Researchers from a cyber security course have revealed the discovery of a dangerous new hacking tool. Identified as Raccoon, this is a powerful malware specifically developed for the theft of personal information, including login credentials, banking keys, cryptocurrency addresses, among others.
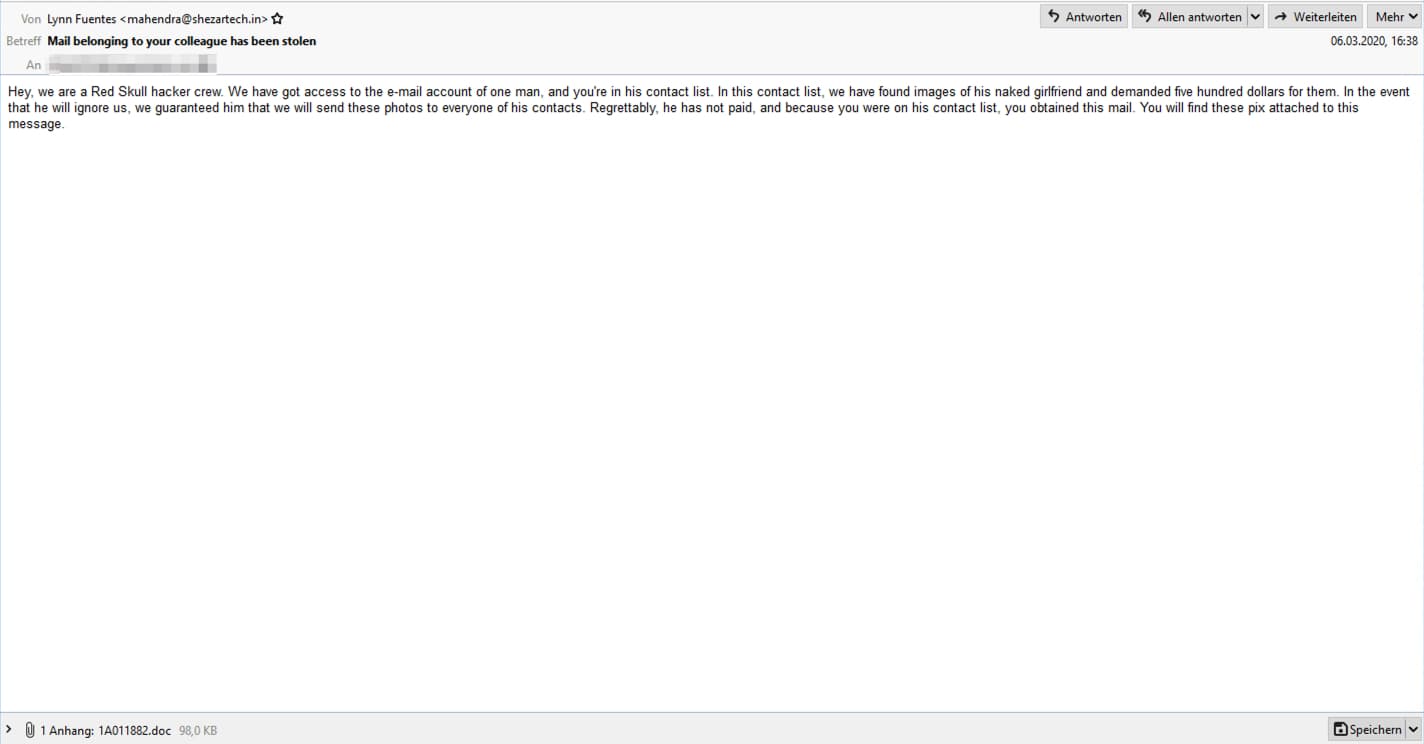
According to reports, threat actors deliver Raccoon’s malicious payloads through a sextortion campaign. Hackers send Outlook emails to unsuspecting users assuring them that they have intimate photos of friends or colleagues.
Threat actors assure the victim that the message was sent by the cybercriminal group Red Skull Hacker Crew, who possess intimate photos of someone related to a contact of the victim (a girlfriend, usually). In addition, hackers report that the user did not pay a ransom of 500 dollars, so they will be sending the photos to all contacts. “Unfortunately, he did not pay. Because you were on his contact list, you got this email. You will find the intimate photos attached to this message,” the email says.
According to the experts of the cyber security course, cybercriminals found an efficient way for users to fall into the trap. After interacting with the alleged attachments, it initiates the infection of the victim’s device.
