WhatsApp, a very popular mobile application used for chatting, sharing different types of files. It is estimated, as of 2018 WhatsApp has around 200 million users than Facebook Messenger. According to ethical hacking researcher of international institute of cyber security there are various types of attacks which are done on Whatsapp. It could be network level attacks or physical access of victim’s device. Thats why it is mostly targeted by attackers or spammers. We will show some basic steps to check if your whatsapp is hacked or not.
NOTE : Never Give Your Device To Any Unknown Person.
Methods To Check your WhatsApp :-
Using WhatsApp Web
- Whatsapp web is the popular feature which enables to use whatsapp on computer. Users can use Whatsapp on their computers web browsers. When user opens https://web.whatsapp.com/
- Everyone is familiar with screen below. Now, here attacker can make any social engineering method. That attacker will ask for your phone. It could be TO MAKE AN EMERGENCY CALL or it could be TO SEND IMPORTANT MESSAGE.
- Here attacker will try to distract your mind from your phone. In order to get access of your Whatsapp data. Attacker will open the options of WhatsApp Web.
- And Scans the QR code. To open whatsapp chat on computer.
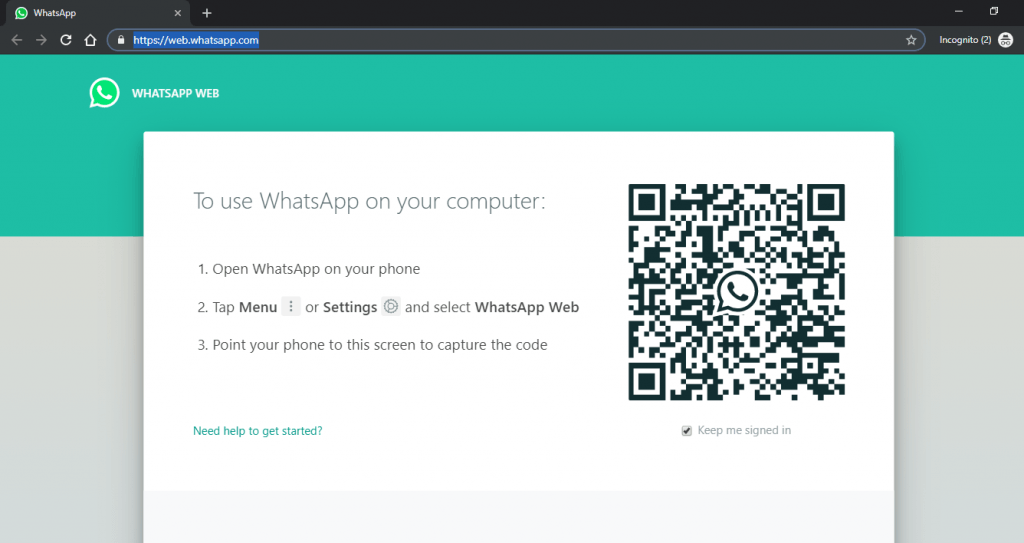
- The above QR is scanned & all your chat will now be able to see by the attacker as shown below.
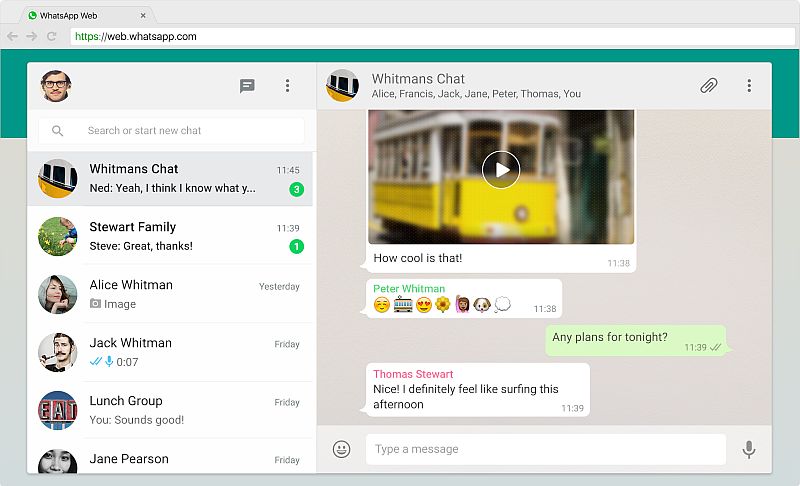
- Above screenshot shows all the whatsapp chat on attacker’s computer. For Checking if your whatsapp is not accessible to anyone. Always check whatsapp web active sessions. This can be seen from Setting -> WhatsApp Web options. See that no active session is running.
