A HACKER WHO claims to have broken into the AOL account of CIA Director John Brennan says he obtained access by posing as a Verizon worker to trick another employee into revealing the spy chief’s personal information.
Using information like the four digits of Brennan’s bank card, which Verizon easily relinquished, the hacker and his associates were able to reset the password on Brennan’s AOL account repeatedly as the spy chief fought to regain control of it.
News of the hack was first reported by the New York Post after the hacker contacted the newspaper last week. The hackers described how they were able to access sensitive government documents stored as attachments in Brennan’s personal account because the spy chief had forwarded them from his work email.
The documents they accessed included the sensitive 47-page SF-86 application that Brennan had filled out to obtain his top-secret government security clearance. Millions of SF86 applications were obtained recently byhackers who broke into networks belonging to the Office of Personnel Management. The applications, which are used by the government to conduct a background check, contain a wealth of sensitive data not only about workers seeking security clearance, but also about their friends, spouses and other family members. They also include criminal history, psychological records and information about past drug use as well as potentially sensitive information about the applicant’s interactions with foreign nationals—information that can be used against those nationals in their own country.
The hacker, who says he’s under 20 years old, told WIRED that he wasn’t working alone but that he and two other people worked on the breach. He says they first did a reverse lookup of Brennan’s mobile phone number to discover that he was a Verizon customer. Then one of them posed as a Verizon technician and called the company asking for details about Brennan’s account.
“[W]e told them we work for Verizon and we have a customer on scheduled callback,” he told WIRED. The caller told Verizon that he was unable to access Verizon’s customer database on his own because “our tools were down.”
After providing the Verizon employee with a fabricated employee Vcode—a unique code the he says Verizon assigns employees—they got the information they were seeking. This included Brennan’s account number, his four-digit PIN, the backup mobile number on the account, Brennan’s AOL email address and the last four digits on his bank card.
“[A]fter getting that info, we called AOL and said we were locked out of our AOL account,” he said. “They asked security questions like the last 4 on [the bank] card and we got that from Verizon so we told them that and they reset the password.” AOL also asked for the name and phone number associated with the account, all of which the hackers had obtained from Verizon.
On October 12, they gained access to Brennan’s email account, where they read several dozen emails, some of them that Brennan had forwarded from his government work address and that contained attachments. The hacker provided WIRED with both Brenann’s AOL address and the White House work address used to forward email to that account.
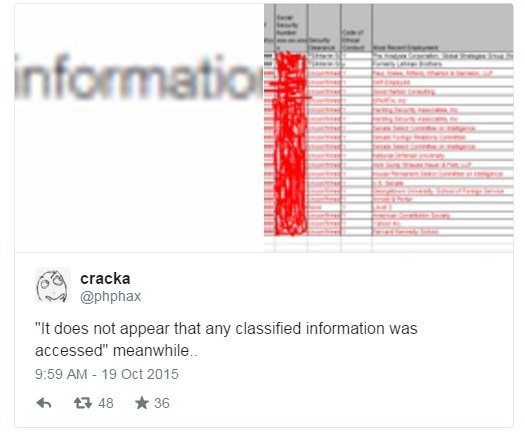
Among the attachments was a spreadsheet containing names and Social Security numbers—some of them for US intelligence officials—and a letter from the Senate asking the CIA to halt its use of harsh interrogation techniques—that is, its controversial use of torture tactics.
These documents appear to come from 2009. The Associated Press has speculated that the spreadsheet might be a list of guests who were visiting the White House that year when Brennan was President Obama’s counter-terrorism adviser.
The hackers posted screenshots of some of the documents on their Twitter account, @phphax. Among the items posted were links to a file the hackers say contained portions of Brennan’s contact list as well as a log of phone calls by former CIA deputy director Avril Haines. They also posted a reduced page from the spreadsheet.
The hackers were in Brennan’s account for three days before it was disabled last Friday.
On October 16, the hacker Tweeted that Brennan had deleted his AOL account after they had notified him of the breach.
The hacker told WIRED that Brennan had tried to access the account and couldn’t.
He told WIRED that Brennan re-set the password, and they hijacked it again. “[H]e took back access and we re-jacked it. That happened 3 times,” he said.
So they called Brennan’s mobile number, using VoIP, and told him he’d been hacked. The conversation was brief.
“[I]t was like ‘Hey,…. its CWA.’ He was like ‘What do you want?’ We said ‘2 trillion dollars hahhaa, just joking,’” the hacker recounted to WIRED.
Brennan, the hacker says, replied, “How much do you really want?”
They told Brennan “We just want Palestine to be free and for you to stop killing innocent people.”
In addition to Brennan’s AOL account, the hackers also broke into the Comcast account of Homeland Security Secretary Jeh Johnson.
The news of the breach, of course, comes in the midst of another email scandal involving Hillary Clinton who has been under fire for months over a private server and email account she maintained to do official work. Clinton has been accused of maintaining the server to bypass public records requests involving her government email address.
It’s unclear if Brennan was using his personal email to conduct government business or if he simply used it to occasionally store email and documents from his work account.
The hack, using social-engineering techniques to pull information from tech support, is reminiscent of the epic hack that targeted former WIRED writer Mat Honan. In that case, Apple tech support gave a hacker named Cosmo access to Honan’s iCloud account, and Amazon tech support gave him the ability to see the last four digits of Honan’s credit card number. which the hacker then used to gain access to Honan’s iCloud account, and that in turn led to the hacker obtaining access to a series of other accounts.
Source:https://www.wired.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.