Malicious hackers keep showing their ability to evolve and diversify. A digital forensics investigation revealed that the creators of a massive botnet are using a picture of the famous singer Taylor Swift loaded with malware that integrates the affected systems into the massive network, used for cryptocurrency mining.
The botnet in question is known as MyKingz, also called Smominru, DarkCloud or Hexmen, according to the security firm that elaborates the report, so the activities of its operators are widely documented.
Since its inception, MyKingz has shown unused growth; just a few months after the first reports, the developers of this botnet had already infected more than 520k Windows systems, generating more than $2 million USD in Monero cryptocurrency in less than a year.
Threat actors abuse the EternalBlue vulnerability, so the botnet is able to reach the innards of any corporate network. As if that weren’t enough, initial estimates of just over a million infected systems have been left behind as experts estimate that the number of infections already exceeds two million devices.
Although some reports claimed that the creators of the botnet stopped operating it, new signs of activity began to be recorded a few months later, detecting up to 4,000 new infections a day.
According to a report by digital forensics firm Sophos, hackers devised a new way to infect devices to integrate them into the botnet. Employing steganography, threat actors hide malicious files inside legitimate ones, in this case a malicious EXE is hidden in a JPEG image of the famous pop singer Taylor Swift.
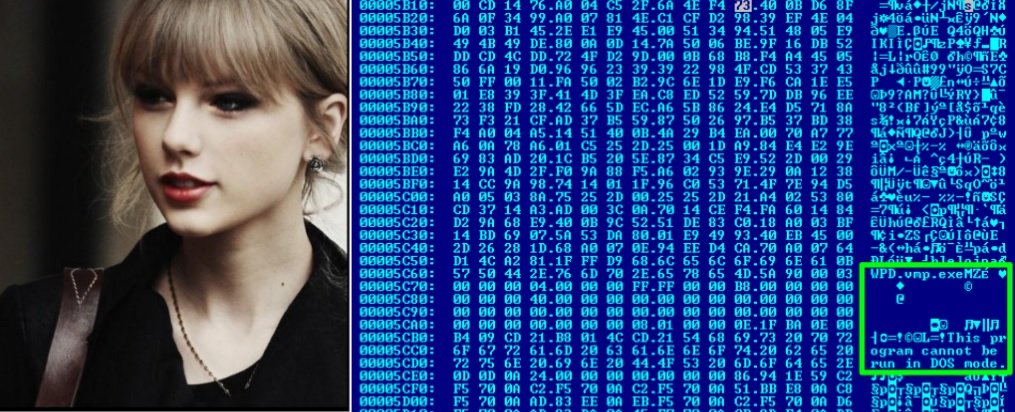
SOURCE: Sophos
This way, the hackers seek to trick the antivirus software on the target system, which only identifies the JPEG file that is being downloaded, completely bypassing the detection of the malware.
This is not the first time a hacker group uses steganography to infect thousands of victims. A couple of years ago, digital forensics experts reported that a group of cybercriminals distributed malware hidden in an image of actress Scarlett Johansson. It should be noted that steganography is not limited to the use of images loaded with malicious code. In recent months, some groups of cybercriminals have experienced new uses for this technique, trying to hide malware in PDF documents or even WAV audio files, many times successfully.
For a couple of years now this botnet has become one of the main threats to computers with Windows operating system, as mentioned by reports of various firms, it is sufficient that a system is outdated or leaves some ports uncovered to complete the infection.
According to the digital forensics specialists from the International Institute of Cyber Security (IICS) the developers of this botnet earn about $300 USD a day, and it is estimated that in total some 9,000 Monero units have been generated, equivalent to $3 million USD, according to the current exchange rate.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











