The baseStriker technique, uncovered by information security researchers from the company Avanan, allows you to bypass anti-phishing filters by dividing and masking a malicious link using a tag called <base> URL tag, used by malicious actors in nature to bypass the function ` Safe Links` of Microsoft Office 365.
The Safe Links feature designed by Microsoft to protect users from malicious code and phishing attacks is part of Microsoft’s Advanced Threat Protection (ATP).

At the end of October last year, the ATP Safe Links protection was extended to work with web addresses (URL) in emails and URLs in Office 365 ProPlus documents, such as Word, Excel, PowerPoint in Windows, iOS and Android devices, and Visio files in Windows.
Information security experts explain that this security feature works by replacing URLs in an incoming email with secure URLs owned by Microsoft.
At the moment when the user clicks on a link in an incoming email, it redirects the user to a domain operated by Microsoft to verify the original URL. If the scan detects a malicious activity, then it warns the users; otherwise, the user will be redirected to the original link.
BaseStriker takes advantage of the URL <base> tag in the header of an HTML email to divide and disguise a malicious link, information security experts say.
“BaseStriker refers to the method used to exploit this vulnerability: divide and disguise a malicious link using a tag called <base> URL tag” says the analysis published by Avanan.
“This attack sends a malicious link, which would usually be blocked by Microsoft.
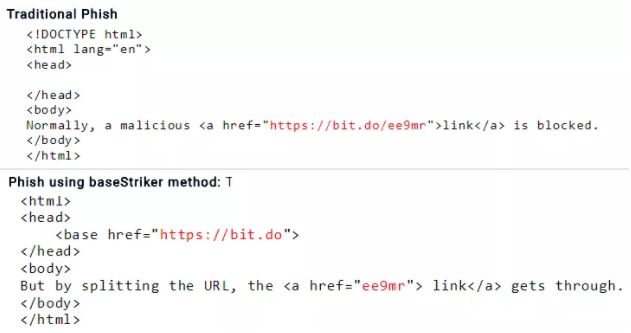
In the tests of the baseStriker technique they showed that Office 365 users are vulnerable.
“The vulnerability has been tested in various configurations, the proof is that anyone who uses Office 365 in any configuration is vulnerable, Gmail does not have this problem, if you are protecting Office 365 with Mimecast, you are sure, but Proofpoint is also vulnerable.” says the publication.

Information security professionals commented that malicious actors are already using baseStriker to carry out phishing campaigns, they also warn that the technique can be exploited to distribute malware.
Avanan reported on baseStriker to Microsoft and Proofpoint last weekend, but there is still no patch available.
“Because the vulnerability is already known, an immediate step would be to notify users and reinforce the risk of phishing attacks.”

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











