The Cybersecurity and Infrastructure Security Agency (CISA), in collaboration with the National Security Agency (NSA), Federal Bureau of Investigation (FBI), and international partners, has issued a critical advisory warning about the activities of People’s Republic of China (PRC) state-sponsored cyber actors. These actors, identified under the moniker Volt Typhoon among others, have been implicated in sophisticated cyber operations aimed at pre-positioning within IT networks of U.S. critical infrastructure. This strategic positioning is assessed as preparation for potential disruptive or destructive cyberattacks in the context of escalating geopolitical tensions or conflict with the United States.
The Threat Actors: Volt Typhoon
Volt Typhoon has successfully infiltrated the networks of critical infrastructure sectors, including Communications, Energy, Transportation Systems, and Water and Wastewater Systems, across the continental United States and its territories. The actors’ choice of targets and operational patterns diverge from conventional cyber espionage, indicating a clear intent towards enabling disruption of operational technology (OT) functions.
Tactics, Techniques, and Procedures (TTPs)
Volt Typhoon’s operations are characterized by the use of “living off the land” (LOTL) techniques, leveraging valid accounts and maintaining strong operational security to ensure long-term, undetected persistence within compromised environments. The actors conduct extensive reconnaissance to tailor their TTPs to the victim’s environment and have been observed maintaining access to some IT environments for at least five years.
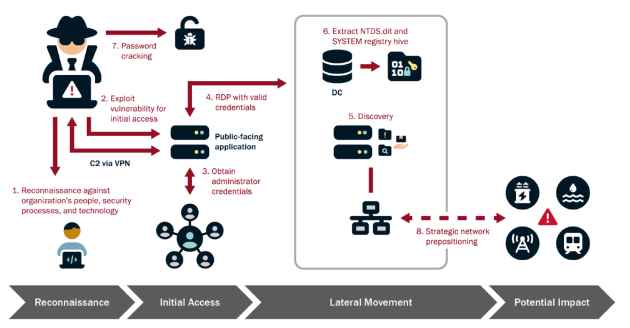
Key stages of Volt Typhoon’s activity include:
- Reconnaissance: Volt Typhoon’s operations begin with meticulous reconnaissance, gathering detailed intelligence on target organizations. This phase is critical for understanding the network architecture, security measures, typical user behaviors, and identifying key network and IT staff. The actors use various methods for reconnaissance, including web searches on victim-owned sites and leveraging search engines like FOFA, Shodan, and Censys to find exposed infrastructure. This extensive pre-compromise intelligence gathering is tailored to enhance their operational security and ensure successful penetration and persistence within the target environment.
- Initial Access: Gaining initial access to the IT network is a pivotal step in Volt Typhoon’s operations. The actors commonly exploit known or zero-day vulnerabilities in public-facing network appliances, such as routers, VPNs, and firewalls. The use of publicly available exploit code for known vulnerabilities is frequent, but the actors are also adept at discovering and exploiting zero-day vulnerabilities. This approach allows them to establish a foothold within the network, from which they can launch further intrusion activities.
- Credential Access and Privilege Escalation:Once inside the network, Volt Typhoon aims to obtain administrator credentials, often by exploiting privilege escalation vulnerabilities in the operating system or network services. In some instances, credentials are obtained from insecurely stored information on a public-facing network appliance. With these credentials, the actors can move laterally within the network, accessing critical systems and data.
- Lateral Movement:Using valid administrator credentials, Volt Typhoon moves laterally to the domain controller and other critical devices via remote access services such as Remote Desktop Protocol (RDP). This step is crucial for expanding their access within the network and positioning themselves for further exploitation and disruption.
- Discovery:Post-compromise, Volt Typhoon conducts discovery activities within the victim’s network, leveraging Living Off the Land (LOTL) binaries for stealth. This includes using PowerShell to perform targeted queries on Windows event logs, focusing on specific users and periods. These queries facilitate the discreet extraction of security event logs, allowing the actors to gather critical information while minimizing detection.
- Domain Compromise:Achieving full domain compromise is a key objective for Volt Typhoon. The actors frequently employ the Volume Shadow Copy Service (VSS) to access the
NTDS.ditfile from the domain controller. This file contains critical Active Directory data, including user accounts and passwords (in hashed form), which can be leveraged for further exploitation. - Persistence:Volt Typhoon relies on valid credentials for persistence within the compromised environment. This approach allows them to maintain long-term, undiscovered access to the network, enabling them to re-target the same organizations over extended periods.
- Defense Evasion:The actors’ strong operational security is evident in their primary use of LOTL techniques for defense evasion. By camouflaging their malicious activity with typical system and network behavior, they can circumvent simplistic endpoint security capabilities. Additionally, Volt Typhoon actors obfuscate their malware and engage in targeted log deletion to conceal their actions within the compromised environment.
Mitigation and Recommendations
The advisory urges critical infrastructure organizations to apply recommended mitigations and actively hunt for similar malicious activity. These measures are primarily intended for IT and OT administrators and include updating to the latest security patches, enhancing monitoring and detection capabilities, and applying best practices for identity and access management.
International Implications
While the direct threat to Canada’s critical infrastructure from PRC state-sponsored actors is assessed as lower than that to the U.S., the interconnected nature of critical infrastructure means that disruptions in the U.S. could have cascading effects on Canada and potentially other allied nations. Australian and New Zealand critical infrastructure is also considered vulnerable to similar activities from PRC state-sponsored actors.
The advisory from CISA, NSA, and FBI, supported by international cybersecurity agencies, highlights the sophisticated and persistent threat posed by PRC state-sponsored cyber actors to U.S. critical infrastructure. The detailed analysis of Volt Typhoon’s activities underscores the necessity for vigilance, proactive security measures, and international cooperation to mitigate the risks of disruptive or destructive cyberattacks against critical infrastructure sectors.
For organizations within the targeted sectors, adherence to the recommended mitigations and engagement with cybersecurity authorities for incident response and reporting is crucial. As geopolitical tensions continue to influence the cyber threat landscape, the resilience of critical infrastructure against state-sponsored cyber threats remains a top priority for national security.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











