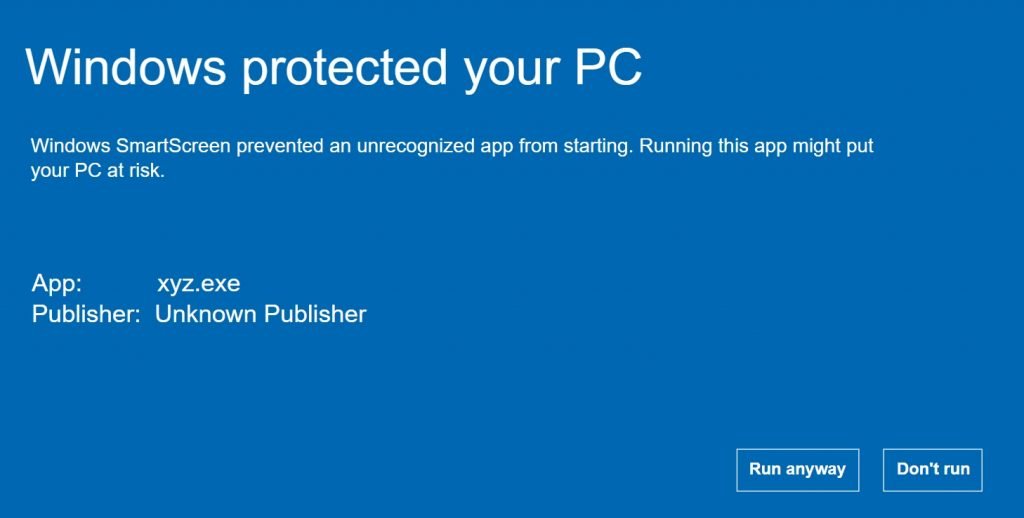
Microsoft SmartScreen
Overview: Microsoft SmartScreen is a cloud-based anti-phishing and anti-malware component that comes integrated with various Microsoft products like Microsoft Edge, Internet Explorer, and Windows. It is designed to protect users from malicious websites and downloads.
Key Features:
- URL Reputation:
- SmartScreen checks the URL of websites against a list of known malicious sites stored on Microsoft’s servers. If the URL matches one on the list, the user is warned or blocked from accessing the site.
- Application Reputation:
- When a user downloads an application, SmartScreen checks its reputation based on data collected from other users who have downloaded and installed the same application. If the app is deemed suspicious, the user is warned before proceeding with the installation.
- Phishing Protection:
- SmartScreen analyzes web pages for signs of phishing and alerts the user if a site appears to be trying to steal personal information.
- Malware Protection:
- The system can identify and block potentially malicious software from running on the user’s device.
- Integration with Windows Defender:
- SmartScreen works in conjunction with Windows Defender to provide a layered security approach, ensuring comprehensive protection against threats.
How it Works:
- URL and App Checks:
- When a user attempts to visit a website or download an application, SmartScreen sends a request to the SmartScreen service with the URL or app details.
- The service checks the details against its database and returns a verdict to the user’s device.
- Based on the verdict, the browser or operating system either allows, blocks, or warns the user about potential risks.
- Telemetry and Feedback:
- SmartScreen collects telemetry data from users’ interactions with websites and applications, which helps improve the accuracy of its threat detection algorithms over time.
Smart App Control (SAC)
Overview: Smart App Control (SAC) is a security feature in Windows designed to prevent malicious or potentially unwanted applications from running on the system. It is an evolution of the earlier Windows Defender Application Control (WDAC) and provides advanced protection by utilizing cloud-based intelligence and machine learning.
Key Features:
- Predictive Protection:
- SAC uses machine learning models trained on a vast amount of data to predict whether an application is safe to run. It blocks apps that are determined to be risky or have no known good reputation.
- Cloud-Based Intelligence:
- SAC leverages Microsoft’s cloud infrastructure to continuously update its models and threat intelligence, ensuring that protection is always up-to-date.
