Apple often boasts about the level of data protection and security of its devices. While the cybersecurity community recognizes the firm’s efforts and its superiority in encryption and privacy over its counterparts, the firm is not completely safe from security flaws. A team of researchers has reported the finding of a vulnerability that allows the interception of personal data stored on various iPhone or iPad models.
When a user copies any information, it is stored on Apple‘s general pasteboard (usually known as a clipboard). According to the report, any application can access this information temporarily stored on the clipboard, so users are exposed to the leaking of sensitive data such as location, online profile access passwords, and banking details.
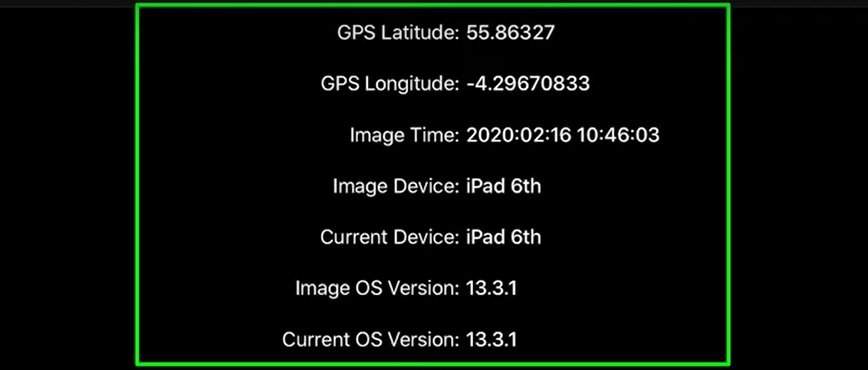
Apparently, all iOS apps have unlimited access to the general clipboard. A user could unintentionally expose their sensitive information (such as location data) to other apps by simply copying/pasting a photo taken with the device’s camera, thanks to the image metadata, mentioned by data protection specialists.
To prove their finding, the researchers developed a proof-of-concept app called KlipboardSpy and an iOS widget called KlipSpyWidget. This test app does not have access to the target device’s location data; however, the specialists were able to extract this information using the method described above.

Specialists say the report was sent to Apple from last January. However, the company’s data protection team responded that this error could not be considered a serious vulnerability, as its operating systems are designed to allow any application to access the clipboard only when apps are working in the foreground.
In this regard, the International Institute of Cyber Security (IICS) believes that Apple should not allow apps to access the clipboard without restriction, such as the express consent of the user. The operating system should only expose the contents of the clipboard to an application by prior confirmation, as sometimes users are not aware of the contents of this tool.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.










