As part of an ongoing cyber espionage effort, the Iranian nation-state hacking group known as OilRig has continued to target government entities in the Middle East. This cyber espionage campaign makes use of a newly discovered backdoor in order to exfiltrate data. OilRig (APT34) is an Iranian cyberespionage gang that has been active since 2014 and has been targeting different sectors and governments in the Middle East, including Chemical, Energy,Finance and Telecom.
Following the commencement of the DNSpionage operation in 2018-2019 targeting Lebanon and the UAE, OilRig began the HardPass operation in 2019-2020 utilizing LinkedIn to target individuals in the energy and government sectors.
In recent weeks, the experts in charge of cybersecurity at trendmicro have discovered and assessed two campaigns run by the OilRig APT group:
Outer Space (2021)
Juicy Mix (2022)
Due to the operations’ concentration on the Middle East, Israeli organizations were the only ones targeted by these cyberespionage efforts. They gained access to the network by posing as genuine businesses using VBS droppers to plant C# and.NET backdoors and post-compromise data mining tools.
An Overview of the Campaign
Outer Space: It was an OilRig campaign from the year 2021 that employed an Israeli HR website as a command and control server for the Solar backdoor. . Here, with just the most fundamental functionalities, the Solar linked to the SC5k downloader, while the MKG was utilized for data exfiltration from browsers.
OilRig started a new campaign in 2022 called “Juicy Mix.” It targeted Israeli organizations with improved tools, compromised a job site for command and control, and then attacked an Israeli healthcare organization with a Mango backdoor, two hidden browser-data dumpers, and a Credential Manager stealer. Juicy Mix was a hit.
In order to get access to the target system, both attacks used VBS droppers, which were most likely distributed using spear phishing emails.
These droppers distributed Mango, made sure the infection would remain, and linked to the command and control server. Concealing the base64 encoding and basic string deobfuscation that the embedded backdoor employed at the same time was accomplished using these methods.
After inserting the backdoor, the dropper transmits the compromised computer’s name to the command and control server in the form of a base64-encoded POST request. This is done after it has scheduled Mango (or Solar) to run every 14 minutes.
During the Outer Space campaign, OilRig launches Solar, a backdoor that is both simple and flexible. It is able to download and run files, as well as independently exfiltrate prepared data.
Mango, which had previously been known as Solar, has been replaced in Juicy Mix by OilRig’s Mango, which, although having similar features and a workflow, has substantial differences.
In the same way as Solar did, Mango starts an in-memory job that runs every 32 seconds, talks with the C&C server, and carries out orders. Mango, on the other hand, is distinct in that it replaces Solar’s Venus assignment with a whole new exfiltration command.
Post-compromise tools
The following post-compromise tools are included below for your convenience:
Downloader for SampleCheck5000, often known as SC5k
Data scrapers for browsers
Windows Credential Manager stealer
OilRig makes its way from Solar to Mango via implants that function similarly to backdoors. While they do make use of specialized technology for data collecting, they nevertheless rely on more traditional methods to get user information.
