Software maker issued security patch hours after reports surfaced it was breached.
Developers of the vBulletin software package for website forums released a security patch Monday night, just hours after reports surfaced that a hack on the developers’ site leaked password data and other sensitive information belonging to almost 480,000 subscribers.
vBulletin officials have put in place a mandatory password reset for all users after discovering it was subjected to a hack attack. They went on to warn that the attacker “may have accessed customer IDs and encrypted passwords on our system.” A separate post on the vBulletin site makes reference to a security patch for versions 5.1.4 through 5.1.9 of the vBulletin Connect software package.
Noticeably missing from either link is an explicit warning that there is a critical vulnerability in vBulletin that has already been actively exploited and puts thousands of sites at risk until they install the patch. Ars asked vBulletin officials to clarify the reports and to confirm or disconfirm the speculation they have generated, but so far the request has gone unanswered. This post contains inferences and information from alternative sources that has yet to be explicitly confirmed.
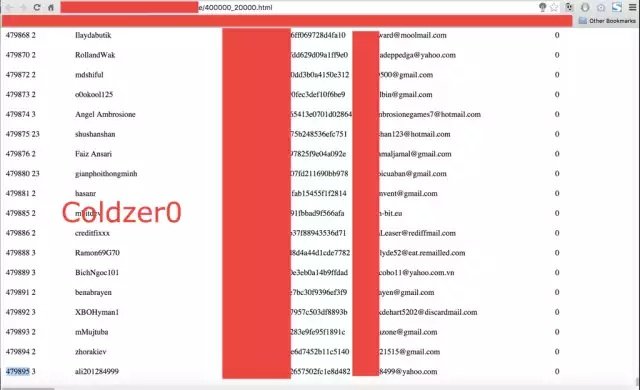
Enter Coldzer0
Over the weekend, a person going by the handle Coldzer0 took to various social media and Web forums, including this discussion group, to claim he breached the vBulletin.com website and obtained personal information belonging to 479,895 users. As proof, Coldzer0 provided the screen shot at the top of this post. Coldzer0 also posted a video to YouTube and additional data to a Facebook page, but those items have since been taken down. Coldzer0 also claimed to use the same vulnerability to compromise forums for Foxit Software. At time of writing, those forums were unavailable.
On top of that, on late Tuesday, someone posted an analysis of a purported three-year-old bug that gives hackers the ability to remotely execute code in sites running vBulletin. “Welp, since it’s fixed now anyway – a more than 3 years old vBulletin 5 PreAuth RCE,” the person posting the writeupwrote on Twitter.
Piecing everything together, it’s hard to escape the inference that the vBulletin software contained a zero-day vulnerability that allowed hackers in the wild to gain almost complete control over websites that used the forum app. If so, administrators for any site that uses vBulletin should drop whatever they’re doing and immediately install Monday’s patch. It also appears that people with accounts on both vBulletin.com and foxitsoftware.com should be explicitly warned that their data has been exposed and that they should change credentials on any other sites that used the same or a similar password. Already, some sites that rely on vBulletin, including the heavily targeted Defcon.org, have suspended user forums until the uncertainty is cleared up. Similar fears over vBulletin security surfaced two years ago.
Again, officials from vBulletin and Foxit Software have yet to explicitly confirm these details, but out of an abundance of caution, Ars is making these recommendations. This post will be updated if either company responds later.
Source:https://arstechnica.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