In addition, the researchers revealed some titles or email issues linked to Raccoon infections, including:
- “Your colleague’s mail has been stolen”
- “Your colleague’s account has been compromised”
- “We have access to your friend’s account”
- “Private information belonging to your friend has been stolen”
If the victim opens the attachment, he encounters some blurry images. A message then appears asking the user to enable the content to view the images.
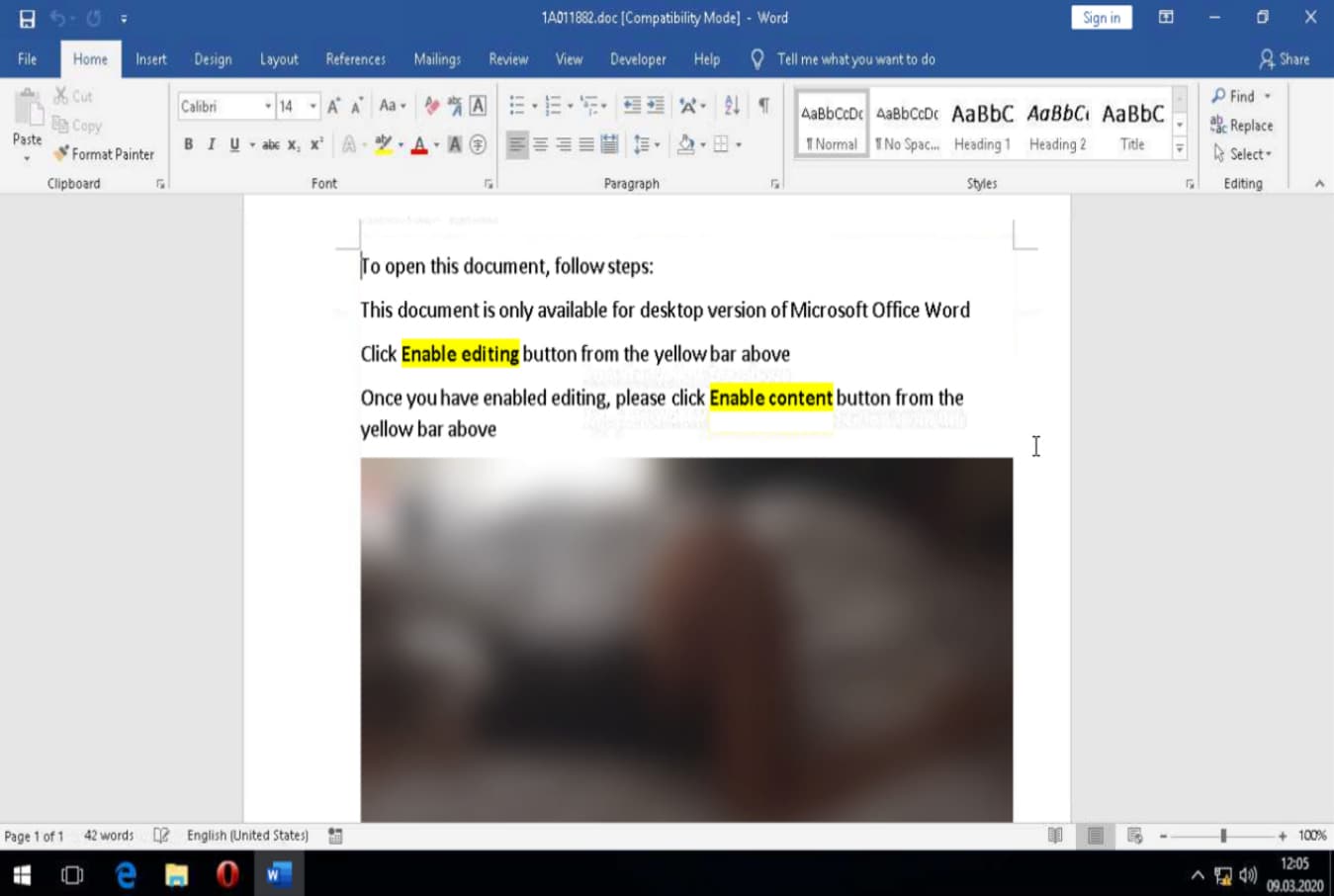
Experts in the cyber security course mention that these attachments are loaded with Raccoon malware, which immediately begins to infest the target system with embedded macros; these macros then trigger a PowerShell command that completes the Raccoon installation.
In this regard, the International Institute of Cyber Security (IICS) mentions that the domain from which the hackers operated has already been removed, although it is highly likely that this group of threat actors will retake their malicious activities as soon as possible, Raccoon proved capable of deploying quickly.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











