Amazon implemented some improvements to Fire 7, one of its basic tablet models, including a new and faster processor and twice storage space than the previous model. However, information security specialists mention that some of its predecessor’s flaws have been inherited by Fire 7.
Although relatively inexpensive, the Fire 7 tablet is also easily hackable. In a minimum time span, multiple users and researchers discovered how to root the device, unlock the bootloader, uninstall updates and even install Google Play Store.
If you want to use Apple apps and services without rooting your smartphone, but if you also want to use the Google Play Store to run Google apps (such as Gmail, YouTube, etc.), there’s a way to do it. Information security experts say the same method that has been used for this purpose on Amazon tablets remains functional.
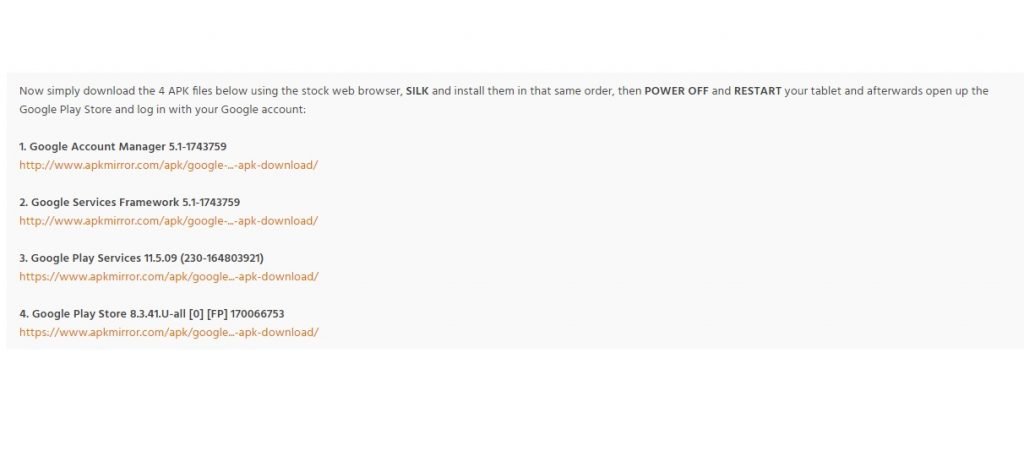
Simply put, all you need to do is dig a little bit into the tablet settings menu. In this section, you enable the installation of applications from unknown sources and download, in order, the following applications (available on multiple developer platforms):
- Google Account Manager 5.1-1743759
- Google Services Framework 5.1-1743759
- Google Play Services 11.5.09 (230-164803921)
- Google Play Store 11.5.09 (230-164803921)
Information security specialists also unveiled a couple of new methods for rooting the latest version of the Fire 7 tablet. The first of these methods requires a slight modification to the tablet hardware, as it is necessary to open the device and cut a circuit; on the other hand, the second hacking method only requires software alterations.
Whatever method the user’s choice, specialists from the International Institute of Cyber Security (IICS) remind us that in any way all data stored on the device will be deleted, so the user must make sure to back up any information of interest before rooting the tablet.
You can consult additional details about these hacking methods, as well as the download links of the required apps in the following link.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.










