BlackCat’s ransomware operators have recently introduced a new tool called “Munchkin,” enabling the propagation of BlackCat payloads to remote machines and shares within a victim’s network. This new tactic involves the use of a customized Alpine Virtual Machine (VM) to deploy the malware, a trend gaining traction amongst ransomware actors to bypass security solutions during malware deployments.
Here’s a detailed breakdown of the new VM Ransomware tactic adopted by BlackCat, based on discoveries made by Unit 42:
- Munchkin Utility Introduction:
- The BlackCat operators announced updates to their toolkit, including a utility named Munchkin.
- Munchkin facilitates the propagation of BlackCat payloads to remote machines and shares within a victim organization’s network.
- The use of Munchkin marks a significant evolution in BlackCat’s ransomware-as-a-service (RaaS) business model, making it more potent and elusive to security measures.
- Customized Alpine VM Usage:
- Munchkin is unique in its deployment, as it leverages a customized Alpine VM.
- This VM tactic allows ransomware actors to bypass security solutions, as most security controls on host OS do not have introspection within the embedded virtualized OS.
- Once the malware is deployed using the VM, it can execute without being interrupted by the security solutions on the host machine.
- Technical Execution:
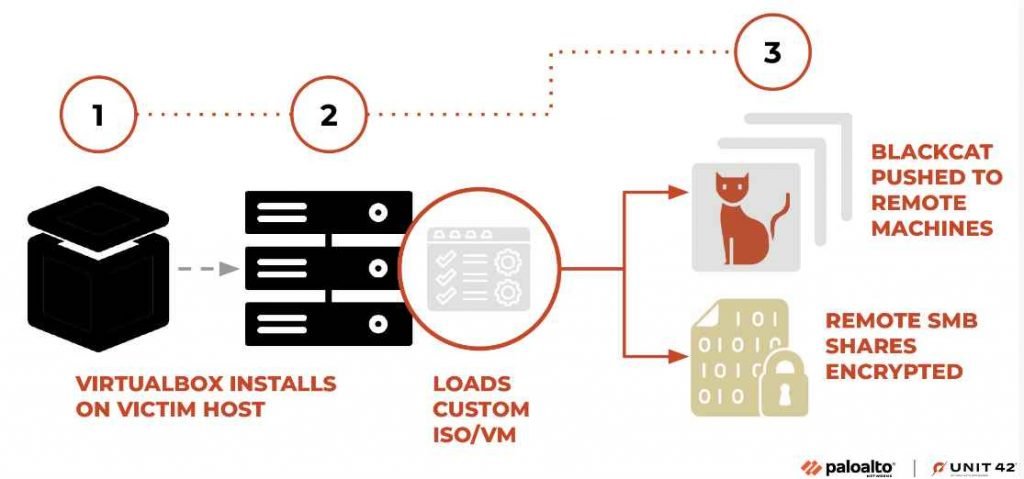
- Munchkin utility is delivered as an ISO file, loaded in a newly installed instance of the VirtualBox virtualization product representing a customized implementation of the Alpine OS.
- Upon running the operating system, specific commands are executed to change the root password of the VM to one chosen by threat actors, generating a new terminal session via the built-in tmux utility to execute the malware binary named controller. Post execution, it powers the VM off.
- Within the VM OS, notable files are hosted that play crucial roles in the malware’s operation, such as the Munchkin malware utility, serialized configuration file used by Munchkin, and a template BlackCat malware sample customized by Munchkin at runtime.
- Escalating Threat:
- The use of VMs for malware deployment is an escalating trend in the ransomware community.
- Other ransomware organizations have also been reported to leverage this new tactic, indicating a paradigm shift in how ransomware is deployed and managed across networks.
- Cybercrime Syndicate ALPHV/BlackCat:
- The cybercrime syndicate ALPHV, also known as BlackCat, initiated this novel tool deployment.
- This development underscores the continual evolution of tactics employed by the BlackCat syndicate, marking a significant step in its operational sophistication.
- Security Implications:
- The evolvement of BlackCat’s tactics, including the use of VMs, underscores a growing need for enhanced security measures to mitigate such advanced threats.
- The Unit 42 researchers hope that shedding light on these tactics will motivate further efforts within the information security industry to better defend against this evolving threat.
- BlackCat’s Evolution:
- Over time, BlackCat has evolved from using unobfuscated configurations to employing obfuscation mechanisms and command-line parameters for added security, illustrating its dynamic threat landscape.
The detailed elucidation of the Munchkin utility and its VM Ransomware tactic provides crucial insights into the advancing methodologies of BlackCat and similar ransomware operators. By understanding these evolving tactics, stakeholders in the cybersecurity domain can better prepare and defend against such sophisticated threats.
The FBI and other agencies have released Indicators of Compromise (IOCs) associated with the BlackCat/ALPHV ransomware, a Ransomware-as-a-Service (RaaS) entity, that has reportedly compromised at least 60 entities worldwide. While the specific IOCs were mentioned in a Flash report by the FBI.
Indicators of Compromise (IOCs):
The Federal Bureau of Investigation (FBI) has outlined specific indicators of compromise (IOCs) pertaining to the BlackCat/ALPHV ransomware activities. Although the exact details were contained in an FBI Flash report, the overarching concern is the worldwide compromise of at least 60 entities through this Ransomware-as-a-Service (RaaS) model. These IOCs are critical for organizations to identify potential threats and take necessary mitigation steps to prevent or respond to ransomware attacks orchestrated by BlackCat/ALPHV. By understanding and monitoring for these IOCs, organizations can significantly enhance their cybersecurity posture against this evolving threat vector.
It’s advisable for organizations and cybersecurity professionals to review official advisories and reports from the FBI and other cybersecurity agencies to stay updated on the latest IOCs and mitigation strategies concerning BlackCat/ALPHV Ransomware and its new VM Ransomware tactic involving the Munchkin utility.
The IOCs released by authoritative bodies like the FBI provide a crucial roadmap for organizations to assess their networks for potential compromises and to bolster their defenses against the evolving tactics of BlackCat/ALPHV Ransomware, particularly with the introduction of the Munchkin utility and the new VM Ransomware tactic.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











