In a significant cybersecurity revelation, a zero-day vulnerability in the Telegram messaging app for Android, dubbed ‘EvilVideo,’ has been uncovered, allowing attackers to send malicious Android APK payloads disguised as video files. This exploit, which has recently been patched, posed a serious threat to millions of Telegram users globally.
The vulnerability was discovered by cybersecurity researchers who found that threat actors could craft malicious APK files that appeared as video files within the Telegram app. When users attempted to play these videos, they were prompted to open the file in an external application, leading to the installation of the malicious APK and potentially compromising the user’s device.
The Telegram ‘EvilVideo’ zero-day vulnerability allowed attackers to send Android APK files disguised as video files. This exploitation was primarily due to insufficient file validation and improper handling of media files within the Telegram Android app.
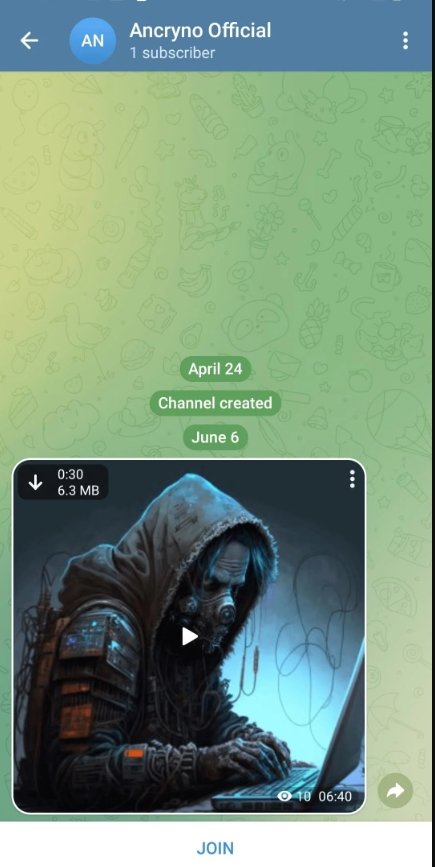
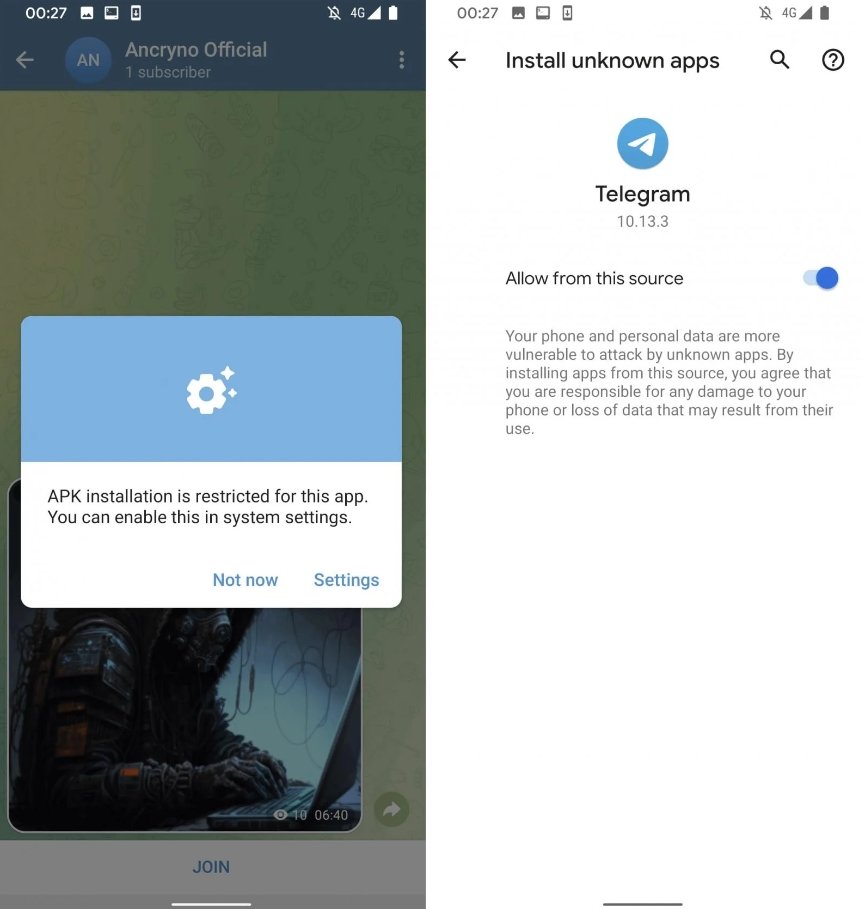
Exploitation Process:
- Crafting the Malicious APK:
- File Header Modification: Attackers crafted a malicious APK file by modifying its file header and metadata to mimic those of a legitimate video file. This involves altering the file extension and adjusting the header information so that the APK file appears as a common video format such as MP4 or AVI.