- Zero Trust Model:
- By default, SAC assumes that all applications are untrusted until proven otherwise, aligning with the zero trust security model.
- Seamless User Experience:
- SAC operates silently in the background, allowing trusted apps to run without interruptions while blocking potentially harmful ones. Users receive clear notifications and guidance when an app is blocked.
- Policy Enforcement:
- Administrators can define policies to control app execution on enterprise devices, ensuring compliance with organizational security standards.
How it Works:
- App Analysis:
- When an app attempts to run, SAC sends its metadata to the cloud for analysis.
- The cloud service evaluates the app against its machine learning models and threat intelligence to determine its risk level.
- Decision Making:
- If the app is deemed safe, it is allowed to run.
- If the app is determined to be risky or unknown, it is blocked, and the user is notified with an option to override the block if they have sufficient permissions.
- Policy Application:
- SAC policies can be customized and enforced across an organization to ensure consistent security measures on all managed devices.
Integration with Windows Security:
- SAC is integrated with other Windows security features like Microsoft Defender Antivirus, providing a comprehensive defense strategy against a wide range of threats.
Despite the robust protections offered by Microsoft SmartScreen and Smart App Control (SAC), some techniques can sometimes bypass these features through several sophisticated techniques.
1. Signed Malware Bypassing Microsoft SmartScreen and SAC
1. Valid Digital Signatures:
- Stolen Certificates: Cybercriminals can steal valid digital certificates from legitimate software developers. By signing their malware with these stolen certificates, the malware can appear trustworthy to security features like SmartScreen and SAC.
- Bought Certificates: Attackers can purchase certificates from Certificate Authorities (CAs) that might not perform thorough background checks. These certificates can then be used to sign malware.
2. Compromised Certificate Authorities:
- If a Certificate Authority (CA) is compromised, attackers can issue valid certificates for their malware. Even if the malware is signed by a seemingly reputable CA, it can still be malicious.
3. Certificate Spoofing:
- Advanced attackers may use sophisticated techniques to spoof digital certificates, making their malware appear as if it is signed by a legitimate source. This can deceive security features into trusting the malware.
4. Timing Attacks:
- Some malware authors time their attacks to take advantage of the period between when a certificate is issued and when it is revoked or added to a blacklist. During this window, signed malware can bypass security checks.
5. Use of Legitimate Software Components:
- Attackers can incorporate legitimate software components into their malware. By embedding malicious code within a signed, legitimate application, the entire package can be trusted by security features.
6. Multi-Stage Attacks:
- Initial stages of the malware may appear harmless and thus be signed and trusted. Once the initial stage is executed and trusted by the system, it can download and execute the actual malicious payload.
7. Social Engineering:
- Users may be tricked into overriding security warnings. For example, if SmartScreen or SAC blocks an application, an attacker might use social engineering tactics to convince the user to manually bypass the block.
2. How Reputation Hijacking Bypasses Microsoft SmartScreen and SAC
- Compromised Legitimate Websites:
- Method: Attackers compromise a legitimate website that has a strong reputation and inject malicious content or host malware on it.
- Bypass Mechanism: Since SmartScreen relies on the reputation of websites to determine if they are safe, a website with a previously good reputation may not trigger alerts even if it starts serving malicious content. Users are not warned because the site’s reputation was established before the compromise.
- Trusted Domains and Certificates:
- Method: Attackers use domains with valid SSL certificates issued by trusted Certificate Authorities (CAs) to host malicious content.
- Bypass Mechanism: SmartScreen and SAC check for valid certificates as part of their security protocols. A valid certificate from a trusted CA makes the malicious site appear legitimate, thus bypassing the security checks that would flag a site with an invalid or self-signed certificate.
- Embedding Malware in Legitimate Software:
- Method: Attackers inject malicious code into legitimate software or its updates.
