CVE-2024-31497 has emerged as a critical security flaw affecting PuTTY, a widely used SSH and Telnet client, from versions 0.68 through 0.80, all of which are now confirmed to have a serious vulnerability that compromises cryptographic key security. This vulnerability revolves around the generation of biased ECDSA nonces, which could potentially allow an attacker to recover the NIST P-521 secret keys used by clients.
The Vulnerability Explained
The core of the issue lies in how ECDSA (Elliptic Curve Digital Signature Algorithm) nonces are generated within these versions of PuTTY. The nonces, which should be random to ensure the security of the cryptographic process, were found to be “heavily biased”. This bias in the nonce generation process means that it does not provide the cryptographic randomness required, thereby exposing the private keys to potential recovery by malicious entities.
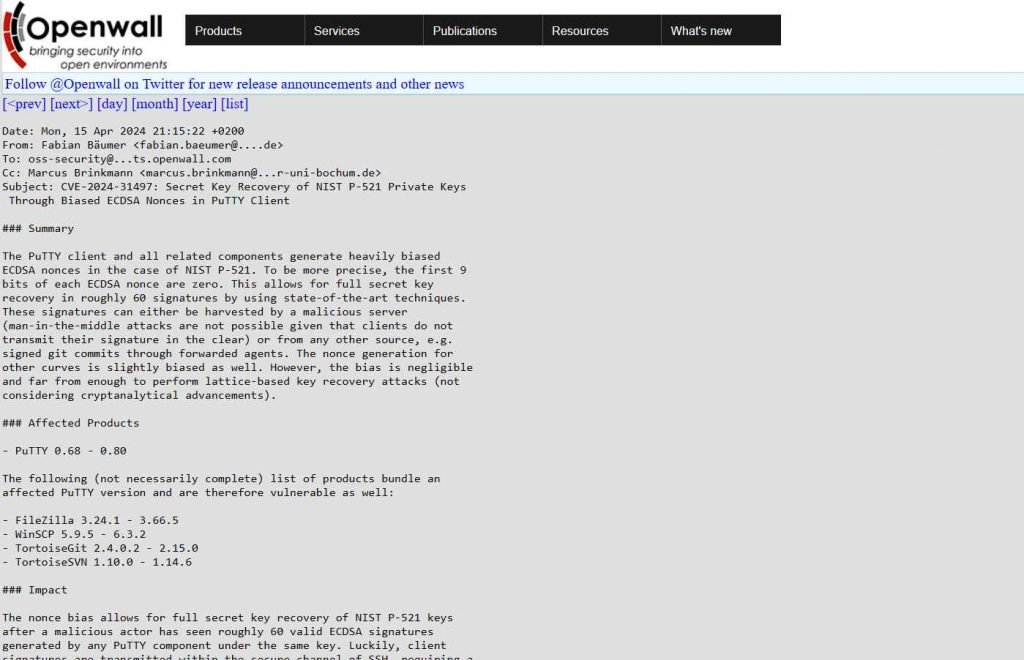
The specific target of this vulnerability is the NIST P-521 elliptic curve, a standard that is commonly used for securing sensitive communications. The flaw was detailed in various security advisories and databases, which highlighted the risk of attackers being able to exploit this vulnerability to gain unauthorized access to encrypted communications.
Exploiting CVE-2024-31497: A Deep Dive into the PuTTY Vulnerability
CVE-2024-31497 has identified a critical security flaw within versions 0.68 through 0.80 of PuTTY, a popular SSH and Telnet client, specifically targeting its ECDSA nonce generation process. This vulnerability exposes the potential for attackers to recover the NIST P-521 secret keys, posing severe risks to encrypted communications.
The Mechanism of the Exploit
The vulnerability arises from the way PuTTY generates ECDSA nonces. In cryptographic protocols, nonces (numbers used once) are crucial for ensuring the security of the encryption process. Ideally, these should be unpredictable and randomly generated. However, in the affected versions of PuTTY, the ECDSA nonces were found to be “heavily biased”, meaning they do not offer the randomness necessary to securely encrypt data.