- Embedding Malicious Code: The APK file was embedded with malicious payloads, which could range from spyware to ransomware. This payload was designed to execute specific actions once installed on the victim’s device.
- Disguising the Malicious Payload:
- Manipulating File Metadata: Attackers manipulated the file metadata to ensure that Telegram’s initial file inspection would not flag the file as suspicious. This included changing the MIME type and file extension to those associated with video files.
- Creating a Deceptive Appearance: The file was named and presented in a way that would not raise immediate suspicion from the user. For example, it might be named “vacation_video.mp4” to appear as an innocent video.
- Delivering the Malicious APK via Telegram:
- Sending the File: The attacker sent the disguised APK file to the target using Telegram. The vulnerability in Telegram’s file handling allowed the app to accept and present the file as a video.
- Initial User Interaction: The recipient sees the file as a video and attempts to play it within Telegram. The app, recognizing the file as a video, tries to play it but fails due to its true APK nature.
- Triggering the Exploit:
- Error Prompt: When the user tries to play the “video,” Telegram displays an error message indicating that the video cannot be played within the app. It then prompts the user to open the file using an external application.
- Executing the Malicious APK: If the user consents to open the file externally, the operating system’s file handler processes the file as an APK and executes it. This results in the installation of the malicious payload on the device.
- Post-Exploitation Actions:
- Payload Execution: Once installed, the malicious APK can perform various harmful activities based on the attacker’s intent. This might include exfiltrating personal data, encrypting files for ransom, or creating backdoors for further exploitation.
- Maintaining Persistence: The malware may also establish persistence on the device, ensuring that it remains active even after reboots or attempts to remove it.
Technical Specifics of the Exploit:
- File Header and Metadata Spoofing: By altering the file header and metadata, attackers could bypass Telegram’s superficial file validation checks.
- MIME Type Manipulation: Changing the MIME type to video formats such as “video/mp4” misled Telegram into treating the APK file as a video.
- Error Handling Exploitation: Leveraging the error prompt mechanism, attackers guided users to execute the APK file using external apps, where the actual nature of the file would be revealed and executed by the Android OS.
Mitigation and Prevention:
- Enhanced File Validation: Telegram’s patch involved implementing stricter file validation processes, ensuring that files were thoroughly checked before being accepted as media files.
- User Education: Educating users about the risks of opening unknown files and the importance of verifying the source of received media can reduce the likelihood of such exploits being successful.
- Security Software: Utilizing robust security applications that can detect and block malicious APKs, even when disguised as media files, adds an additional layer of protection.
Best Practices for Users:
- Keep Apps Updated:
- Always ensure that apps, particularly those handling sensitive information or media, are updated to the latest versions to benefit from security patches and enhancements.
- Exercise Caution with Unknown Files:
- Avoid opening files from unknown or untrusted sources. Be especially wary of media files that prompt external application execution.
- Employ Security Solutions:
- Use robust security software to detect and mitigate potential threats. This includes antivirus programs and malware scanners that can identify and block malicious APKs.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.