- Bypass Mechanism: If the legitimate software has a good reputation and is signed with a valid certificate, SmartScreen and SAC are less likely to flag it. When users update the software, the malicious payload is delivered without triggering security warnings because the update appears to be from a trusted source.
- Phishing with Spoofed Emails:
- Method: Attackers send phishing emails that appear to come from trusted sources, often using spoofed email addresses.
- Bypass Mechanism: Users are more likely to trust and open emails from familiar and reputable sources. SmartScreen may not always catch these emails, especially if they come from legitimate domains that have been spoofed, leading users to malicious websites or downloads.
- Domain and Subdomain Takeover:
- Method: Attackers take over expired or unused domains and subdomains of reputable sites.
- Bypass Mechanism: Since the domain or subdomain was previously associated with a legitimate entity, SmartScreen and SAC may continue to trust it based on its historical reputation. This allows attackers to serve malicious content from these domains without raising security flags.
- Social Engineering Attacks:
- Method: Attackers trick users into overriding security warnings by posing as legitimate sources or using persuasive tactics.
- Bypass Mechanism: Even if SmartScreen or SAC warns users, skilled social engineering can convince them to bypass these warnings. Users might disable security features or proceed despite warnings if they believe the source is trustworthy.
3. How Reputation Seeding Bypasses Microsoft SmartScreen and SAC
Reputation seeding is a tactic where attackers build a positive reputation for malicious domains, software, or email accounts over time before launching an attack. This can effectively bypass security measures like Microsoft SmartScreen and Smart App Control (SAC) because these systems often rely on reputation scores to determine the trustworthiness of an entity. Here’s how reputation seeding works and strategies to mitigate it:
How Reputation Seeding Works
- Initial Clean Activity:
- Method: Attackers initially use their domains, software, or email accounts for legitimate activities. This involves hosting benign content, sending non-malicious emails, or distributing software that performs as advertised without any harmful behavior.
- Bypass Mechanism: During this period, SmartScreen and SAC observe and record these entities as safe and build a positive reputation for them. Users interacting with these entities during the seeding phase do not encounter any security warnings.
- Gradual Introduction of Malicious Content:
- Method: Over time, attackers start to introduce malicious content slowly. This might involve adding malware to software updates, injecting harmful code into websites, or sending phishing emails from trusted accounts.
- Bypass Mechanism: Because the entities have already established a positive reputation, initial malicious activities may not be immediately flagged by SmartScreen or SAC, allowing the attackers to reach their targets.
- Leveraging Established Trust:
- Method: Once a strong reputation is established, attackers conduct large-scale malicious campaigns. They leverage the trust built over time to bypass security checks and deceive users.
- Bypass Mechanism: The established positive reputation causes security systems to consider these entities as low-risk, allowing malware or phishing attempts to bypass filters and reach users without triggering alarms.
Typical Timeframes for Reputation Seeding
- Websites:
- Short-Term (Weeks): Initial establishment of a website with benign content and basic user interactions.
- Medium-Term (Months): Gaining backlinks, increasing traffic, and more extensive content creation.
- Long-Term (6+ Months): Strong reputation with significant traffic, positive user interactions, and established trust.
- Software:
- Short-Term (Weeks): Initial distribution and passing basic security checks.
- Medium-Term (Months): Accumulating downloads, positive user reviews, and routine updates.
- Long-Term (6+ Months): Strong reputation with widespread usage and consistently positive feedback.
- Email Accounts:
- Short-Term (Weeks): Initial legitimate emails and normal interactions.
- Medium-Term (1-2 Months): Building trust through regular, benign communication.
- Long-Term (3+ Months): Established trust with consistent, non-malicious activity.
