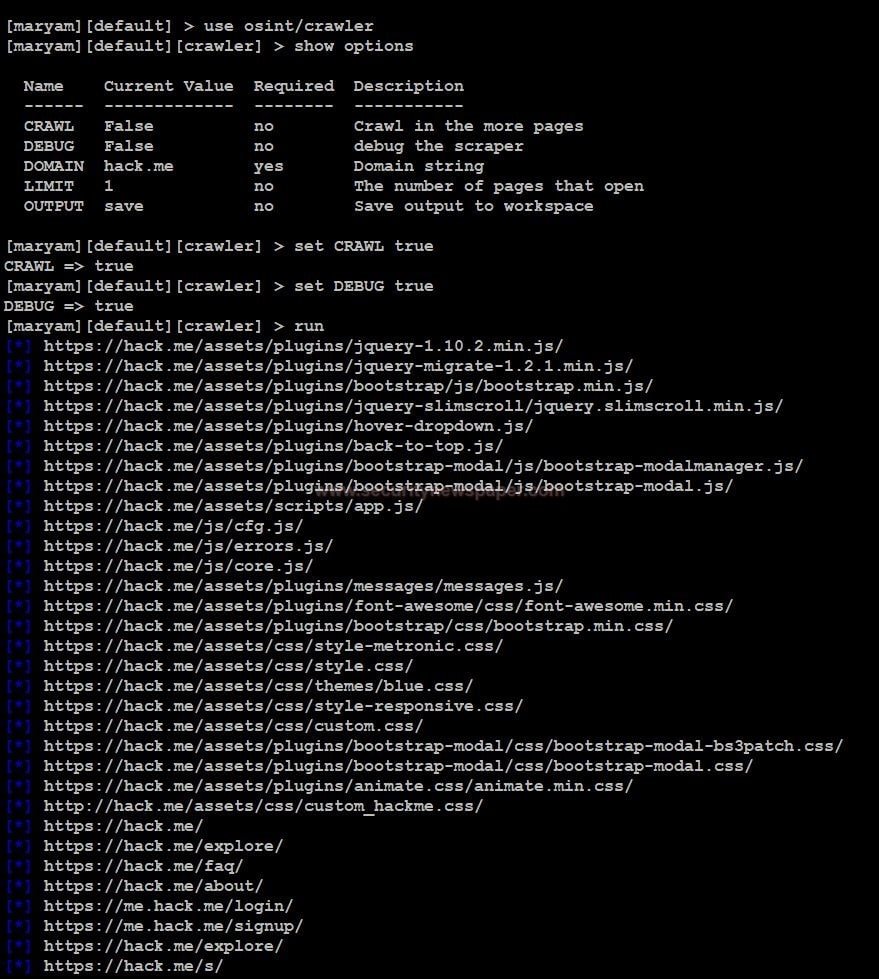
Crawler module
The crawler module is used to collect the URLs of the domain.
- Commands to execute the module.
- Use this command to set the module use osint/crawler
- Enter show options, to view requirements for executing the module
- Use <set option name > to change any option in the module.
- Use the run command to execute the module.
Email Module
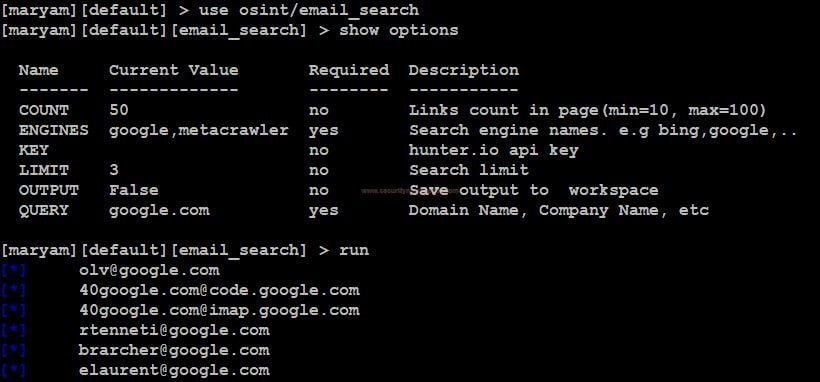
This module collects the list of email of a domain.
- Commands to execute the module.
- Use this command to set the module Use osint/email_search.
- Enter show options, to view requirements for executing the module
- Use <set option name > to change any option in the module.
- Use the run command to execute the module.
- These email address can further be used for social engineering attacks.
Social Nets
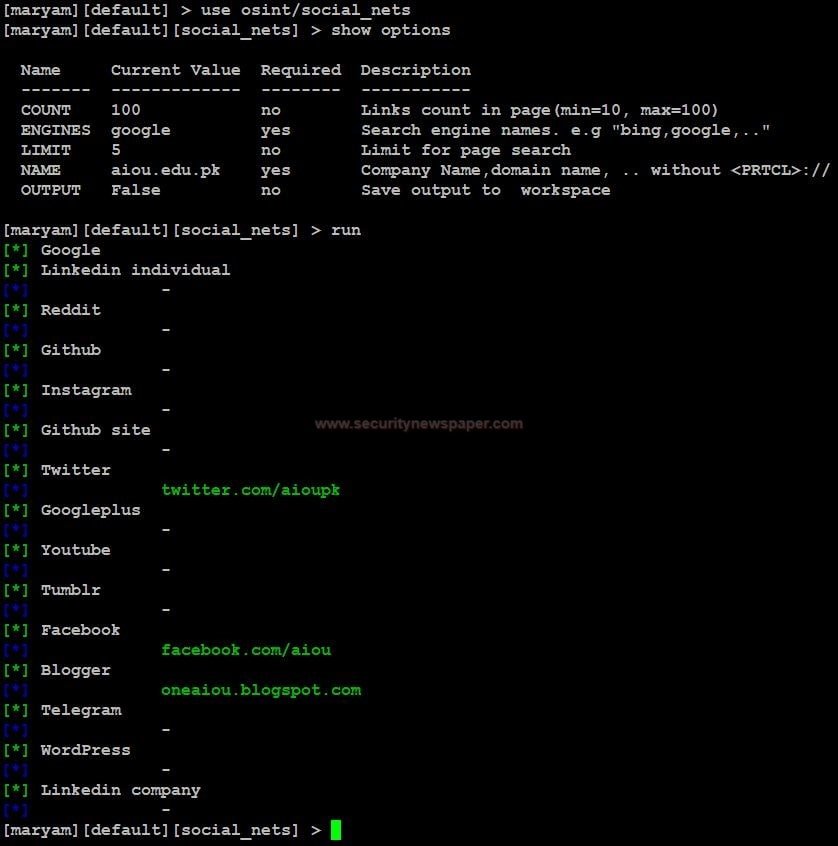
The social nets module is used to collect URLs about a domain in social media applications.
- Commands to execute the module.
- Use this command to set the module Use osint/social_nets
- Enter show options, to view requirements for executing the module
- Use <set option name > to change any option in the module.
- Use the run command to execute the module.
Conclusion
This is a good tool to collect information about any web application. Most of the penetration testers can used this for first phase of pentesting.

Cyber Security Specialist with 18+ years of industry experience . Worked on the projects with AT&T, Citrix, Google, Conexant, IPolicy Networks (Tech Mahindra) and HFCL. Constantly keeping world update on the happening in Cyber Security Area.