This bias in nonce generation makes it theoretically possible for an attacker with sufficient resources and access to encrypted communications to use statistical methods to infer the private key associated with a particular set of communications. Specifically, the bias could allow attackers to perform a side-channel attack where they could deduce the private keys after observing a large number of cryptographic operations.
To exploit this vulnerability, an attacker would need to intercept the cryptographic operations performed by a victim using the compromised versions of PuTTY. The attacker could then apply advanced cryptanalytic techniques to exploit the biased nonce values. This would involve complex mathematical calculations and possibly significant computational resources to effectively “guess” the private key through patterns observed in the biased nonces.
Example of Exploiting CVE-2024-31497: Simulated Attack Scenario
To illustrate how CVE-2024-31497 could be exploited, let’s consider a hypothetical attack scenario:
Scenario Background:
Alice is an administrator who uses PuTTY version 0.70 to manage remote servers for her organization. She connects to these servers using an SSH key pair, where the private key is secured on her local machine.
Step 1: Gathering Information
An attacker, Bob, learns that Alice’s organization still uses a vulnerable version of PuTTY. He decides to target her to gain unauthorized access to the secure servers. Bob begins by intercepting Alice’s SSH sessions to the server. This is typically done using a network sniffer on a compromised network or through a man-in-the-middle attack.
Step 2: Intercepting Cryptographic Operations
During each of Alice’s SSH sessions, Bob captures the encrypted data packets, focusing on extracting the ECDSA nonce values used in the cryptographic operations. Since these nonces are biased (due to the CVE-2024-31497 vulnerability), they do not vary as randomly as they should.
Step 3: Exploiting the Bias
Bob uses a custom-developed script to analyze the captured nonces. The script employs statistical algorithms to detect patterns and irregularities in the nonces that should be random. These patterns indicate the biased nature of the nonce generation in PuTTY, making the private key more predictable.
Step 4: Cracking the Private Key
Using the patterns observed, Bob applies a series of advanced mathematical calculations designed to reverse-engineer Alice’s private key. This type of cryptanalysis exploits the weaknesses inherent in the biased nonces, gradually narrowing down the possible values of the private key.
Step 5: Gaining Unauthorized Access
Once Bob successfully deduces Alice’s private key, he uses it to authenticate himself on the SSH server as if he were Alice. He can now execute commands, access confidential information, and potentially implant further malware to maintain access or affect other parts of the network.
Digital Signature Exploit Mechanism in SSH and Git
- Digital Signature Creation and Verification:
- Digital Signature Creation: A digital signature is created using a user’s private key. This process involves the private key signing data (in this case, a Git commit), which effectively “seals” the data with proof that it was signed by the holder of the private key.
- Digital Signature Verification: The corresponding public key, which is known to others, can be used to verify that the signature was made by the matching private key without exposing the private key itself. This process confirms the identity of the user and ensures the integrity and authenticity of the signed data.
Exploitation Explained
- Collecting Signatures for Exploitation:
- Via SSH Server Logs: If an attacker controls or compromises an SSH server, they can collect the digital signatures generated during user logins. These signatures, when created using compromised or weak cryptographic methods, can be analyzed to reveal patterns or weaknesses.
- Via Signed Git Commits: A more practical approach, as mentioned, involves collecting signatures from signed Git commits. If Git is configured to use SSH keys for signing commits and these commits are pushed to a public repository (like GitHub), the signatures are easily accessible to anyone.
- Exploiting Vulnerabilities in Signature Generation:
- In the context of PuTTY and Pageant, if there is a vulnerability in how these tools generate signatures (such as using biased nonces as in CVE-2024-31497), an attacker can potentially exploit this to deduce the private key used for signing.
- Calculation of Private Key: According to the provided information, attackers might need around 58 signatures to calculate a target’s private key accurately. This calculation is likely based on the ability to exploit flaws in the nonce generation process during signature creation.
Specific Use Case: PuTTY and Pageant with Git
- PuTTY and Pageant Setup for Git:
- Configuration: Users might configure Git to use Pageant as an SSH agent, where Pageant manages their SSH keys. When making Git commits, these commits are signed using the SSH key provided by Pageant.
- Vulnerability Risk: If Pageant is using a version of PuTTY affected by CVE-2024-31497, then the signatures it generates for Git commits might be vulnerable to being exploited, allowing attackers to eventually recover the private key.
