The authors of the XiaoBa ransomware have retooled their malware’s code into a cryptocurrency miner (coinminer).
According to information security experts, despite not encrypting files anymore, the XiaoBa coinminer still destroys users’ data thanks to a series of bugs that primarily corrupt a user’s executable files.
The XiaoBa ransomware is one of those ransomware strains that have been active on the malware scene for months, but very few people have heard of it, mainly because it was never at the center of a mass distribution campaign.

Researchers first spotted a first version of the XiaoBa ransomware in October last year, and a second one, a month later.
These first two versions only targeted Chinese users, but a third version released in February, this year, also contained ransom notes in English, suggesting its author might have expanded his targeting base.
But now, Trend Micro information security researchers say they identified what appears to be a modified version of the XiaoBa ransomware, but coded to work as a file infector and cryptocurrency miner.
You’d think that XiaoBa getting converted into a coinminer is a good thing. However, it is not so. This new XiaoBa coinminer contains sloppy code that destroys user files and will crash PCs.
The reason this happens is because of the XiaoBa “file infector,” a component that scans the local file system and appends the XiaoBa malware to other files.
According to experts, the current version of the XiaoBa coinminer will inject a copy of itself and the legitimate XMRig cryptocurrency mining software inside all EXE, COM, SCR, and PIF files found on an infected computer.
But information security professionals say this “executable injection routine” has been poorly coded, so much so that XiaoBa injects multiple versions of itself into other executables, and may even take legitimate executables and inject them into other legitimate executables many times over.
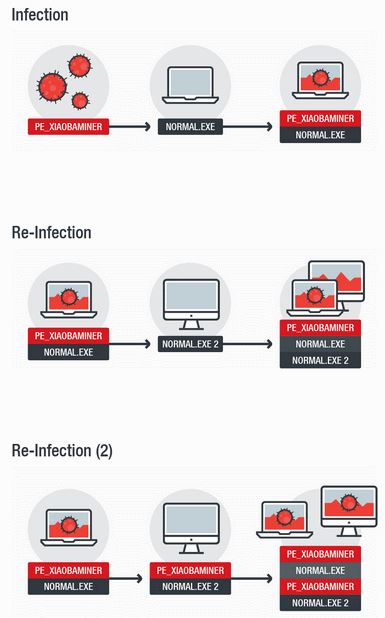
The main disadvantage of this faulty file injection process is that it artificially inflates file sizes, taking up local disk space.
New XiaoBa coinminer destroys executables, crashes PCs. But this isn’t the only problem. Hackers created the file injector process to make sure that regardless of what application the user starts, the XiaoBa coinminer also runs beside it. However, they messed up their code and running any of the “injected” executables only starts the coinminer, but not the legitimate app.
Moreover, the XiaoBa file infector also attaches the coinminer to executables all over the hard drive, including core operating system folders.
Because the injection process is faulty and the “injected” process doesn’t start, this leads to issues where users’ computers will not be able to boot because core Windows executables have been accidentally neutered by the shoddy XiaoBa file injector component.
According to information security experts, XiaoBa also injects CoinHive in local HTML files. But if by a miracle an infected users’ computer boots up, users should be aware that XiaoBa also injects a copy of the CoinHive JavaScript library inside all HTML and HTM files, and also deletes all GHO and ISO files, for an unknown reason.
With XiaoBa inflicting such damage to users’ computers, even if there’s no file encryption features included with this new XiaoBa version, the malware is as dangerous as the first three ransomware variants, and users may need to restore from backups to recover deleted or “injected” files.

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











