Despite some of them have advanced security measures, cryptocurrency exchange platforms remain one of the hackers’ favorite targets. As reported by digital forensics specialists, Upbit, a South Korean-based crypto exchange platform, has been the victim of a cyberattack that led to the theft of 342k Ethereum units, equivalent to $48.5M USD at current exchange rate.
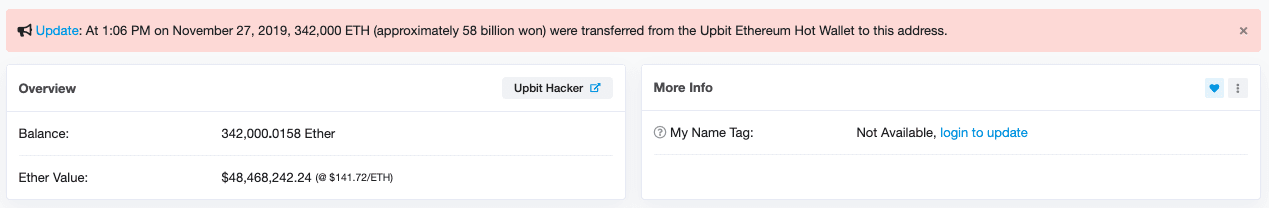
Rumors about the incident began circulating on Tuesday’s early hours; a couple of hours later, Lee Seok-woo, CEO of Upbit, confirmed the theft via a statement posted on the platform’s website: “Around 13:06 (local time) this Tuesday, November 27, were transferred 342,000 ETH from the Upbit Ethereum hot wallet (term referring to an Internet-connected cryptocurrency wallet) to an unknown address,” the statement says.
The Upbit website also shows a screenshot with the address to which the assets were transferred; so far those responsible for the attack have not made any operation in this online wallet, experts in digital forensics say. (photo)
SOURCE: TheNextWeb
The exchange platform ensures that any Ethereum replacements arising from this incident will be funded, so affected users must remain in communication with the company to learn about their digital assets recovery process.
As a security measure, Upbit digital forensics team mentioned that all platform assets have been transferred to their cold wallets (a term used to refer to cryptocurrency wallets that are not connected to the Internet, so they are safe from cyberattacks) at least until they can ensure that the threat has been eliminated.
It is important to note that, while a hot wallet is a software-based virtual asset storage implementation (usually through mobile apps or computer programs), cold wallets are hardware-based implementations, so they can be maintained offline while not being used, so a threat actor would require physical access to these resources to try to steal them.
The investigation will remain ongoing for at least the next two weeks. In the meantime, all operations on Upbit are suspended. The platform strongly asks its users to refrain from sending cryptocurrencies until further notice.
A few days ago, digital forensics specialists at the International Institute of Cyber Security (IICS) reported a cybersecurity incident related to the Monero cryptocurrency. One user noticed that when downloading a 64-bit Linux binary to work with this virtual currency, the SHA256 hash did not match the one displayed on the official website. After an internal investigation, the team behind Monero determined that the file had been altered by a malicious user with the intention of stealing some units from the virtual asset.
As a security measure, the platform recommended to its users who downloaded this file to verify the hashes of the binary, in addition to deleting them and downloading them again in case of detecting any anomalies. Although the incident was detected in time, there appear to have been cryptocurrency thefts arising from this incident, although until now Monero has not revealed further details.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.










