A team of ethical hacking specialists from security firm Confiant has revealed the discovery of a new malware variant for Mac devices. Dubbed Tarmac, this strain is distributed through some malicious advertising campaigns in countries such as the US, Japan and Italy.
In their report, the researchers mention that it all starts using malicious advertising, which redirects the victim to an infested pop-up site offering commonly used software updates (Adobe Flash Player, for example). When the victim downloads and runs these alleged updates, the MacOS OSX/Shlayer malware is installed, which will eventually run the OSX/Tarmac payload.
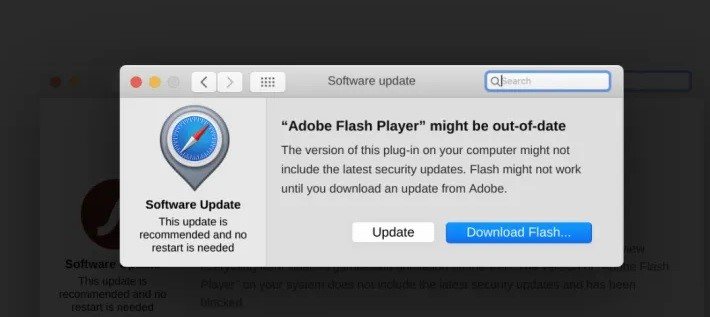
“This is obviously a fake Adobe installation signed with an Apple developer certificate (2L27TJZBZM). This certificate was issued by Fajar Budiarto, a fake entity,” the ethical hacking experts added.
This campaign was detected since January 2019, although at that time researchers had not detected Tarmac’s malicious code. It is very common for malware developers to sign their creations with Apple developer certificates, as it is easier than other methods and allows their code to bypass some of the most commonly used security implementations in a system, such as XProject or Gatekeeper.
In the report, experts note that the command and control (C&C) servers of the campaign operators were inactive at the time of the investigation, adding that the malware samples analyzed were somewhat old. However, it is likely that criminals have only changed infrastructure and this campaign will remain active.
The analyses were performed when the C&C servers were already down, so it was not possible for experts to know all the features of the malware. “We know that Tarmac collects information about the target system and send it to the hackers, although we don’t know which commands this malware supports,” the ethical hacking experts added.
Although it does not seem like an overly sophisticated tactic, experts from the International Institute of Cyber Security (IICS) claim that the use of malicious advertising and pop-ups remains highly effective for the distribution of this kind of malware. As a security measure, users are advised to avoid clicking on suspicious links that could redirect them to malicious pages.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











