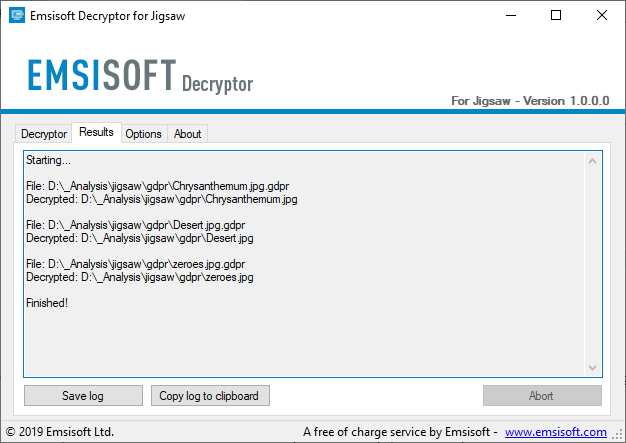
These are excellent news for ransomware victims. Specialists in ethical hacking of security firm Emsisoft have just announced the launch of a new tool to remove the encryption imposed by the ransomware variant known as Jigsaw.
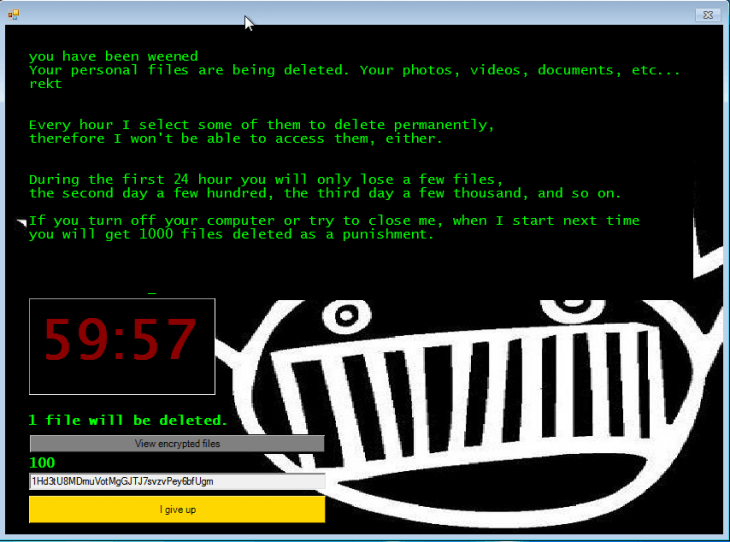
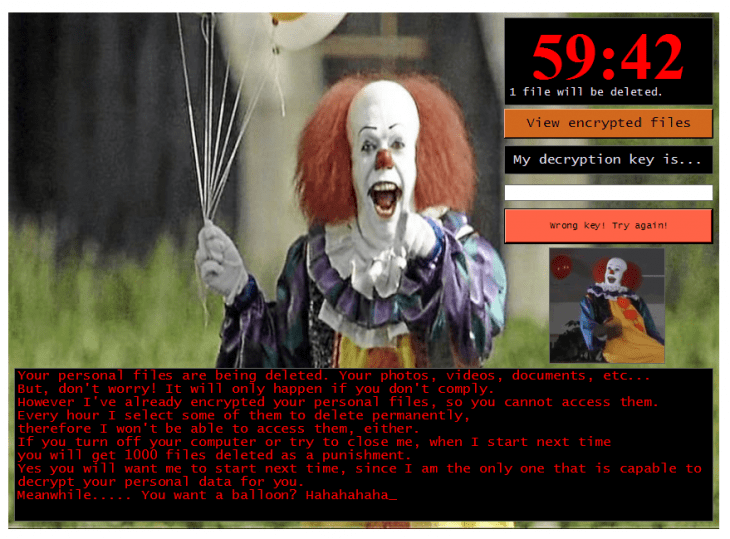
Like any other ransomware strains, Jigsaw encrypts the victims’ files, although it includes other features that make it unique. After encrypting the files, Jigsaw displays a countdown in users’ screen; after an hour, the ransomware begins to delete files randomly, starting with one but increasing the figure as the clock progresses.
In cases of Jigsaw infection detected, 72 hours after infection, all the victim’s files are deleted, in addition, the hackers display a message threatening the victim with deleting a thousand files as punishment if the infected computer is restarted or if victims try to stop the Jigsaw process, ethical hacking specialists mention.
In 2016, shortly after the Jigsaw outbreak began, a decryption tool was released; however, the malware developers turned it into an open source tool, allowing the creation of multiple new versions of the ransomware, impossible to decipher with the original tool.
The good news is that this new version of the tool released by Emsisoft is able to remove the encryption of 85 extensions used by Jigsaw; in addition it will be constantly updated to address new versions of the malware. Best of all, you don’t need advanced knowledge to run the decryption tool (available here). Jigsaw victims should simply run the tool while they are online for the encryption removal process to begin.
According to the International Institute of Cyber Security (IICS) ethical hacking specialists, the original Jigsaw variant displayed an image of “Billy the Puppet”, a character from the film Saw. When new variants of the ransomware were developed, new graphical user interfaces (GUI) appeared, although the operation of the encryption malware remained the same. The ransom notes sent in each infection were also quite similar.
SOURCE: EMSISOFT
No matter what variant of Jigsaw you are dealing with, Emsisoft specialists claim that your tool is truly functional, so victims will be able to recover their files without negotiating with the criminals.
Before you begin the recovery process, remember to perform the following steps:
- Open Task Manager
- On the Processes tab, select firefox.exe and drpbx.exe and click “Finish Task”
- When finished, open MSConfig
- On the Home tab, deselect the firefox.exe startup item that points to %UserProfile%\AppData\Roaming\Frfx\firefox.exe and click OK
Now you can run the tool smoothly and retrieve your information.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











