Windows is the most popular operating system. Because of its easy usability, easy to understanding its features. Most usage of this operating system makes it more vulnerable, according Ethical hacking researcher to International Institute of Cyber Security, Windows do have many vulnerabilities which makes an question if Windows is secure or not. Today we will show python script designed to find vulnerabilities.
WES-NG Windows Exploit Suggester is a tool based on Windows systeminfo utility. It provides list of vulnerabilities which includes exploits of Windows OS. All Windows version including Windows server versions is supported.
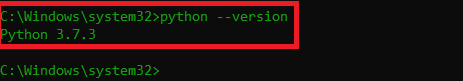
- For testing we will use Windows 10 1809 64 Bit. Make sure that Windows is configured with python3.
- For installing python go to : https://www.python.org/downloads/
- After downloading install python for all users. If the python path is not set automatically. Set path in Windows enviroment variables.
- Go to My computer properties < Advanced < Enviroment Variables < System Variables
- Click on New & in Variable type Path then enter Value C:\Program Files (x86)\Python37-32\Scripts\
- Type python –version
- After configuring the python. Download the WES-NG from : https://github.com/bitsadmin/wesng
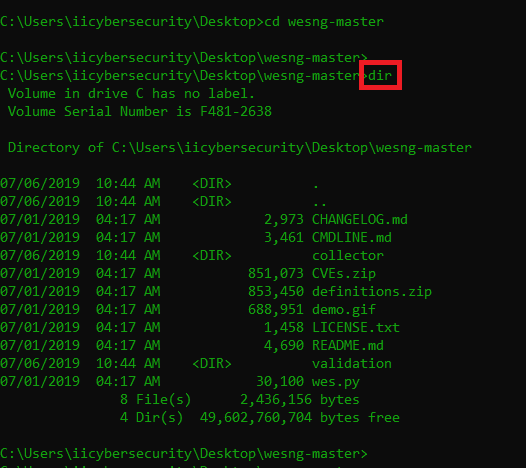
- After downloading, unzip the WES-NG. Then open CMD (Command Prompt) as administrator
- Go to location where you have download & unziped the WES-NG.
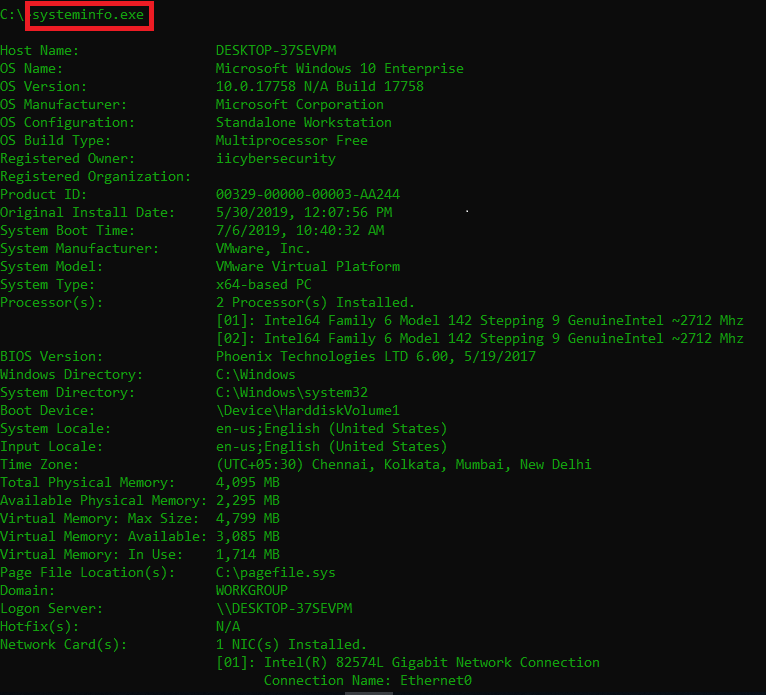
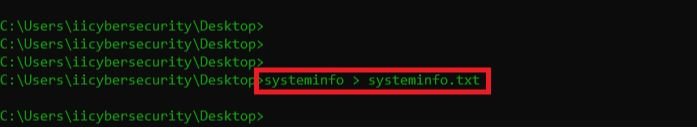
- Then open another cmd as adminstrator & gather system configuration. For that type systeminfo.exe
- Copy system info into text file. Type systeminfo > systeminfo.txt
- An new text file will be created. Copy the systeminfo.txt into wesng-master folder.
