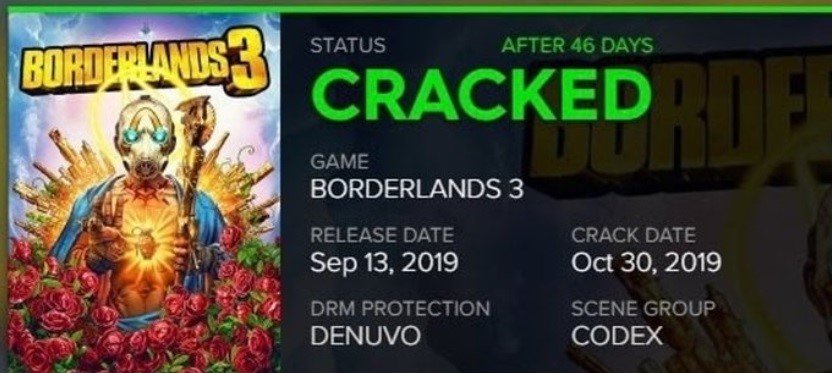
Even the most sophisticated security measures cannot guarantee the integrity of multiple IT developments, including video games. According to web application security experts, the hacker group known as CODEX has managed to crack the latest version of Denuvo, the Digital Rights Management (DRM) protection system used in multiple video games, including Borderlands 3, barely a month after its release.
Denuvo is one of the main measures to protect against videogame cracking. This is not an additional software, but is installed directly in the code of some video games, so it runs as one of the elements of the game.
According to web application security experts, in theory this is an approach that gives the game greater protection against hackers using reverse engineering techniques, although in reality this is not the first time that a recent version of Denuvo is hacked shortly after its release.
Hackers posted their achievement on various forums, although they did not specify whether other video games using the latest version of Denuvo will also be released. The most recent time a version of this protection system was released, this was hacked a week after its release. Although those responsible for hacking the last version of this system claimed that it was obsolete, some video games that use it, such as Mortal Kombat 11 or Anno 1800 are still protected.
Since the protection system has been disabled, Borderlands 3 developers and editors are likely to remove Denuvo from the game code, although they haven’t commented on it yet.
Although Denuvo has demonstrated a better level of protection against the activities of video game hacker groups, web application security specialists at the International Institute of Cyber Security (IICS) claim that its implementation can also be detrimental to gamers, as their inclusion in a videogame requires an increase in the resources of the console, which generates lower performance (especially in graphical aspects of the game), increased load time and high latency.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











