Almost a year ago, on May 4, 2017, information security researcher privately discovered and reported a spoofing vulnerability of the recipient in Google Inbox. The expert noticed that the composition box always hid the email addresses of named recipients without providing a way to inspect the actual email address, and discovered how to abuse this with mailto: links containing named recipients.
The link mailto: “support@paypal.com” <scam@phisher.example> is indicated as “support@paypal.com” in the composition window of the Google inbox.
To exploit this vulnerability, the target user only needs to click on a malicious link. The experts comment that it can also be activated by clicking on a direct link to the mailto: handler page in the inbox.
This vulnerability has not yet been corrected.
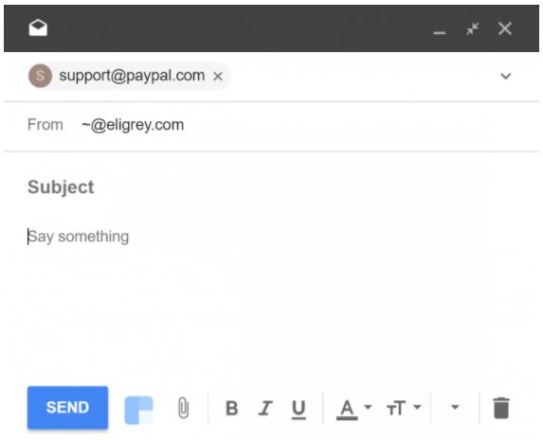
The information security professionals comment that the recipient “support@paypal.com” is being falsified in the composition window of the Google inbox. The real recipient is “scam@phisher.example”.
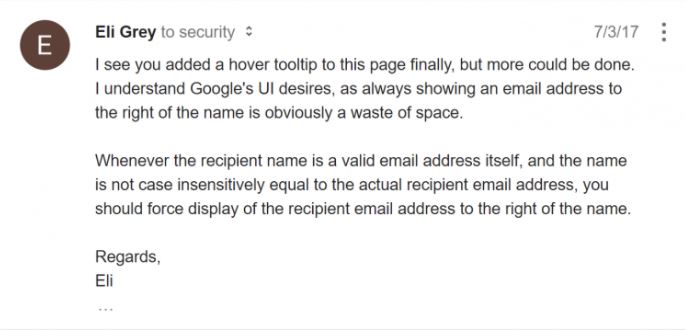
In July of 2017, the expert noticed that Google had added information about emerging tools to this field in Inbox; this allowed users to manually confirm the recipient’s email address. The default display of the email address was still vulnerable to spoofing, another notice was sent via email to Google.
After receiving no response for more than 8 months, another notification was sent via email in March 2018.
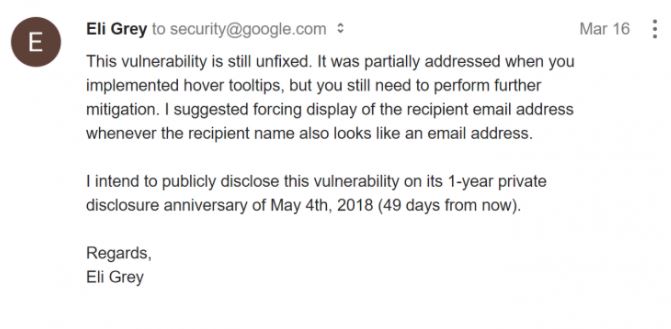
Nine months after sending the emails the information security researcher received a response, which leads to believe that Google really does not want to solve this vulnerability.


Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











