In the evolving landscape of cybersecurity threats, a new class of Distributed Denial of Service (DDoS) attacks has emerged, exploiting the intricate dance between network services. This phenomenon, known as application-layer loops, presents a sophisticated challenge that goes beyond traditional network-layer defenses. By manipulating two network services into an endless exchange of error messages, attackers can create a self-sustaining cycle of communication that puts undue stress on both the servers involved and the network infrastructure connecting them.
The Mechanism of Application-Layer Loops
Application-layer loops occur when two network services are configured to respond to each other’s messages indefinitely. A practical example of this vulnerability involves two DNS resolvers that, upon receiving an error message, reply with another error message. An attacker can exploit this by sending a single, IP-spoofed DNS error message to these resolvers, triggering an infinite loop of error messages between them. This not only burdens the servers but also saturates the network links between them, potentially leading to service degradation or outright failure.
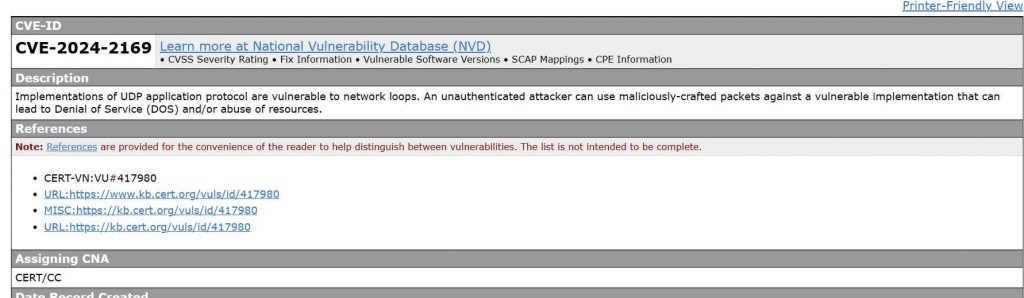
This type of vulnerability has been identified in various implementations of TFTP, DNS, and NTP protocols, as well as in six UDP-based legacy protocols including QOTD, Chargen, and Echo, which have been vulnerable by design since their inception. The attack is possible due to a vulnerability, currently tracked as CVE-2024-2169, in the implementation of the UDP protocol, which is susceptible to IP spoofing and does not provide sufficient packet verification.
Scenarios of Exploitation
The exploitation of application-layer loops opens up several attack scenarios, each with its own set of challenges for cybersecurity defenses:
Scenario A: Direct Attack on a Loop Server
An attacker targets a loop server by creating multiple loops with other servers, concentrating the attack on a single point. This can exhaust the server’s bandwidth or computational resources. Patching the server to prevent loop patterns is a crucial defense strategy.
Scenario B: Straining the Network Backbone
By pairing hosts within a network’s backbone, attackers can generate millions of loops, aiming to overload the network infrastructure. Networks that implement ingress filtering for IP-spoofed traffic can mitigate such attacks from external sources.
Scenario C: Targeting Network Links
Attackers may also orchestrate loops to congest specific Internet links, including a network’s uplink or other critical paths. This strategy requires careful pairing of internal and external loop hosts to maximize stress on the targeted link.
Scenario D: Self-Amplifying Loops
In rare instances, loop servers respond with multiple messages, leading to self-amplifying loops. These loops not only persist indefinitely but also increase in intensity, posing a significant threat even when defensive measures cause packet loss.
The Scale of Vulnerability
The operator community faces a daunting challenge, with vulnerable servers identified across TFTP (~23k hosts), DNS (~63k), NTP (~89k), Echo/RFC862 (~56k), Chargen/RFC864 (~22k), and QOTD/RFC865 (~21k). The widespread nature of these vulnerabilities, coupled with the difficulty in attributing the majority of these systems to specific products or software, complicates the mitigation process.
Action Items for Mitigation
To address this emerging threat, several action items have been proposed:
- Notification of ASNs: Informing Autonomous System Numbers (ASNs) about systems within their networks that are susceptible to DoS attacks. Initiatives like Shadowserver’s one-time report to subscribed organizations are steps in the right direction.
- Assistance in Disclosure: Facilitating the disclosure process with affected vendors and developers to identify and rectify vulnerable software products.
- Preventive Measures: Updating or shutting down vulnerable services, restricting service access, and identifying responsible software or products are crucial steps in reducing the attack landscape.
- Reactive Measures: Disrupting the loops through packet loss, employing Quality of Service (QoS) adjustments, rate limiting, and detecting loop patterns are effective strategies in mitigating ongoing attacks.
The discovery of application-layer loops as a potential vector for DDoS attacks underscores the complexity of modern cybersecurity challenges. Unlike network-layer loops, which can be mitigated with existing defenses like TTL hop limits, application-layer loops require a combination of proactive and reactive strategies to prevent exploitation. As cyber threats continue to evolve, the cybersecurity community must remain vigilant, fostering collaboration and innovation to protect critical infrastructure and ensure the integrity of digital services.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











