According to the findings of Akamai’s security experts, a high-severity vulnerability in Kubernetes may be exploited to accomplish remote code execution (RCE) on any Windows endpoints that are part of the cluster.
The flaw, identified as CVE-2023-3676 and with a CVSS score of 8.8, affects Kubernetes’ processing of YAML files. These files are used by the container orchestration system for a variety of purposes, including configuration, management, and the handling of secrets, among other things.
YAML files are used for almost every aspect of Kubernetes’ operation, including configuration, automatic deployment, scalability, administration of containerized application pods, and a great many others.
It was discovered in 2022 that the constructor of SnakeYAML included the CVE-2022-1471 vulnerability, which allowed for the execution of remote code in applications that were susceptible.
Many vulnerabilities were found by Kubernetes itself, such as CVE-2021-25749 (workloads might execute as ContainerAdministrator even though the runAsNonRoot option was set to true), CVE-2017-1002101, and CVE-2021-25741 (race situations and symlinks in combination with the subPath subproperty in a YAML file).
When users establish a pod, they also have the option of creating a shared directory between the pod and the host. This directory is referred to as “volumes.”
In order to make the volumes accessible, the YAML file has to have the volume parameter added to it, in addition to the mountPath (which specifies the location of the container) and the hostPath (which specifies the location of the host).
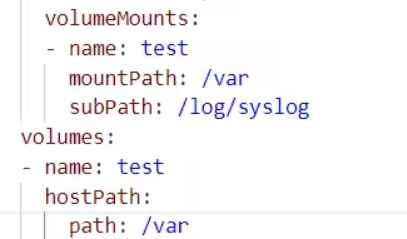
Mounting the shared directory at a specific place may also be accomplished with the help of the subPath subproperty. This YAML file is then read by kubelet, which verifies every parameter in the YAML file and uses the isLinkPath inner function to make sure that no symlinks are formed on the subPath argument. A PowerShell command to determine the path type is generated by taking the subPath subproperty from the YAML file and using it as a parameter in the command. After that, the exec. Command function call receives this PowerShell command and processes it.
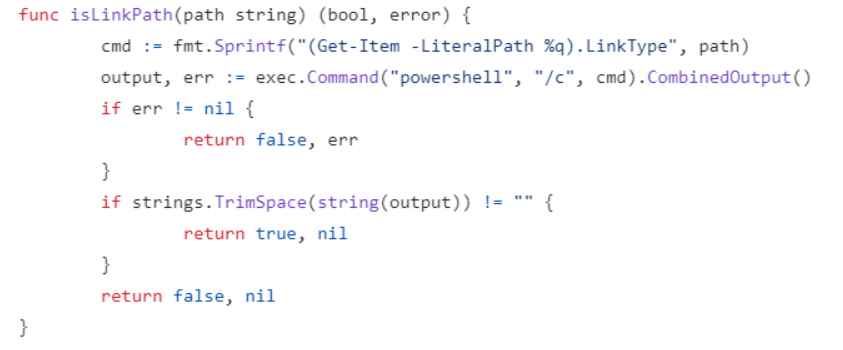
An further research discovered that the “exec.Command” variable may be used in conjunction with user input that has not been sanitized, which results in a command injection vulnerability.
Disabling the usage of Volume.Subpath, utilizing the open source Open Policy Agent (OPA) agent to set rules to prohibit particular YAML files, and applying role-based access control (RBAC) to restrict the number of users who may conduct activities on a cluster are some of the recommended remedies.
“CVE-2023-3676 demands minimal privileges and, as a result, establishes a low threshold for attackers. All an attacker needs is access to a node and the ability to apply privileges. “High impact coupled with ease of exploitation usually means that there is a higher chance of seeing this attack (and similar attacks) on organizations,” writes Akamai. “High impact coupled with ease of exploitation also means that there is a higher chance of seeing similar attacks.”

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











