The most frustrating part of being a cybercrime victim is the low chance of an attacker getting caught; however, malicious hackers don’t always get away with it without taking punishment. Ethical hacking experts report that a white hat hacker managed to take revenge on the cybercriminal group that encrypted his files, hacking their servers and releasing the decryption keys of the ransomware strain they used in their operations.
The incident is related to the Muhstik hacker group, which uses the ransomware variant of the same name to encrypt the files of its victims. According to reports, this group of hackers had been active for at least a couple of months.
Muhstik ransomware attacks are primarily targeted against the network-attached storage (NAS) devices of the Taiwan-based QNAP manufacturer. Campaign operators perform brute force attacks against these devices, which usually use weak passwords for the built-in phpMyAdmin service, as mentioned by ethical hacking experts.
After accessing phpMyAdmin, Muhstik encrypts the files and stores a copy of the decryption keys on the hacker’s Command and Control (C&C) server. Finally, the compromised files are added the extension .muhstik, the main indicator of compromise of this ransomware variant.
Tobias Frömel, a software developer from Germany was one of the many victims of Muhstik. Unable to regain access to his files by himself, the developer had to pay the ransom demanded by the hackers. However, Frömel did not stayed quiet, as long after paying the ransom, the ethical hacking expert began to analyze the malware variant used by hackers, which granted him some clues as to the mode of operation of this group for finally access the server database operated by hackers, discovering more than 2,800 keys to remove Muhstik encryption. “I know this isn’t exactly legal, but I’m not the bad guy of this story,” he mentioned on his blog.
Encryption keys are not the only finding of the expert, as he has also revealed a tool to remove encryption that all Muhstik victims can use to unlock access to their files. The tool is available for download in MEGA.
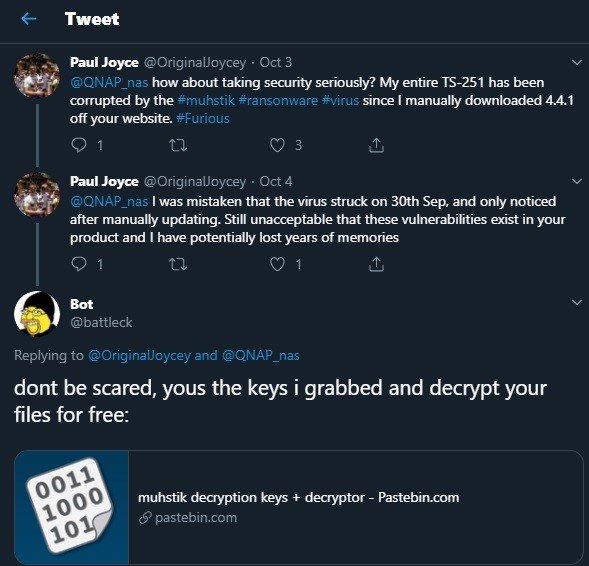
Through Twitter, Frömel has been notifying all possible Muhstik victims, trying to prevent them from paying a ransom to hackers. The specialized platform ZDNet published an interview with a Frömel collaborator, who claims that the expert also discovered important information about this hacker group, and mentioned that authorities have already been notified.
Muhstik is the third ransomware variant that attacks NAS devices discovered this year, along with the strain known as eCh0raix, for which a decryption tool already exists. Another unidentified ransomware variant is still active.
Although the actions of Frömel are considered illegal, the ethical hacking experts of the International Institute of Cyber Security (IICS) mention that the German authorities will most likely not press charges against them, as their discovery will help thousands of victims of this hacker group. However, the recommended procedure is to notify the authorities and not try to do justice in their own hands.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