4 .How Reputation Tampering Bypasses Microsoft SmartScreen and SAC
Reputation tampering, particularly in the context of Smart App Control (SAC), can exploit the way SAC assesses and maintains the reputation of files. Given that SAC might use fuzzy hashing, feature-based similarity comparisons, and machine learning models to evaluate file reputation, attackers can manipulate certain segments of a file without changing its perceived reputation. Here’s a deeper dive into how this works and the potential implications:
How Reputation Tampering Works in SAC
- Fuzzy Hashing:
- Method: Unlike traditional cryptographic hashing, which changes completely with any alteration to the file, fuzzy hashing allows for minor changes without drastically altering the hash value. This means that files with small modifications can still be considered similar to the original.
- Attack: Attackers modify segments of the file that do not significantly affect the fuzzy hash value, allowing the file to retain its reputation.
- Feature-Based Similarity Comparisons:
- Method: SAC may use feature-based similarity comparisons to evaluate files. These features could include metadata, structural attributes, or specific code patterns that are consistent with known good files.
- Attack: By understanding which features are used and ensuring that these remain unchanged while modifying other parts of the file, attackers can maintain the file’s good reputation.
- Machine Learning Models:
- Method: Machine learning models in the cloud may analyze files based on patterns learned from a large dataset of known good and bad files. These models might use a variety of indicators beyond simple hashes.
- Attack: Through trial and error, attackers identify which code sections can be altered without changing the overall pattern recognized by the ML model as benign. They can then inject malicious code into these sections.
5. How LNK stomping Bypasses Microsoft SmartScreen and SAC
LNK stomping is a technique where attackers modify LNK (shortcut) files to execute malicious code while appearing legitimate to users and security systems. By leveraging the flexibility and capabilities of LNK files, attackers can disguise their malicious intentions and bypass security features such as Microsoft SmartScreen and Smart App Control (SAC). Here’s how LNK stomping works and how it can bypass these security features:
How LNK Stomping Works
- Creating a Malicious LNK File:
- Method: Attackers create an LNK file that points to a legitimate executable or document but includes additional commands or scripts that execute malicious code.
- Example: An LNK file might appear to open a PDF document, but in reality, it executes a PowerShell script that downloads and runs malware.
- Modifying Existing LNK Files:
- Method: Attackers modify existing LNK files on a target system to include malicious commands while retaining their original appearance and functionality.
- Example: An LNK file for a commonly used application (e.g., a web browser) is modified to first execute a malicious script before launching the application.
- Embedding Malicious Code:
- Method: Attackers embed malicious code directly within the LNK file, taking advantage of the file’s structure and features.
- Example: An LNK file might contain embedded shell commands that execute when the shortcut is opened.
Understanding the MotW Bypass via LNK File Manipulation
The Mark of the Web (MotW) is a critical security feature used to flag files downloaded from the internet, making them subject to additional scrutiny by antivirus (AV) and endpoint detection and response (EDR) systems, including Microsoft SmartScreen and Smart App Control (SAC). However, certain techniques can bypass this feature, allowing potentially malicious files to evade detection. Here, we’ll explore how manipulating LNK (shortcut) files can bypass MotW checks
Manually Creating an LNK File with a Non-Standard Target Path
- Locate the PowerShell Script:
- Ensure you have the path to the PowerShell script, for example,
C:\Scripts\MyScript.ps1.
- Ensure you have the path to the PowerShell script, for example,
- Create the Shortcut:
- Right-click on the desktop or in the folder where you want to create the shortcut.
- Select New > Shortcut.
- Enter the Target Path:
- In the “Type the location of the item” field, enter the following command with a non-standard path:
powershell.exe -File "C:\Scripts\MyScript.ps1."- Notice the extra dot at the end of the script path.
- Name the Shortcut:
- Enter a name for your shortcut (e.g.,
Run MyScript Non-Standard). - Click Finish.
- Enter a name for your shortcut (e.g.,
- Verify the Target Path:
- Right-click the newly created shortcut and select Properties.
- In the Target field, you should see:
powershell.exe -File "C:\Scripts\MyScript.ps1."- Click OK to save the changes.
