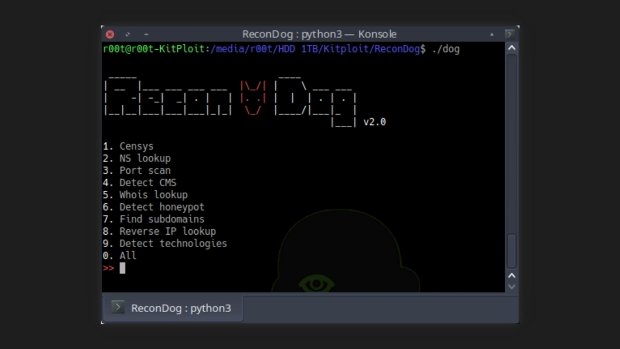
Reconnaissance Swiss army knife
Main Features
- Wizard and CLA interface
- You can extract targets from STDIN (channeled input) and act on them
- According to specialists in digital forensics from the International Institute of Cyber Security, all information is extracted with API, and no direct contact is established with the target
Utilities
- Censys: uses censys.io to collect a large amount of information about an IP address
- NS Lookup: Performs name server search
- Port scan: Scans the most common TCP ports
- Detect CMS: Can detect more than 400 content management systems
- Whois Lookup: Performs whois protocol search
- Detect honeypot: Uses Shodan to identify whether the target is a honeypot
- Find subdomains: Search for sub-domains using com
- Reverse IP Lookup: Does an inverse IP lookup to find domains associated with an IP address
- Detect technologies: Uses wappalyzer.com to detect over a thousand technologies
- All: According to experts in digital forensics, this utility executes all the previous utilities in the target
Compatibility
ReconDog runs on any system that has a Python interpreter installed. Experts in digital forensics report that this tool has been tested in the following configurations:
- Windows, Linux and MAC operating systems
- Versions of Python 2.7 to 3.6
Installation
ReconDog does not require manual configuration and can be run simply as a normal Python script.
Use
Wizard Interface
The wizard interface is the easiest way to use ReconDog. Just run the program, select what you want to do and enter the target, it’s that simple.
CLA interface
ReconDog also has a CLA interface. You can find subdomains in the following way:
python dog -t marvel.com -c 7
There’s still more. If you have a program that can enumerate subdomains and you want to scan ports of all the subdomains you find, ReconDog is designed to handle this type of case. Simply use this command:
subdomainfinder -t example.com | python dog –domains -c 3
No matter what type of output the other program generates, ReconDog uses regular expressions to find targets, which makes it easy to integrate literally all the tools. There are two switches available:
–domains extract domains from STDIN
–ips extract ip addresses from STDIN

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.