SMTP stands for Simple Mail Transfer Protocol. It’s a protocol used for sending emails across the Internet. SMTP operates on a push model, where the sending server pushes the email to a receiving server or an intermediary mail server. Here are some basic concepts associated with SMTP:
- Sending and Receiving Servers: SMTP involves at least two servers: the sending mail server and the receiving mail server. The sending server initiates the process.
- SMTP Ports: Commonly, SMTP uses port 25 for non-encrypted communication and port 587 for encrypted communication (STARTTLS). Some servers also use port 465 for SSL/TLS encrypted communication.
- SMTP Commands and Responses: SMTP communication is based on commands and responses. Common commands include
HELO(orEHLOfor Extended SMTP),MAIL FROMto specify the sender,RCPT TOfor the recipient, andDATAfor the body of the email. Responses from the server indicate success or failure of these commands. - MIME (Multipurpose Internet Mail Extensions): Although SMTP is limited to sending text, MIME standards enable SMTP to send other types of data like images, audio, and video by encoding them into text format.
- SMTP Authentication: This is used to authenticate a user who wants to send an email. It helps in preventing unauthorized access to the email server.
- SMTP Relay: This refers to the process of transferring an email from one server to another. When an SMTP server forwards an email to another server for further delivery, it’s called relaying.
- SMTP in Email Clients: Email clients (like Outlook, Thunderbird) use SMTP to send emails. These clients require configuration of SMTP settings (server address, port, authentication) to send emails.
- Limitations and Security: SMTP itself does not encrypt email content; it relies on other protocols (like SSL/TLS) for security. Also, SMTP does not inherently include strong mechanisms to authenticate the sender, which has led to issues like spam and phishing.
- Interaction with Other Protocols: SMTP is typically used alongside POP3 or IMAP, which are protocols used for retrieving emails from a mail server.
- Use in Modern Email Systems: Despite its age, SMTP remains a fundamental part of the email infrastructure in the Internet and is used in virtually all email systems today.
SMTP Smuggling
SMTP Smuggling refers to a technique used in network security to bypass security measures by exploiting vulnerabilities in the Simple Mail Transfer Protocol (SMTP). SMTP is the standard protocol used for sending emails across the Internet. Smuggling in this context typically involves manipulating the SMTP conversation in a way that allows an attacker to inject malicious commands or payloads into an email message. These payloads might be overlooked by security systems that are not properly configured to handle anomalous SMTP traffic.
There are several ways SMTP smuggling can be executed:
- Command Injection: By inserting additional SMTP commands into message fields (like the ‘MAIL FROM’ or ‘RCPT TO’ fields), an attacker might trick a server into executing commands it shouldn’t.
- CRLF Injection: SMTP commands are typically separated by a carriage return and line feed (CRLF). If an attacker can inject CRLF sequences into a message, they might be able to append additional commands or modify the behavior of the email server.
- Content Smuggling: This involves hiding malicious content within an email in a way that evades detection by security systems, which might scan emails for known threats.
Email authentication mechanisms
Email authentication mechanisms like SPF, DKIM, and DMARC are crucial in the fight against email spoofing and phishing. They help verify the authenticity of the sender and ensure the integrity of the message. Here’s a basic overview of each:
1. SPF (Sender Policy Framework)
- Purpose: SPF is used to prevent sender address forgery. It allows the domain owner to specify which mail servers are permitted to send email on behalf of their domain.
- How It Works: The domain owner publishes SPF records in their DNS. These records list the authorized sending IP addresses. When an email is received, the receiving server checks the SPF record to verify that the email comes from an authorized server.
- Limitations: SPF only checks the envelope sender (return-path) and not the header (From:) address, which is often what the recipient sees.
2. DKIM (DomainKeys Identified Mail)
- Purpose: DKIM provides a way to validate a domain name identity that is associated with a message through cryptographic authentication.
- How It Works: The sending server attaches a digital signature linked to the domain to the header of the email. The receiving server then uses the sender’s public key (published in their DNS) to verify the signature.
- Advantages: DKIM verifies that parts of the email (including attachments) have not been altered in transit.
3. DMARC (Domain-based Message Authentication, Reporting, and Conformance)
- Purpose: DMARC builds on SPF and DKIM. It allows the domain owner to specify how an email that fails SPF and DKIM checks should be handled.
- How It Works: DMARC policies are published in DNS. These policies instruct the receiving server what to do with mail that doesn’t pass SPF or DKIM checks (e.g., reject the mail, quarantine it, or pass it with a note).
