Elastic Security Labs has uncovered a novel technique, GrimResource, that leverages specially crafted Microsoft Management Console (MMC) files for initial access and evasion, posing a significant threat to cybersecurity.
In response to Microsoft’s decision to disable Office macros by default for internet-sourced documents, attackers have been forced to adapt, exploring new infection vectors like JavaScript, MSI files, LNK objects, and ISOs. These traditional methods are now heavily scrutinized by defenders, pushing well-resourced attackers to innovate further. A recent example includes North Korean actors using a novel command execution technique within MMC files.
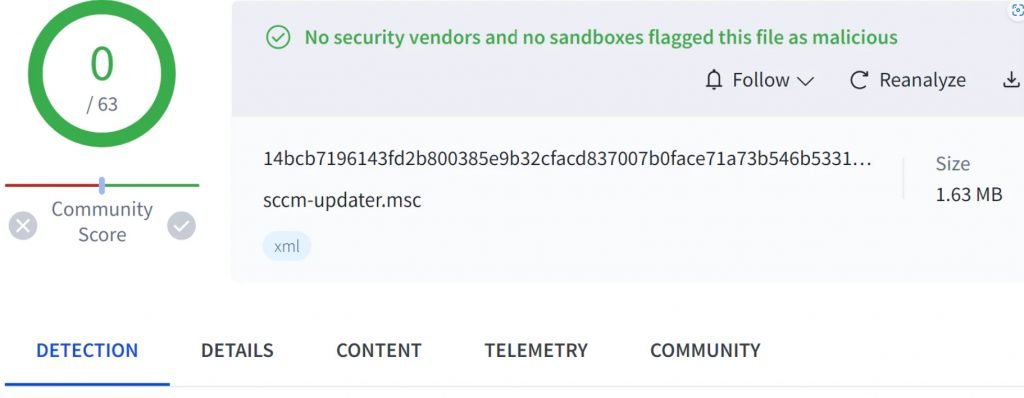
Elastic researchers have identified GrimResource, a new infection technique that exploits MSC files, allowing attackers to execute arbitrary code in the context of mmc.exe when a user opens a specially crafted MSC file. The first sample leveraging GrimResource was uploaded to VirusTotal on June 6th.
Key Takeaways
- GrimResource enables attackers to execute arbitrary code in Microsoft Management Console with minimal security warnings, making it ideal for initial access and evasion.
- Elastic Security Labs provides analysis and detection guidance to help the community defend against this technique.
Detailed Analysis
Initial Discovery
The GrimResource method was identified after a sample was uploaded to VirusTotal on June 6th, 2024. This sample demonstrated a novel way to achieve code execution by exploiting the MSC file format, commonly used in administrative tools within Windows.
Technical Breakdown
Exploitation of apds.dll Vulnerability
The core of the GrimResource technique exploits an old cross-site scripting (XSS) flaw in the apds.dll library. By crafting an MSC file that includes a reference to this vulnerable library in the StringTable section, attackers can execute arbitrary JavaScript in the context of mmc.exe. This approach leverages the following steps:
- StringTable Manipulation: The MSC file is modified to include a reference to apds.dll.
- JavaScript Execution: The XSS flaw in apds.dll allows JavaScript execution within MMC, enabling further payload delivery.
Combination with DotNetToJScript
To execute arbitrary code, attackers combine the XSS exploit with the DotNetToJScript technique:
- Obfuscation Techniques: The initial sample uses the transformNode method for obfuscation, a technique also seen in recent macro-based attacks. This helps evade ActiveX security warnings.
- Embedded VBScript: The obfuscated script within the MSC file sets environment variables with the target payload.
- DotNetToJScript Execution: The script then uses DotNetToJScript to run an embedded .NET loader, named PASTALOADER, which retrieves the payload from the environment variables and executes it.
PASTALOADER Execution
PASTALOADER is designed to execute the payload in a stealthy manner:
- Payload Injection: PASTALOADER injects the payload into a new instance of dllhost.exe, a legitimate system process, to avoid detection.
- Stealth Techniques: The injection uses DirtyCLR, function unhooking, and indirect syscalls to minimize detection chances.
Final Payload: Cobalt Strike
In the identified sample, the final payload is the Cobalt Strike Beacon, a widely used post-exploitation tool. The injection into dllhost.exe is done carefully to avoid triggering security mechanisms.
Detection Methods
Elastic Security Labs’ Detection Techniques
Elastic Security Labs has developed several detection methods to identify GrimResource activity:
- Suspicious Execution via Microsoft Common Console:
- This detection looks for unusual processes spawned by mmc.exe, indicating potential malicious activity.
- .NET COM Object Created in Non-standard Windows Script Interpreter:
- Detects memory allocations by .NET on behalf of Windows Script Host (WSH) engines, indicative of DotNetToJScript usage.
- Script Execution via MMC Console File:
- Monitors file operations and process behaviors related to MSC file execution, particularly looking for the creation and use of apds.dll references.
- Windows Script Execution via MMC Console File:
- Correlates the creation of temporary HTML files in the INetCache folder, a hallmark of the APDS XSS redirection.
Example EQL Rules
sequence by process.entity_id with maxspan=1m
[process where event.action == "start" and process.executable : "?:\\Windows\\System32\\mmc.exe" and process.args : "*.msc"]
[file where event.action == "open" and file.path : "?:\\Windows\\System32\\apds.dll"]
Detecting Temporary HTML Files:
sequence by process.entity_id with maxspan=1m
[process where event.action == "start" and process.executable : "?:\\Windows\\System32\\mmc.exe" and process.args : "*.msc"]
[file where event.action in ("creation", "overwrite") and process.executable : "?:\\Windows\\System32\\mmc.exe" and file.name : "redirect[?]" and file.path : "?:\\Users\\*\\AppData\\Local\\Microsoft\\Windows\\INetCache\\IE\\*\\redirect[?]"]
Forensic Artifacts
The technique leaves several forensic artifacts, including:
- MSC File Manipulations: Unusual references in StringTable sections.
- Temporary Files: HTML files in the INetCache directory named “redirect[?]”.
- Process Anomalies: Unexpected process creation and memory allocations by mmc.exe and dllhost.exe.
Attackers have developed a new technique to execute arbitrary code in Microsoft Management Console using crafted MSC files. Elastic’s defense-in-depth approach has proven effective against this novel threat. Defenders should implement the provided detection guidance to protect themselves and their customers from GrimResource before it proliferates among commodity threat groups.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