- Attacker to read all your Whatsapp Chat, and can even access all files which are shared using whatsapp.
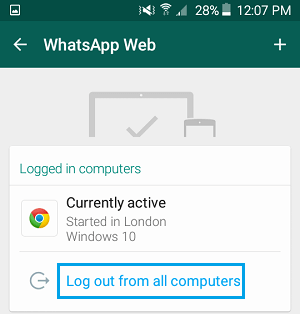
- Above wbatsapp shows that whatsapp web is currently active in Google Chrome Browser. Always remember to logout from whatsapp.
- According to Ethical Hacking researcher of International Institute of Cyber Security, it is easy to hack whatsapp of your friend
Thirty Party Spyware/ Key logger In Form Of Android apk Or IOS app
- Every day we often listen attack on operating system especially on mobiles. Attackers do create spy wares or key loggers to hijack the personal files including whatsapp data.
- In recent years, you can see malicious applications which are even available on Google Play Store or App Store. Such apps do spread malicious content which steals all memory like cache & cookies.
- Before installing any third party application. Remember to check permission what application is asking. Never give any permission which you don’t think is require.
- You should always check the application manager of your mobile that if any third party application is installed or not. Uninstall application that you don’t need.
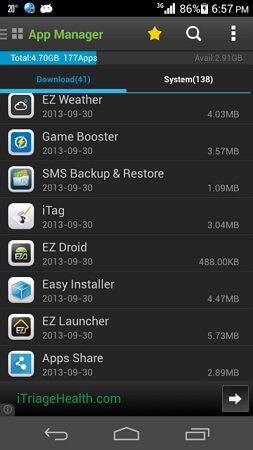
- If want to check any application is infected or not. You can visit : https://www.cyber.nj.gov/ and search for the app.
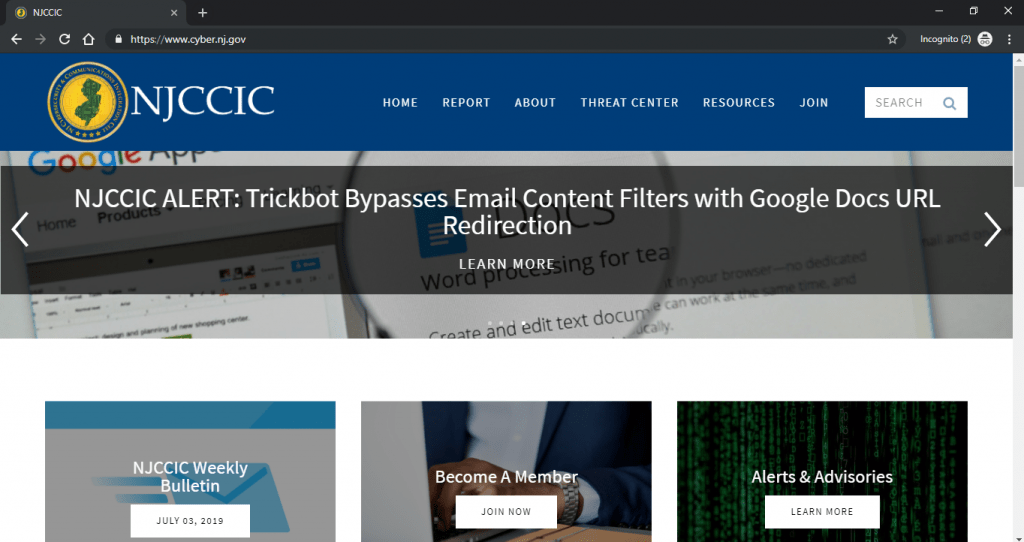
- This website holds the data of malicious applications which you should not install. Below you can see some of the list of android malicious applications.