By following these steps, you can create an LNK file that points to a PowerShell script with a non-standard target path. This can be used for testing how such files interact with security features like SmartScreen and Smart App Control.
Manually Creating an LNK File with a Relative Path
- Locate the PowerShell Script:
- Ensure you have the relative path to the PowerShell script within its directory structure, for example,
.\Scripts\MyScript.ps1.
- Ensure you have the relative path to the PowerShell script within its directory structure, for example,
- Create the Shortcut:
- Right-click on the desktop or in the folder where you want to create the shortcut.
- Select New > Shortcut.
- Enter the Target Path:
- In the “Type the location of the item” field, enter the following command with a relative path:
powershell.exe -File ".\Scripts\MyScript.ps1"- Click Next.
- Name the Shortcut:
- Enter a name for your shortcut (e.g.,
Run MyScript Relative). - Click Finish.
- Enter a name for your shortcut (e.g.,
- Verify the Target Path:
- Right-click the newly created shortcut and select Properties.
- In the Target field, you should see:
powershell.exe -File ".\Scripts\MyScript.ps1"- Click OK to save the changes.
Manually Creating an LNK File with a multi-level path
To create an LNK file with a multi-level path in the target path array, we need to manipulate the internal structure of the LNK file to contain a non-standard target path. This involves using a utility or script that can handle the creation and modification of LNK files with detailed control over their internal structure.
Here’s a step-by-step guide to creating such an LNK file using PowerShell and a specialized library for handling LNK files, pylnk3, which is a Python-based library. For this example, you will need to have Python installed along with the pylnk3 library.
Step-by-Step Guide
Prerequisites
- Install Python:
- If you don’t have Python installed, download and install it from the official website: Python.org.
- Install
pylnk3Library:- Open a command prompt or terminal and run the following command to install
pylnk3:shCopy codepip install pylnk3
- Open a command prompt or terminal and run the following command to install
Creating a Multi-Level Path LNK File
Create a Python Script to Generate the LNK File:
- Create a Python script (e.g.,
create_lnk.py) with the following content:
import lnk
# Define the path for the new shortcut
shortcut_path = "C:\\Users\\Public\\Desktop\\MyScriptShortcutMultiLevel.lnk"
# Create a new LNK file
lnk_file = lnk.lnk_file()
# Set the target path with multi-level path entries
lnk_file.add_target_path_entry("..\\..\\Scripts\\MyScript.ps1")
# Set the arguments for the target executable
lnk_file.command_line_arguments = "-File .\\Scripts\\MyScript.ps1"
# Save the LNK file
with open(shortcut_path, "wb") as f:
lnk_file.write(f)
print(f"Shortcut created at: {shortcut_path}")
Run the Python Script:
- Open a command prompt or terminal and navigate to the directory where your Python script is located.
- Run the script using the following command:shCopy code
python create_lnk.py
Explanation
- lnk.lnk_file(): Creates a new LNK file object.
- add_target_path_entry: Adds entries to the target path array. Here, we use a relative path (
..\\..\\Scripts\\MyScript.ps1) to simulate a multi-level path. - command_line_arguments: Sets the arguments passed to the target executable. In this case, we pass
-File .\Scripts\MyScript.ps1. - write: Saves the LNK file to the specified path.
Additional Notes
- Relative Paths: The use of relative paths (
..\\..\\) in the target path entries allows us to create a multi-level path structure within the LNK file. - Non-Standard Structures: By manipulating the internal structure of the LNK file, we can craft paths that might bypass certain security checks.
Running the LNK File
After creating the LNK file, you can test its behavior by double-clicking it. The crafted LNK file should follow the relative path and execute the target PowerShell script, demonstrating how non-standard paths can be used within an LNK file.
The article “Dismantling Smart App Control” by Elastic Security Labs explores the vulnerabilities and bypass techniques of Windows Smart App Control (SAC) and SmartScreen. For more details, you can read the full article here.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











