Following the disclosure of a serious flaw in the Microsoft Power Platform, researchers in the field of information security are advising users of Azure Active Directory (AD) to keep an eye out for abandoned reply URLs. To be more precise, the researchers discovered an unused reply URL address inside an Azure Active Directory application that was associated with the low-code Power Platform.
Attackers have the potential to utilize the URL to redirect authorization codes to themselves, then trade them for access tokens. After then, the threat actor might get higher access by using the Power Platform API via a middle-tier service.
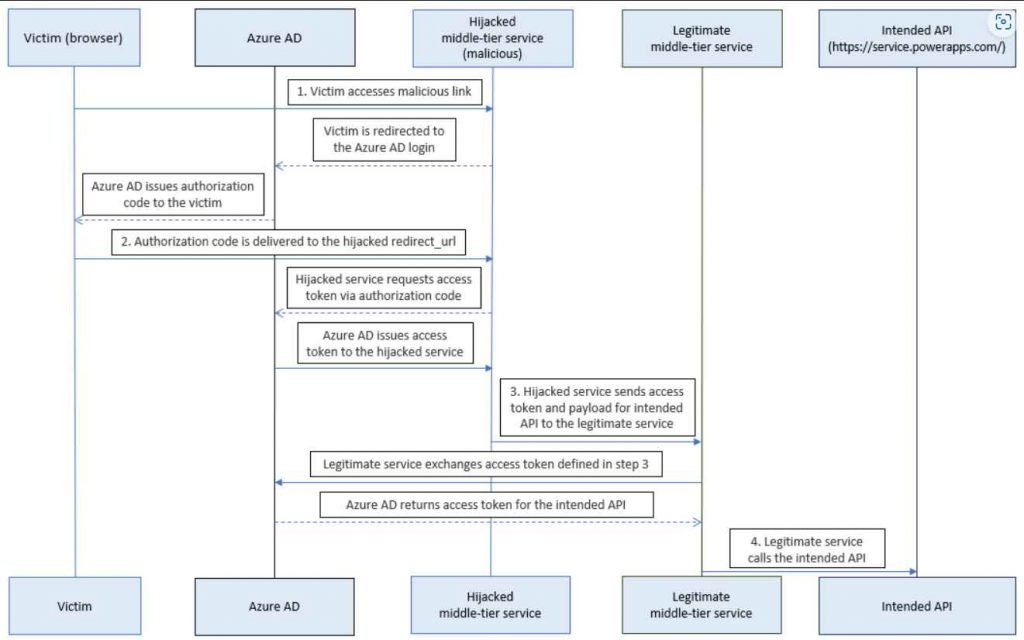
The term “reply URL,” which is synonymous with the term “redirect URI,” describes the site to which the user is sent by the authorization server after the app has been successfully approved and has been provided either an authorization code or an access token. It was feasible to contact the Power Platform API via a middle-tier service and tamper with the environment parameters, according to Secureworks CTU, which discovered an abandoned Dynamics Data Integration app reply URL connected with the Azure Traffic Manager profile.
Users are granted the ability to manage environments, alter environment parameters, and query capacity usage using the Power Platform API. Because of this, threat actors that are looking for privileged access will focus their attention on it as a primary target.
This might have been used in a hypothetical attack scenario to gain the system administrator role for an existing service principal, submit requests to destroy an environment, and misuse the Azure AD Graph API in order to collect information about the target in order to stage follow-on operations.
However, this relies on the potential that a victim may click on a malicious link. If this occurs, the authorization code that is generated by Microsoft Entra ID when signing in will be sent to a redirect URL that has been taken over by the threat actor.
Secureworks issued a warning that potential attackers who are aware of the inner workings of the Power Platform admin API might likely design more attack scenarios.
In the end, Microsoft swiftly fixed the issue by eliminating the problematic abandoned reply URL from the Azure AD application.
However, Secureworks advised security administrators to keep a close check on the reply URLs used by their Azure AD apps in order to prevent an attack scenario similar to the one that was shown before.
After the vulnerability was responsibly disclosed on April 5, 2023, Microsoft provided an update the next day that fixed it, so resolving the problem. The company has also released an open-source application that other businesses may use to search for abandoned reply URLs.
“Organizations are unable to directly mitigate this issue as the identified application is managed by the vendor,” the report came to the conclusion. “The only choice available to you is to delete the service principal, which will prevent you from making any legal use of the application. We strongly advise keeping an eye out for obsolete reply URLs.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