- Benefits: DMARC also includes reporting capabilities, letting senders receive feedback on how their email is being handled.
Combined Effectiveness
- Complementary Roles: SPF, DKIM, and DMARC work together to improve email security. SPF validates the sending server, DKIM validates the message integrity, and DMARC tells receivers what to do if the other checks fail.
- Combat Spoofing and Phishing: By using these mechanisms, organizations can significantly reduce the risk of their domains being used for email spoofing and phishing attacks.
- Adoption and Configuration: Proper configuration of these protocols is critical. Misconfiguration can lead to legitimate emails being rejected or marked as spam.
Implementation
- DNS Records: All three require DNS records to be set up. SPF and DMARC are text records, while DKIM uses a TXT record for the public key.
- Email Servers and Services: Many email services and servers support these protocols, but they usually require manual setup and configuration by the domain administrator.
Overall, SPF, DKIM, and DMARC are essential tools in the email administrator’s toolkit for securing email communication and protecting a domain’s reputation.
In a groundbreaking discovery, Timo Longin, in collaboration with the SEC Consult Vulnerability Lab, has unveiled a novel exploitation technique in the realm of email security. This technique, known as SMTP smuggling, poses a significant threat to global email communication by allowing malicious actors to send spoofed emails from virtually any email address.
Discovery of SMTP Smuggling: The concept of SMTP smuggling emerged from a research project led by Timo Longin, a renowned figure in the cybersecurity community known for his work on DNS protocol attacks. This new technique exploits differences in how SMTP servers interpret protocol rules, enabling attackers to bypass standard email authentication methods like SPF (Sender Policy Framework).
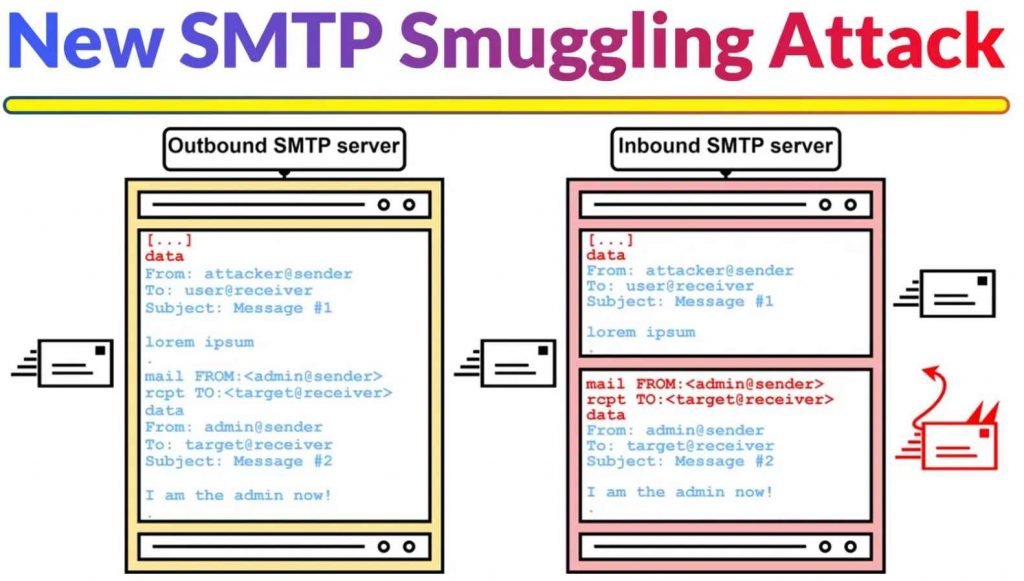
How SMTP Smuggling Works: SMTP smuggling operates by exploiting the interpretation differences of the SMTP protocol among various email servers. This allows attackers to ‘smuggle’ or send spoofed emails that appear to originate from legitimate sources, thereby passing SPF alignment checks. The research identified two types of SMTP smuggling: outbound and inbound, affecting millions of domains and email servers.
Technical Insights: Understanding SMTP Smuggling in Depth
SMTP Smuggling Exploited: SMTP smuggling takes advantage of discrepancies in how different email servers interpret the SMTP protocol. Specifically, it targets the end-of-data sequence, which signifies the end of an email message. In a standard SMTP session, this sequence is represented by a line with only a period (.) character, preceded by a carriage return and a line feed (<CR><LF>.<CR><LF>). However, variations in interpreting this sequence can lead to vulnerabilities.