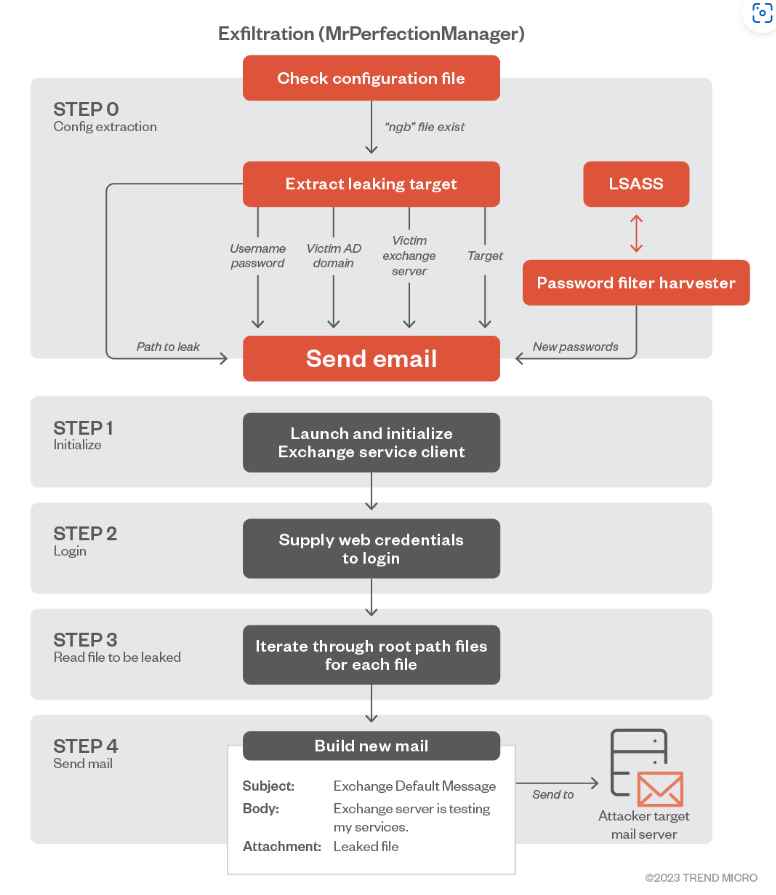
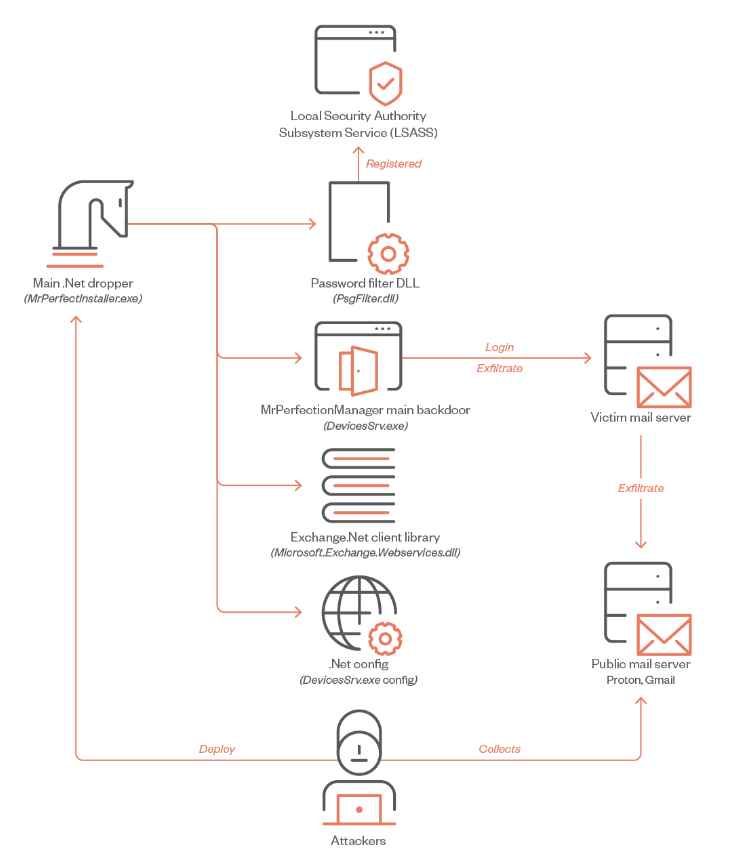
The parallels between the first-stage dropper and Saitama, the victimology patterns, and the usage of internet-facing exchange servers as a communication technique were identified in the case of Karkoff, which is how the campaign is connected to APT34.
If anything, the rising number of malicious tools connected with OilRig illustrates the threat actor’s “flexibility” to come up with new malware depending on the targeted environments and the privileges held at a particular stage of the assault. This “flexibility” may be inferred from the fact that the threat actor has created a growing number of harmful tools linked with OilRig.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.










