Recent news about a critical vulnerability in Jenkins, identified as CVE-2024-23897, has raised significant concerns in the cybersecurity community. This vulnerability has been highlighted due to the publication of a Proof of Concept (PoC) exploit, which has increased the risks associated with this issue.
Overview of the Vulnerability (CVE-2024-23897)
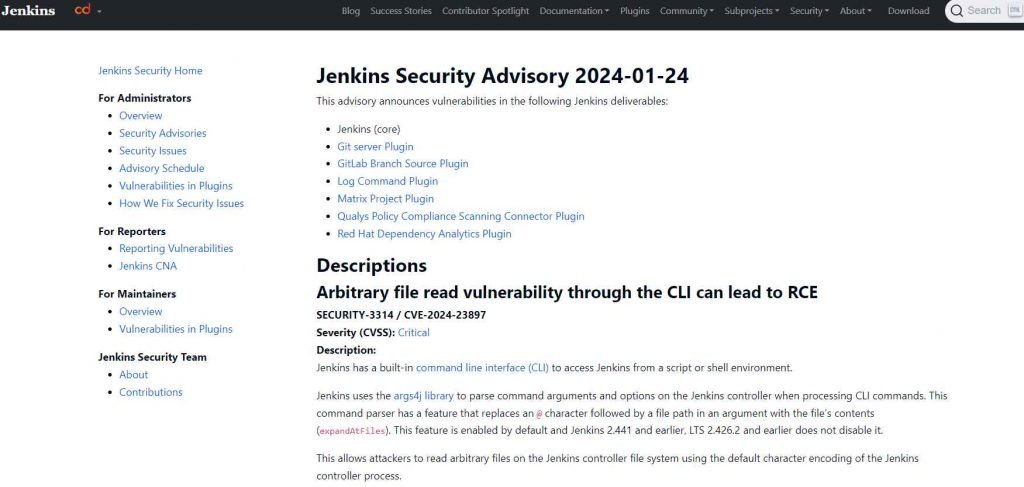
The critical vulnerability in Jenkins, CVE-2024-23897, allows unauthenticated attackers with ‘overall/read’ permission to read data from arbitrary files on the Jenkins controller file system. This flaw poses a severe risk as it enables attackers to gain access to sensitive information, potentially leading to further exploitation of the system.
The exploit for the Jenkins vulnerability, identified as CVE-2024-23897, is a critical security flaw that has significant implications. To understand this exploit, it’s important to break down its components and how it operates:
Nature of the Vulnerability
- Jenkins System: Jenkins is an open-source automation server widely used in continuous integration and continuous delivery (CI/CD) pipelines. It helps automate various aspects of software development, such as building, testing, and deploying applications.
- Vulnerability Type: CVE-2024-23897 is a Remote Code Execution (RCE) vulnerability. RCE vulnerabilities are particularly severe because they allow an attacker to execute arbitrary code on the victim’s system remotely.
How the Exploit Works
- Exploitation of Permissions: The vulnerability allows unauthenticated attackers with ‘overall/read’ permissions to read data from arbitrary files on the Jenkins controller file system. This means that even without full administrative privileges, attackers can access sensitive information.
- Reading Arbitrary Files: The exploit enables attackers to read the first few lines of arbitrary files on the Jenkins controller. This could include configuration files, source code, credentials, or any other sensitive data stored on the server.
- Potential for Further Exploitation: While the primary capability is to read files, the exposure of sensitive data could lead to further exploitation. For instance, if credentials are obtained, attackers could escalate their access privileges.
The Criticality of the Exploit
- Unauthenticated Access: The fact that the exploit can be triggered by unauthenticated users makes it particularly dangerous. It lowers the barrier for attackers, as they do not need to compromise an account before exploiting this vulnerability.
- Ease of Execution: The release of a Proof of Concept (PoC) means that the exploit can be replicated easily by attackers who have access to this PoC. This increases the likelihood of widespread exploitation.
Mitigation and Response
- Patch Availability: Jenkins has released a patch to address this vulnerability. It is crucial for users and administrators of Jenkins to apply this patch immediately to mitigate the risk.
- Security Best Practices: Regularly updating software, monitoring systems for unusual activities, and following security best practices are essential steps in protecting against such exploits.
Security experts have developed curated Sigma rules to detect exploitation attempts of this vulnerability. These rules are crucial for organizations using Jenkins, as they provide a way to identify and respond to any malicious activities related to CVE-2024-23897.
The Severity of the Issue
Rated as critical, this vulnerability has garnered attention due to the ease with which it can be exploited and the potential damage it can cause. The publication of the PoC exploit has escalated the situation, as it provides attackers with a ready-made tool to exploit this vulnerability.
Response from the Jenkins Community
The Jenkins community has been quick to respond to this threat. A patch has been released to address the vulnerability, and users are strongly advised to update their Jenkins installations as soon as possible. The prompt release of the patch highlights the community’s commitment to security and its proactive approach to addressing such critical issues.
Real-World Implications
There have been reports of the PoC exploits for the Jenkins vulnerability being targeted in the wild. This real-world exploitation underscores the importance of immediate action by organizations using Jenkins. Delaying the application of the patch could leave systems vulnerable to attacks, which could lead to severe consequences.
The discovery and subsequent publication of the PoC exploit for the critical Jenkins vulnerability, CVE-2024-23897, serve as a stark reminder of the importance of cybersecurity vigilance. Organizations using Jenkins must prioritize the application of the latest patch to protect their systems from potential exploitation. The situation also highlights the need for continuous monitoring and rapid response mechanisms to address emerging cybersecurity threats.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











