Mobile network data might be one of our most recent and thorough dossiers. Our mobile phones are linked to these networks and expose our demographics, social circles, purchasing habits, sleeping patterns, where we live and work, and travel history. Technical weaknesses in mobile communications networks threaten this aggregate data. Such vulnerabilities may reveal private information to numerous varied players and are closely tied to how mobile phones roam among cell providers for travel. These vulnerabilities are usually related to signalling signals carried across telecommunications networks, which expose phones to possible location disclosure.
Telecommunications networks use private, open signalling links. These connections enable local and international roaming, allowing mobile phones to smoothly switch networks. These signalling protocols also enable networks to obtain user information including if a number is active, whether services are accessible, to which national network they are registered, and where they are situated. These connections and signalling protocols are continually targeted and exploited by surveillance actors, exposing our phones to several location disclosure techniques.
Most illegal network-based location disclosure is achievable because mobile telecommunications networks interact. Foreign intelligence and security agencies, commercial intelligence businesses, and law enforcement routinely want location data. Law enforcement and intelligence agencies may get geolocation information secretly using tactics similar to those employed by criminals. We shall refer to all of these players as ‘surveillance actors’ throughout this paper since they are interested in mobile geolocation surveillance.
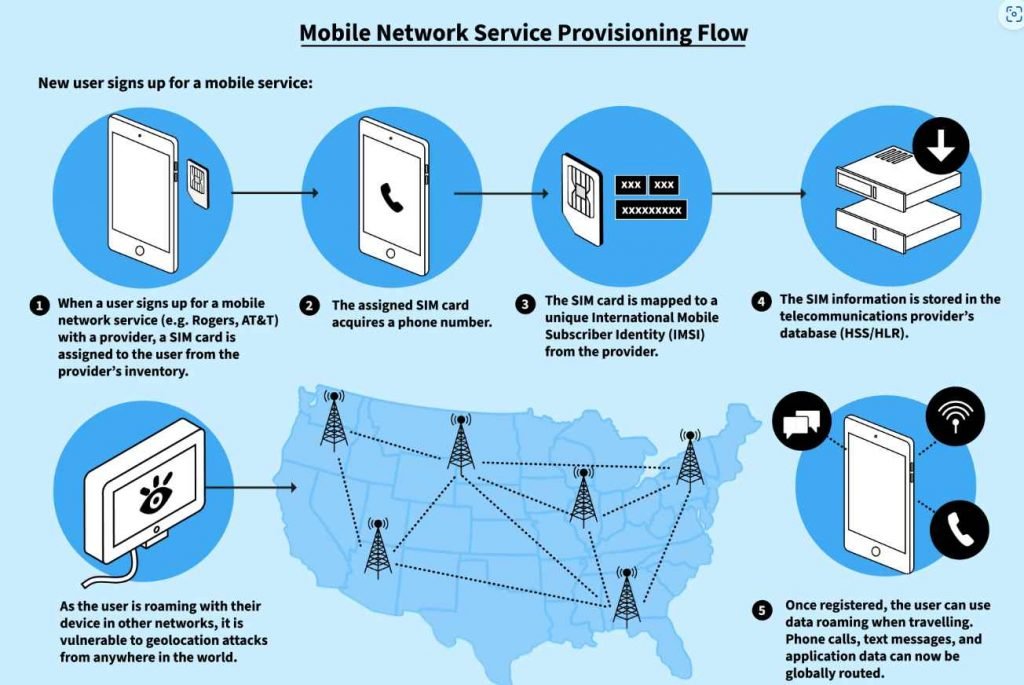
Despite worldwide 4G network adoption and fast developing 5G network footprint, many mobile devices and their owners use 3G networks. The GSMA, which offers mobile industry information, services, and rules, reports 55% 3G subscriber penetration in Eastern Europe, the Middle East, and Sub-Saharan Africa. The UK-based mobile market intelligence company Mobilesquared estimates that just 25% of mobile network operators globally had built a signalling firewall to prevent geolocation spying by the end of 2021. Telecom insiders know that the vulnerabilities in the 3G roaming SS7 signalling protocol have allowed commercial surveillance products to provide anonymity, multiple access points and attack vectors, a ubiquitous and globally accessible network with an unlimited list of targets, and virtually no financial or legal risks.
The research done by Citizen labs focuses on geolocation risks from mobile signalling network attacks. Active or passive surveillance may reveal a user’s position using mobile signalling networks. They may use numerous strategies to do this.
The two methods differ significantly. Active surveillance employs software to trigger a mobile network response with the target phone position, whereas passive surveillance uses a collecting device to retrieve phone locations directly from the network. An adversarial network employs software to send forged signalling messages to susceptible target mobile networks to query and retrieve the target phone’s geolocation during active assaults. Such attacks are conceivable on networks without properly implemented or configured security safeguards. Unless they can install or access passive collecting devices in global networks, an actor leasing a network can only utilise active surveillance tactics.