Outbound and Inbound Smuggling: The research identified two types of SMTP smuggling: outbound and inbound. Outbound smuggling involves sending emails from a compromised server, while inbound smuggling pertains to receiving emails on a server that misinterprets the end-of-data sequence. Both types can be exploited to send spoofed emails that appear to come from legitimate sources.
Exploiting SPF Alignment Checks:
The concept of “Exploiting SPF Alignment Checks” in the context of SMTP smuggling revolves around manipulating the Sender Policy Framework (SPF) checks to send spoofed emails. SPF is an email authentication method designed to prevent sender address forgery. Here’s a detailed explanation of how SPF alignment checks can be exploited through SMTP smuggling:
Understanding SPF:
- SPF Basics: SPF allows domain owners to specify which mail servers are permitted to send emails on behalf of their domain. This is done by publishing SPF records in DNS. When an email is received, the recipient server checks the SPF record to verify if the email comes from an authorized server.
- SPF Check Process: The SPF check typically involves comparing the sender’s IP address (found in the SMTP envelope) against the IP addresses listed in the domain’s SPF record. If the IP address matches one in the SPF record, the email passes the SPF check.
Exploitation through SMTP Smuggling:
- Manipulating the ‘MAIL FROM’ Address: In SMTP smuggling, attackers manipulate the ‘MAIL FROM’ address in the SMTP envelope. This address is used for SPF validation. By carefully crafting this address, attackers can pass the SPF check even when sending from an unauthorized server.
- Discrepancy between ‘MAIL FROM’ and ‘From’ Header: There’s often a discrepancy between the ‘MAIL FROM’ address in the SMTP envelope (used for SPF checks) and the ‘From’ header in the email body (which the recipient sees). SMTP smuggling exploits this by setting the ‘MAIL FROM’ address to a domain that passes the SPF check, while the ‘From’ header is spoofed to appear as if the email is from a different, often trusted, domain.
- Bypassing SPF Alignment: The key to this exploitation is the difference in how various mail servers interpret and process SMTP protocol rules. By smuggling in additional commands or data, attackers can make an email appear to come from a legitimate source, thus bypassing SPF alignment checks.
- Consequences: This exploitation can lead to successful phishing attacks, as the email appears to be from a trusted source, despite being sent from an unauthorized server. Recipients are more likely to trust and act upon these emails, leading to potential security breaches.
Technical Experimentation
The “Technical Experimentation” aspect of the SMTP smuggling research conducted by SEC Consult involved a series of methodical tests and analyses to understand how different email servers handle SMTP protocol, particularly focusing on the end-of-data sequence.
Objective of the Experimentation:
The primary goal was to identify discrepancies in how outbound (sending) and inbound (receiving) SMTP servers interpret the SMTP protocol, especially the end-of-data sequence. This sequence is crucial as it signifies the end of an email message.
Experiment Setup:
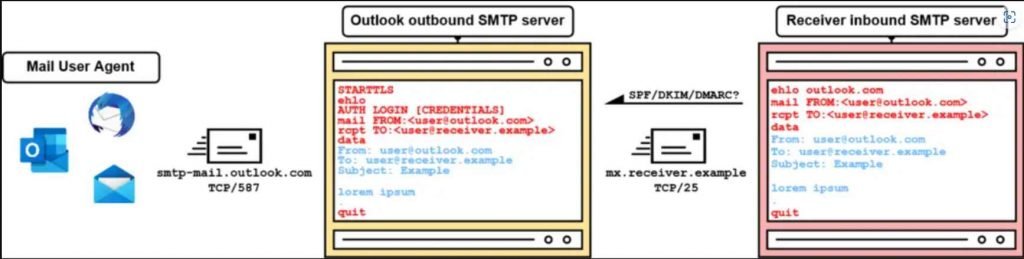
- Selection of Email Providers: The researchers selected a range of public email providers that support mail submissions via SMTP. This included popular services like Outlook.com, Gmail, GMX, iCloud, and others.
- SMTP Analysis Server: A specialized SMTP analysis server was set up to receive emails from these providers. This server played a critical role in observing how different SMTP servers handle various SMTP commands and sequences.
- SMTP Analysis Client: An SMTP analysis client was used to send emails through the outbound SMTP servers of the selected providers. This client was configured to vary the SMTP commands and sequences used in the emails.
Key Areas of Focus:
- End-of-Data Sequence Variations: The researchers experimented with different end-of-data sequences, such as
<LF>.<LF>(Line Feed) instead of the standard<CR><LF>.<CR><LF>(Carriage Return, Line Feed). The goal was to see if outbound servers would process these non-standard sequences differently. - Server Responses to DATA Command: Different responses from email providers to the DATA SMTP command were observed. These responses provided insights into how each server might handle end-of-data sequences.