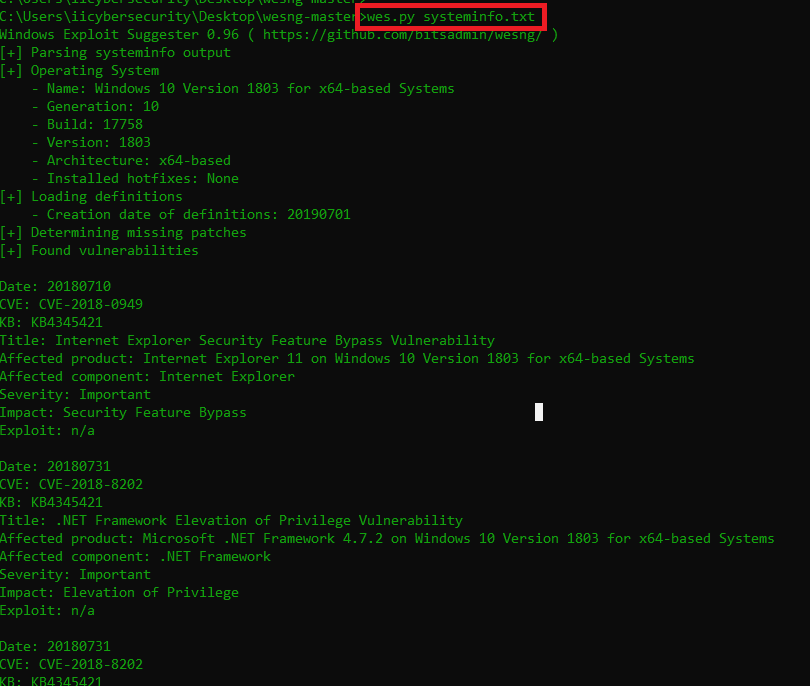
- Then execute wes.py systeminfo.txt
- Now wes-ng will start finding vulnerabilities on the basis of system information.
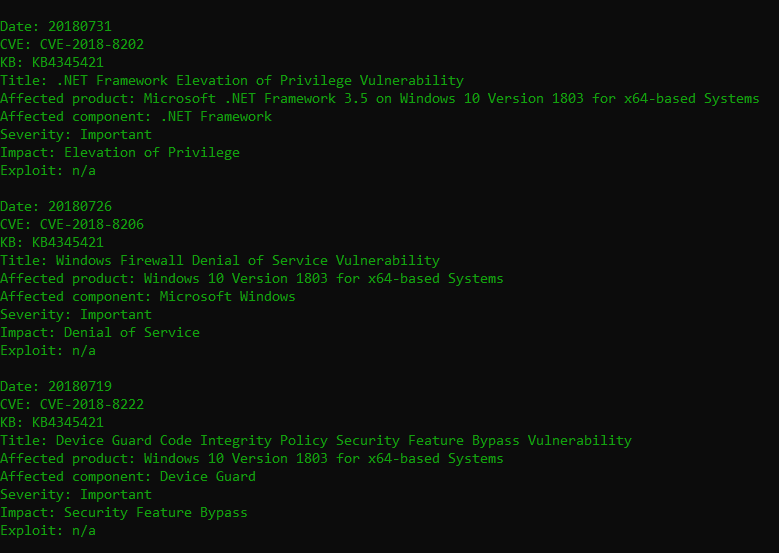
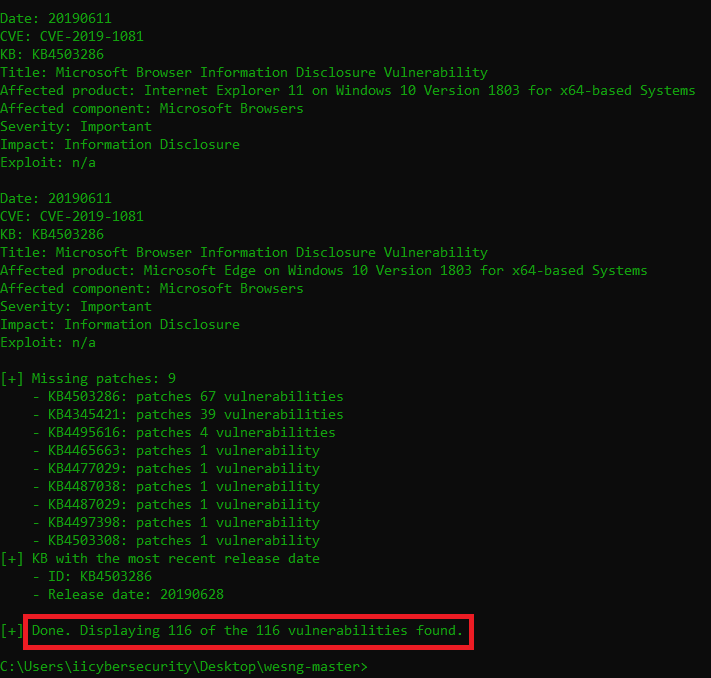
- Above screenshots shows 116 vulnerabilities of Windows 1809. We have posted some vulnerabilities to show how tool works. These type of tools are quite often used by Ethical hacking researcher.
- If you open any vulnerability for ex – we have open last CVE 2019-1081. As wes-ng finds vulnerabiltiy in CVE & exploitdb.
- Above shows the disclousure vulnerability in microsoft browsers improperly handle objects in memory.
- Wes-ng updates list of definitions from : https://raw.githubusercontent.com/bitsadmin/wesng/master/definitions.zip to show the list CVEs and exploits of given operating system.

Cyber Security Researcher. Information security specialist, currently working as risk infrastructure specialist & investigator. He is a cyber-security researcher with over 25 years of experience. He has served with the Intelligence Agency as a Senior Intelligence Officer. He has also worked with Google and Citrix in development of cyber security solutions. He has aided the government and many federal agencies in thwarting many cyber crimes. He has been writing for us in his free time since last 5 years.