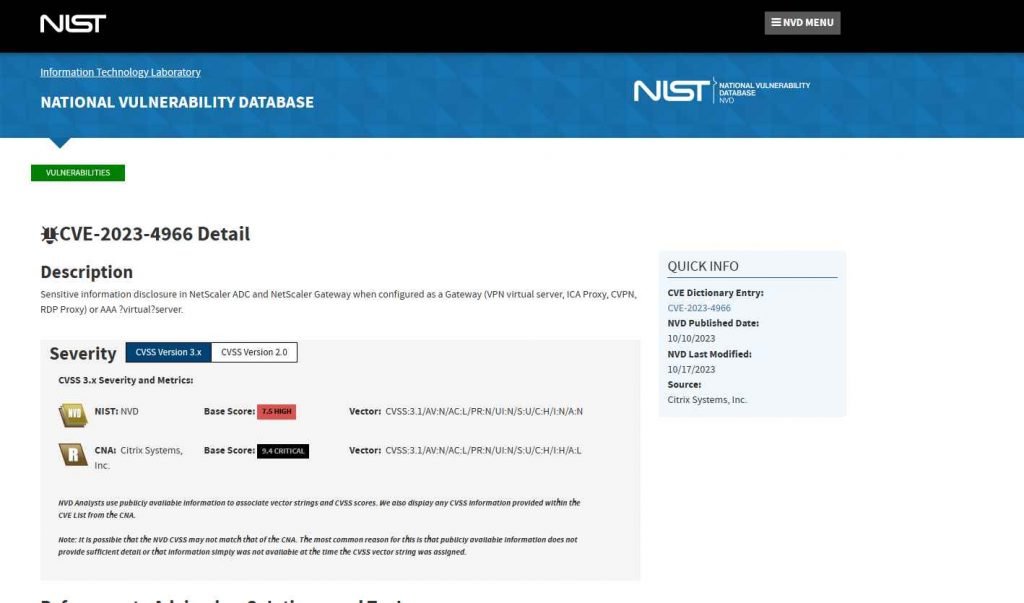
In a digital realm where security forms the bedrock of seamless operations, vulnerabilities act as ticking time bombs, waiting for exploitation. One such critical vulnerability, dubbed CVE-2023-4966, recently surfaced in Citrix NetScaler ADC and Gateway appliances, throwing a multitude of organizations into a state of heightened alert. This article elucidates the essence, impact, and countermeasures surrounding this significant security loophole.
The security glitch, identified as CVE-2023-4966, predominantly pertains to sensitive information disclosure. The appliance must be configured as a Gateway (VPN virtual server, ICA Proxy, CVPN, RDP Proxy) or AAA virtual server to be susceptible to this vulnerability. The core of the issue lies in the Improper Restriction of Operations within the Bounds of a Memory Buffer (CWE-119), with a CVSS score of 9.4, highlighting its critical nature.
Real-world Exploitation
Mandiant shed light on the active exploitation of this vulnerability since August, emphasizing the criticality of the situation. The exploitation entailed unauthenticated buffer-related vulnerabilities, underscoring the urgency of mitigation measures beyond mere patching.
Countermeasures Undertaken:
In a bid to curb the exploitation, Citrix rolled out a patch on October 10, 2023. However, the patch proved to be a half measure, as organizations that had patched their systems continued to face hacks. This revelation underscored the necessity for additional actions alongside patching to thoroughly address the vulnerability. The Cybersecurity and Infrastructure Security Agency (CISA) further accentuated the need for users and administrators to review the Citrix security bulletins and apply the requisite updates to barricade against potential exploits.
Citrix, on October 10, 2023, disseminated a security bulletin concerning the sensitive information disclosure vulnerability, urging users to take remedial actions. Mandiant identified zero-day exploitation of this vulnerability in the wild, which commenced in late August 2023. Successful exploitation could spell significant security implications, thereby necessitating prompt remedial actions.
The vulnerable devices affected by CVE-2023-4966 include:
- NetScaler ADC and NetScaler Gateway versions 14.1-8.50 and later releases.
- NetScaler ADC and NetScaler Gateway versions 13.1-49.15 and later releases of 13.1.
- NetScaler ADC and NetScaler Gateway versions 13.0-92.19 and later releases of 13.0.
- NetScaler ADC 13.1-FIPS versions 13.1-37.164 and later releases of 13.1-FIPS.
The emergence of CVE-2023-4966 unveils the incessant security challenges beleaguering the digital landscape. The vulnerability not only underscores the imperative for robust security frameworks but also for the proactive identification and remediation of security loopholes. As organizations grapple with this security menace, the collaborative efforts between vendors, cybersecurity agencies, and the user community will be pivotal in fostering a more secure digital ecosystem.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