However, cell operators and others may be forced to conduct active and passive monitoring. In this case, the network operator may be legally required to allow monitoring or face a hostile insider accessing mobile networks unlawfully. A third party might get access to the operator or provider by compromising VPN access to targeted network systems, allowing them to gather active and passive user location information.
The report primarily discusses geolocation threats in mobile signaling networks. These threats involve surveillance actors using either active or passive methods to determine a user’s location.
Active Surveillance:
- In active surveillance, actors use software to interact with mobile networks and get a response with the target phone’s location.
- Vulnerable networks without proper security controls are susceptible to active attacks.
- Actors can access networks through lease arrangements to carry out active surveillance.
Passive Surveillance:
- In passive surveillance, a collection device is used to obtain phone locations directly from the network.
- Surveillance actors might combine active and passive methods to access location information.
Active Attacks:
- Actors use software to send crafted signaling messages to target mobile networks to obtain geolocation information.
- They gain access to networks through commercial arrangements with mobile operators or other service providers connected to the global network.
Vulnerabilities in Home Location Register (HLR) Lookup:
- Commercial HLR lookup services can be used to check the status of mobile phone numbers.
- Surveillance actors can pay for these services to gather information about the target phone’s location, country, and network.
- Actors with access to the SS7 network can perform HLR lookups without intermediary services.
Domestic Threats:
- Domestic location disclosure threats are concerning when third parties are authorized by mobile operators to connect to their network.
- Inadequate configuration of signaling firewalls can allow attacks originating from within the same network to go undetected.
- In some cases, law enforcement or state institutions may exploit vulnerabilities in telecommunications networks.
Passive Attacks:
- Passive location attacks involve collecting usage or location data using network-installed devices.
- Signaling probes and monitoring tools capture network traffic for operational and surveillance purposes.
- Surveillance actors can use these devices to track mobile phone locations, even without active calls or data sessions.
Packet Capture Examples of Location Monitoring:
- Packet captures show examples of signaling messages used for location tracking.
- Location information, such as GPS coordinates and cell information, can be exposed through these messages.
- User data sessions can reveal information like IMSI, MSISDN, and IMEI, allowing for user tracking.
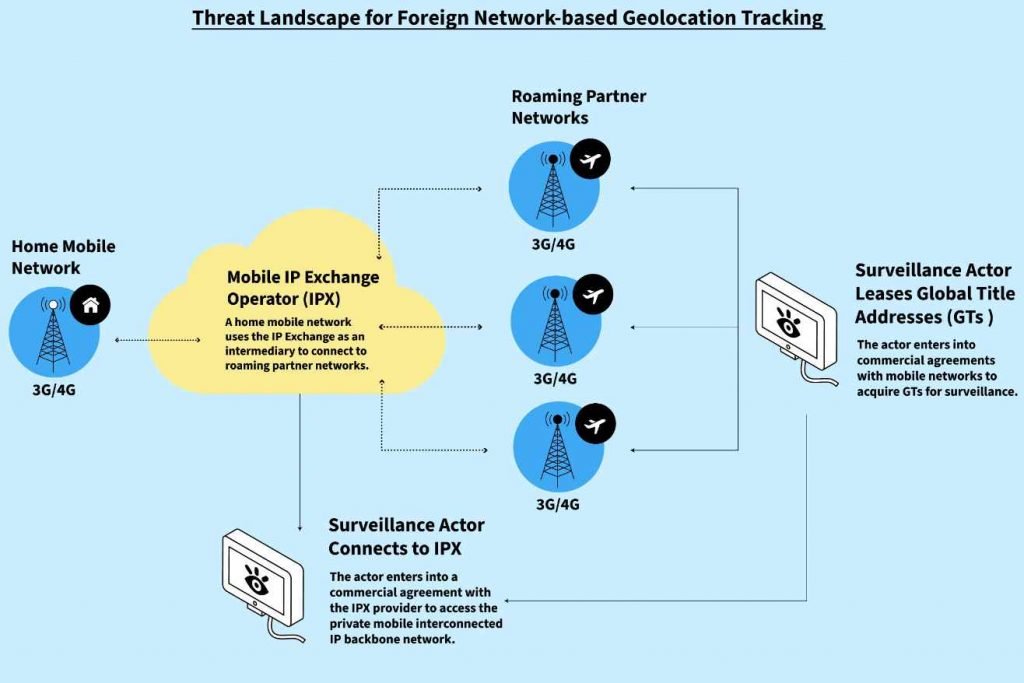
The report highlights the various methods and vulnerabilities that surveillance actors can exploit to obtain the geolocation of mobile users, both domestically and internationally.Based on history, present, and future mobile network security evaluations, geolocation monitoring should continue to alarm the public and policymakers. Exploitable vulnerabilities in 3G, 4G, and 5G network designs are predicted to persist without forced openness that exposes poor practises and accountability mechanisms that require operators to fix them. All three network types provide surveillance actors more possibilities. If nation states and organised crime entities can actively monitor mobile phone locations domestically or abroad, such vulnerabilities will continue to threaten at-risk groups, corporate staff, military, and government officials.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