Gustuff GPlayed Triout HeroRat MysteryRat ZooPark Super Clean Plus XLoader Desert Scorpion KevDroid SMSVova
- Website holds long list of malicious applications. You can check the list on their website. You can search for any application which your want to search. For Ex. – we have searched term SMS. It shows an malicious application with name SMSVova was used to send commands to the infected device.
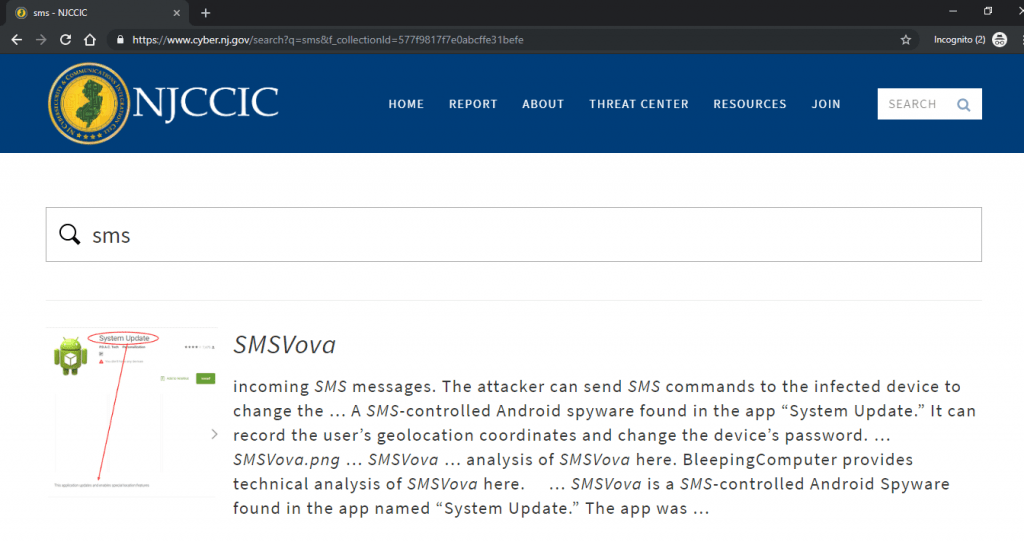
- Above you can see sms message application which vulnerable & you should not use.
Sharing Location On WhatsApp
- Everyone uses Google Maps for navigation. Well it makes our task easy. As it shows the shortest way to reach anywhere.
- But it sometimes makes our privacy at risk. If you mistakenly share your live location on whatsapp status. Attacker can might follow you & can even gather footprints by following with your live location. Only share your live location if you require.
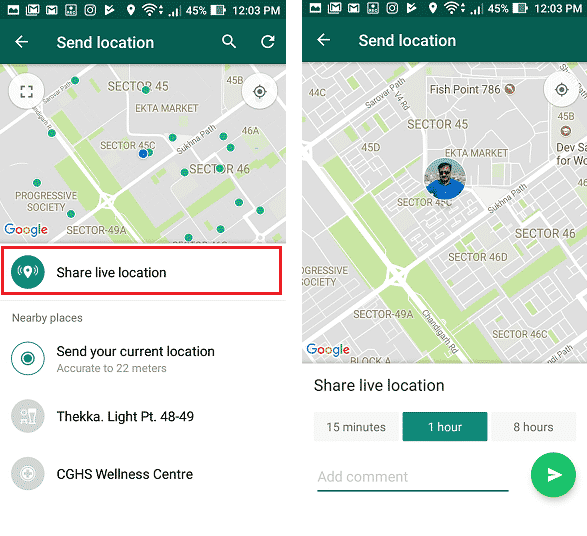
- In most smartphones, there is an inbuild feature of enable or disable GPS. Users should always enable GPS when it is requried.
- Otherwise consider it disabling. Because it saves from getting tracked from attacker.

Cyber Security Researcher. Information security specialist, currently working as risk infrastructure specialist & investigator. He is a cyber-security researcher with over 25 years of experience. He has served with the Intelligence Agency as a Senior Intelligence Officer. He has also worked with Google and Citrix in development of cyber security solutions. He has aided the government and many federal agencies in thwarting many cyber crimes. He has been writing for us in his free time since last 5 years.











