Comprehensive Analysis: ToddyCat’s Advanced Toolset and Stealthy Cyber Espionage Tactics
ToddyCat, an Advanced Persistent Threat (APT) group, has garnered attention for its clandestine cyber-espionage operations, utilizing a sophisticated toolset designed for data theft and exfiltration. The group employs a myriad of techniques to move laterally within networks and conduct espionage operations with a high degree of secrecy and efficiency. This article, incorporating insights from the article and other sources, aims to provide a detailed overview of ToddyCat’s toolset and operational tactics.
Stealth and Sophistication: ToddyCat’s Modus Operandi
ToddyCat employs disposable malware, ensuring no clear code overlaps with known toolsets, thereby enhancing its ability to remain undetected. The malware is designed to steal and exfiltrate data, while the group employs various techniques to move laterally within networks and conduct espionage operations.
Exploitation Techniques and Malware Utilization
- Disposable Malware: Utilized to enhance stealth and evasion capabilities.
- Data Exfiltration: Malware designed to access and extract sensitive information.
- Lateral Movement: Techniques employed to expand reach and access within compromised environments.
Toolset Summary
- Dropbox Exfiltrator: A tool designed to exfiltrate data, ensuring that stolen information can be securely and covertly transferred to the attackers.
- LoFiSe: A tool that may be utilized for lateral movement and further exploitation within compromised networks.
- Pcexter: A tool that may be used to send specific files or data to external servers, facilitating data exfiltration.
- Dropper: A tool that may be utilized to deploy additional payloads or malware within compromised environments.
Detailed Insights into the Toolset
1. Loaders
- Standard Loaders: ToddyCat utilizes 64-bit libraries, invoked by rundll32.exe or side-loaded with legitimate executable files, to load the Ninja Trojan during the infection phase. Three variants of these loaders have been observed, each differing in aspects like the library loaded by, where the malicious code resides, the loaded file, and the next stage.
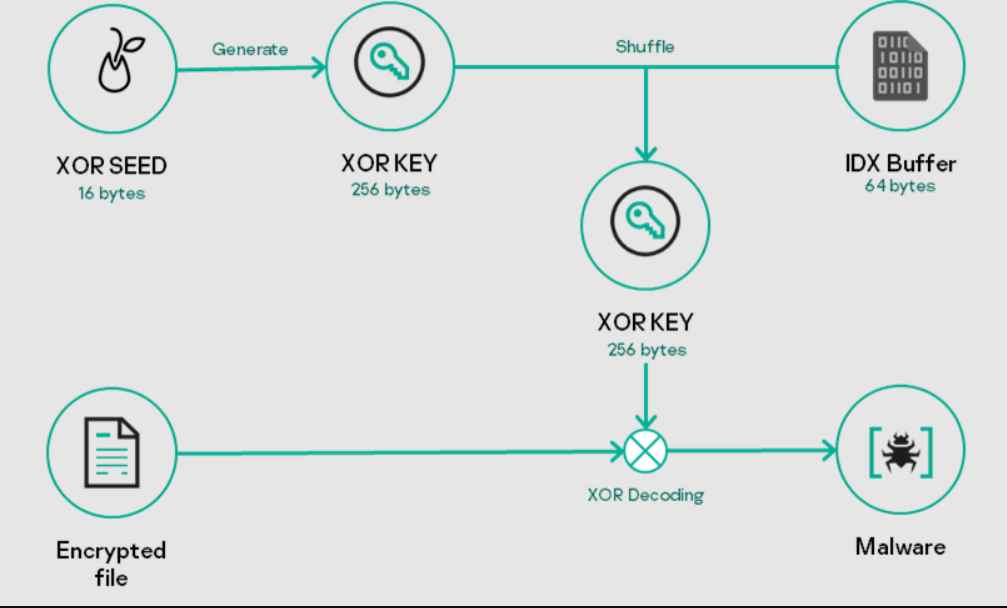
- Tailored Loader: A variant of the standard loader, this is customized for specific systems, employing a unique decryption scheme and storing encrypted files in a different location and filename (%CommonApplicationData%\Local\user.key).
2. Ninja Trojan
The Ninja Trojan, a sophisticated malware written in C++, is a potent tool in ToddyCat’s arsenal. It provides functionalities like:
- Managing running processes
- File system management
- Managing multiple reverse shell sessions
- Injecting code into arbitrary processes
- Loading additional modules during runtime
- Proxy functionality to forward TCP packets between the C2 and a remote host
3. LoFiSe
LoFiSe is a component designed to find and collect files of interest on targeted systems. It tracks changes in the file system, filtering files based on size, location, and extension, and collects suitable files for further action.
4. DropBox Uploader
This generic uploader, not exclusive to ToddyCat, is used to exfiltrate stolen documents to DropBox, accepting a DropBox user access token as an argument and uploading files with specific extensions.
5. Pcexter
Pcexter is another uploader used to exfiltrate archive files to Microsoft OneDrive. It is distributed as a DLL file and executed using the DLL side-loading technique.
Potential Impact and Threat Landscape
The emergence of ToddyCat’s new toolset and its sophisticated TTPs presents a significant threat to organizations, with potential impacts including data breaches, unauthorized access to sensitive information, and network compromise.
Mitigation and Defense Strategies
- Enhanced Monitoring: Implementing monitoring solutions to detect anomalous activities.
- User Education: Ensuring users are educated about potential threats and cybersecurity best practices.
- Regular Patching: Keeping all systems regularly patched and updated.
- Threat Intelligence: Leveraging intelligence to stay abreast of the latest TTPs employed by threat actors.
ToddyCat’s advanced toolset and stealthy operations underscore the evolving and sophisticated nature of cyber threats. Organizations and cybersecurity practitioners must remain vigilant and adopt advanced cybersecurity practices to defend against the sophisticated tools and tactics employed by threat actors like ToddyCat.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











