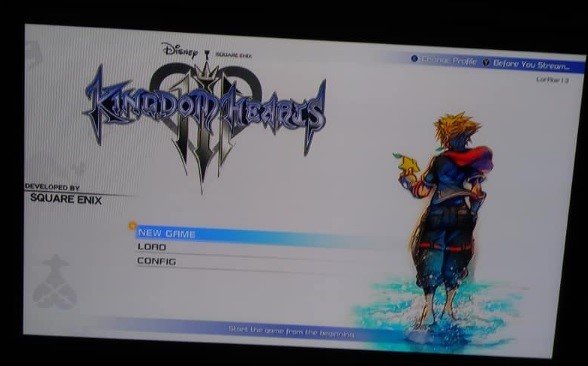
With just a few weeks left for the official release, developers revealed that a security incident led to the theft of some unfinished copies of the videogame
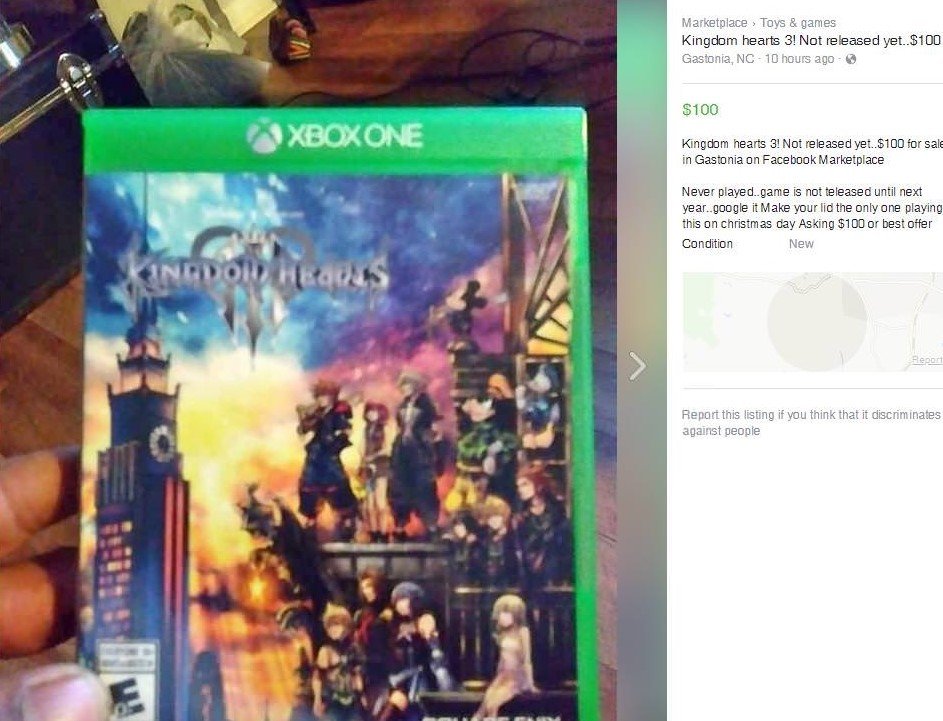
Cybersecurity specialists from the International Institute of Cyber Security reported that some copies of Kingdom Hearts 3 for Xbox One were stolen; in addition, some images and videos were leaked through some social networks. Apparently, an unidentified individual got access to some unfinished copies of the game, although the way this person would have gotten access is still unknown. Later the individual shared some images of the game to show that he actually had the material in his possession, looking for a prospective buyer.
Tetsuya Nomura, director of the videogame, said through his Twitter account: “We are aware that some unfinished copies of Kingdom Heart 3 have been circulating, even when there is about a month left for its official release”. Nomura says the developers already know how the incident happened, although he didn’t reveal any more details at the moment.
The cybersecurity team in charge of Kingdom Hearts 3 also recommends that users do not share or view the leaked footage, although they clarify that the fundamental elements of the game’s history were not included in the leaked copies.
The individual in charge of the leaking had published the material for sale on the Facebook Marketplace, although the social network cybersecurity team banned the publication a few hours later, although it remained online long enough to let many fans and content creators on YouTube disseminate the news of the leak.
This incident has not affected the plans for the official launch of Kingdom Hearts 3, scheduled for January 29, 2019 on platforms such as PlayStation 4 and Xbox One.
The leaking of this video game comes a few weeks after knowing the theft of a copy of Smash Bros. Ultimate in Mexico, which allowed some hackers to access the game in advance.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