- Operating System Differences: The experiment also considered how different operating systems interpret “a line by itself.” For example, Windows uses
<CR><LF>to denote the end of a line, while Unix/Linux systems use<LF>. This difference could affect how email servers process the end-of-data sequence.
Experiment Execution:
- Sending Test Emails: The SMTP analysis client sent test emails through the outbound SMTP servers of the selected providers, using various end-of-data sequences.
- Observing Responses: The inbound SMTP analysis server received these emails and recorded how each outbound server handled the different sequences.
- Identifying Anomalies: The researchers looked for anomalies where outbound servers did not correctly interpret or filter non-standard end-of-data sequences, and inbound servers accepted them as valid.
Findings:
The experimentation revealed that some SMTP servers did not conform to the standard interpretation of the SMTP protocol, particularly in handling end-of-data sequences. This non-conformity opened the door for SMTP smuggling, where attackers could insert additional SMTP commands into email content.
Case Study – GMX SMTP Server
A notable example of SMTP smuggling was demonstrated using GMX’s SMTP server. The researchers were able to send an email with a specially crafted end-of-data sequence that the GMX server did not filter out. This allowed them to insert additional SMTP commands into the email content, which were then executed by the recipient server, effectively ‘smuggling’ malicious commands or content.
Exploitation Technique:
- Manipulating End-of-Data Sequence: The researchers experimented with different end-of-data sequences, such as
<LF>.<LF>instead of the standard<CR><LF>.<CR><LF>. - Observing GMX Server Response: It was observed that when a specific sequence (
<LF>.<CR><LF>) was sent to the GMX outbound SMTP server, it passed this sequence unfiltered to the inbound SMTP server.
Successful SMTP Smuggling:
- Breaking Out of Message Data: By using the
<LF>.<CR><LF>sequence, the researchers were able to ‘break out’ of the message data at the inbound SMTP server. This meant that anything following this sequence could be interpreted as a separate SMTP command or additional email content. - Demonstration of Vulnerability: This technique allowed the researchers to effectively insert additional SMTP commands into the email content, demonstrating a successful SMTP smuggling attack.
The research team’s first successful SMTP smuggling exploit was demonstrated using GMX’s SMTP server. This breakthrough confirmed the feasibility of the technique and its potential to compromise email security on a large scale. SMTP smuggling represents a new frontier in email spoofing, challenging existing security measures and highlighting the need for continuous vigilance in the cybersecurity domain. The discovery underscores the importance of regular security audits and updates to protect against emerging threats. The discovery of SMTP smuggling has significant implications for email security. Vulnerabilities were identified in major email services, including Microsoft and GMX, which were promptly addressed. However, SEC Consult has issued a warning to organizations using Cisco Secure Email, urging them to update their configurations to mitigate this vulnerability.
Technical and Security Mitigations:
- Patch and Update Systems: Regularly update and patch email servers and related software. Providers should ensure their systems are up-to-date with the latest security patches that address known vulnerabilities, including those related to SMTP smuggling.
- Enhance Email Authentication: Implement and enforce advanced email authentication protocols like DKIM (DomainKeys Identified Mail) and DMARC (Domain-based Message Authentication, Reporting, and Conformance). These protocols provide additional layers of verification, ensuring that the email’s sender is legitimate and that the message content hasn’t been tampered with.
- Configure Email Servers Correctly: Ensure that email servers, especially those handling outbound and inbound emails, are configured correctly to handle SMTP protocol standards, particularly the end-of-data sequence. This involves strict adherence to protocol specifications to prevent any ambiguity in interpretation.
- Use Advanced Email Filtering Solutions: Employ advanced email filtering solutions that can detect and block spoofed emails. These solutions often use machine learning and other advanced techniques to identify anomalies in email messages that might indicate a spoofing attempt.
- Regular Security Audits: Conduct regular security audits of email infrastructure to identify and rectify potential vulnerabilities. This should include a review of server configurations, authentication mechanisms, and update protocols.
SMTP smuggling represents a significant advancement in the understanding of email protocol vulnerabilities. It challenges the existing security paradigms and calls for a reevaluation of email security strategies. As the cybersecurity community works to address these vulnerabilities, this discovery serves as a crucial reminder of the dynamic and evolving nature of cyber threats.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