Implications of the Exploit
The recovery of NIST P-521 secret keys via this exploit could allow unauthorized parties to decrypt sensitive information, impersonate legitimate users, or perform a range of other malicious activities. Given PuTTY’s extensive use in managing secure communications for critical infrastructure, this vulnerability could have widespread implications, potentially affecting a wide array of sectors including government, finance, and healthcare.
Security Responses and Fixes
CVE-2024-31497 specifically affects PuTTY software versions 0.68 through 0.80. The vulnerability is tied to the implementation of the ECDSA nonce generation within these specific versions of PuTTY. As such, other software products are not directly impacted by this CVE unless they somehow incorporate the same flawed code or similar nonce generation mechanisms that were used in PuTTY.
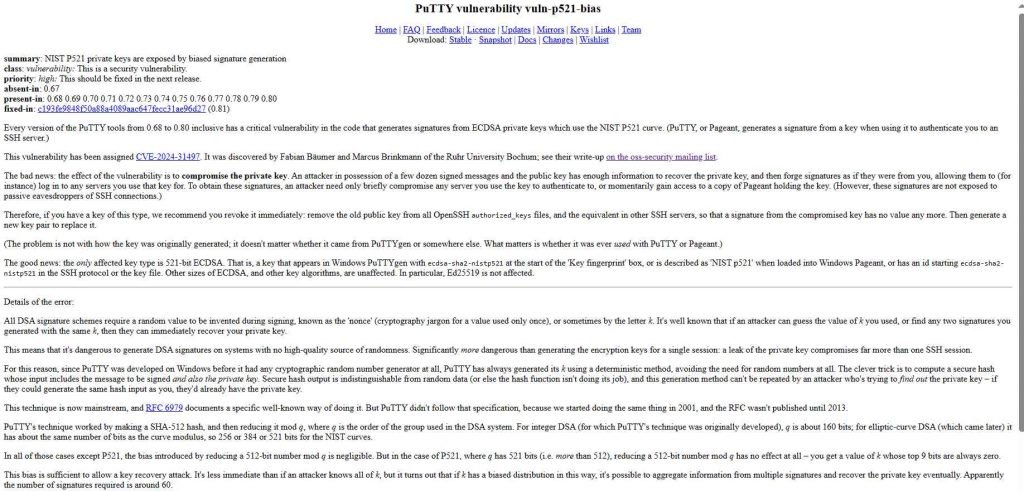
However, here’s a broader perspective on other software types that could potentially be impacted by similar vulnerabilities:
- SSH Clients:
- Other SSH clients might also suffer from similar vulnerabilities if they use flawed or biased ECDSA nonce generation methods. Users should ensure they use up-to-date versions and apply patches regularly.
- Cryptographic Libraries:
- Libraries that implement ECDSA and other cryptographic algorithms could be vulnerable if they have similar issues with nonce generation. Examples include OpenSSL, Libgcrypt, and others which have previously had vulnerabilities related to cryptographic nonce handling.
- VPN Software:
- VPNs that use custom or outdated cryptographic implementations may be vulnerable to similar issues if they do not use secure, random nonce generation methods in their cryptographic protocols.
- Secure Communication Applications:
- Applications that facilitate secure messaging and data transmission, relying on ECDSA for encryption, could potentially be exposed if their nonce generation is biased or predictable.
- Financial Transaction Systems:
- Systems that handle e-commerce and financial transactions using ECDSA for transaction signing could be at risk if they inherit or fail to properly implement secure nonce generation practices.
Best Practices for Prevention:
- Regular Updates and Patching: Regularly updating all software to the latest version is critical. This not only applies to PuTTY but to all software that involves cryptographic operations.
- Security Audits: Regularly conduct security audits of the cryptographic practices and implementations used within your organization’s software stack.
- Vulnerability Scanning: Use vulnerability scanners and penetration testing tools to identify and mitigate risks associated with cryptographic implementations.
By keeping an eye on updates related to cryptographic practices and implementing robust security measures, organizations can safeguard against vulnerabilities similar to CVE-2024-31497 and protect their data integrity and privacy.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











