CVE-2023-36874 is not just any vulnerability; rather, it is a zero-day that is being actively exploited. This indicates that the vulnerability was being exploited in the wild even before any remedy was provided, and in some cases, even before it was publicly acknowledged. Because they provide a window of opportunity before updates are sent out, vulnerabilities of this kind are often among the top targets for cybercriminals.
However, taking advantage of this vulnerability is not as simple as one may first believe it to be. According to the advisory notes published by Microsoft, “An attacker must have local access to the targeted machine and must be able to create folders and performance traces on the machine, with restricted privileges that normal users have by default.”
This significantly reduces the danger vector, but it does not remove it entirely. Because Windows is so prevalent throughout the world, even a very minor security flaw may put millions of machines at danger.
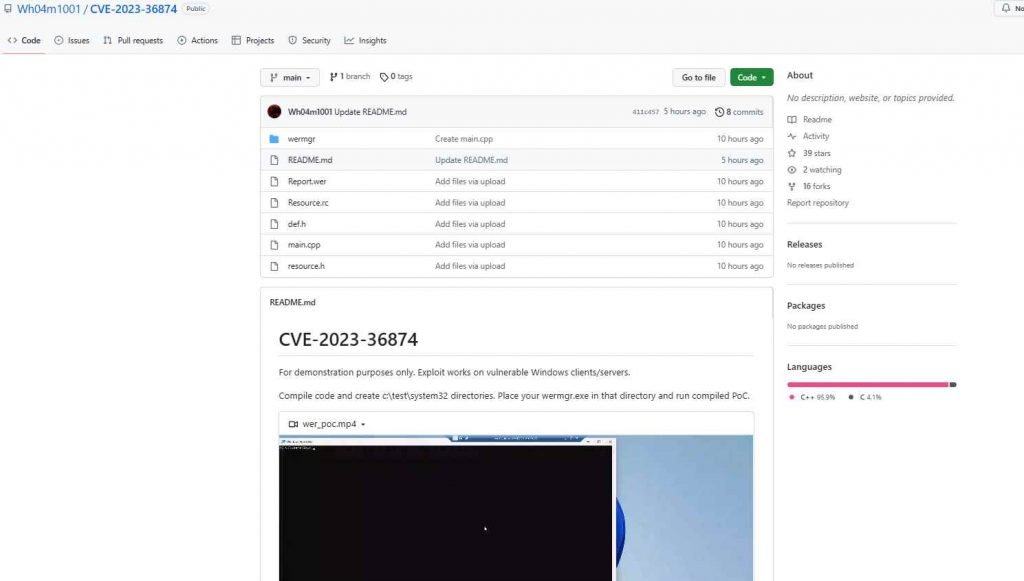
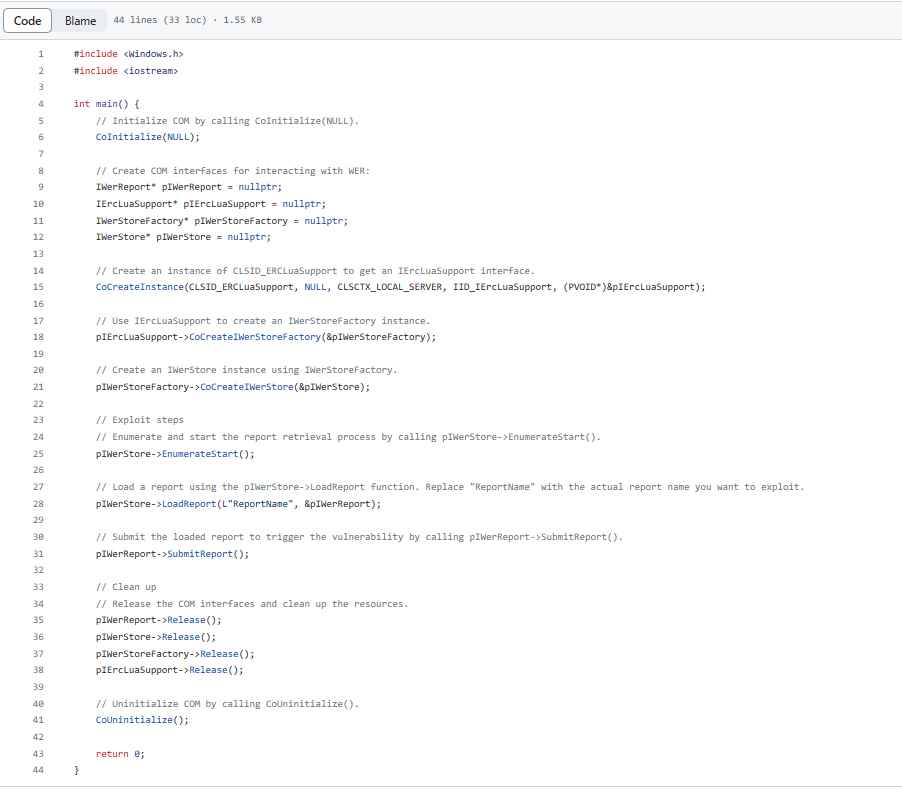
Security researchers issued a warning to Windows users yesterday, informing them that he has developed a proof-of-concept (PoC) attack for the CVE-2023-36874 vulnerability. The Windows Error Reporting Service (WER), a component that gathers and transmits error reports to Microsoft, is susceptible to the vulnerability, which has been assigned a CVSS score of 7.8. Because of an issue in the way that WER processes specifically designed requests, the system is susceptible to this vulnerability. An adversary might take use of this vulnerability by developing a malicious software specifically intended to take advantage of the hole in the system. Once the malicious application has been run on the system, the attacker may be able to get higher rights on the machine. According to Microsoft, the vulnerability was discovered by two members of Google’s Threat Analysis Group (TAG), namely Vlad Stolyarov and Maddie Stone.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











