The Internet of Things (IoT) is now experiencing its zenith and is quickly growing its capabilities. This is being accomplished through the transformation of commonplace goods, such as light bulbs and plugs, into smart devices that can be controlled using a smartphone.
The number of Internet of Things devices surpassed 13.8 billion in 2021; by 2025, that number is expected to quadruple. However, this massive increase also offers a great number of attack opportunities for threat actors, which presents security experts with a number of issues.
Recently, cybersecurity specialists from different universities discovered that cybercriminals may hack smart bulbs in order to collect Wi-Fi credentials. The researchers chose the Tp-Link Tapo Smart Wi-Fi Multicolor Light Bulb (L530E) in order to do the Vulnerability Assessment and Penetration Testing (VAPT) on smart bulbs. To do so, they used the PETIoT, a novel IoT-focused Kill Chain (KC) that identifies network vulnerabilities.
Because it is a cloud-enabled multicolor smart bulb, the Tapo L530E may be operated using the Tapo app on an Android or iOS device without the need for a hub. Instead, it connects directly to the home Wi-Fi network. According to the findings of the researchers, this particular kind of smart bulb is susceptible to each of the following four vulnerabilities:
Lack of authentication of the smart bulb with the Tapo app (8.8 CVSS score, High severity)
Hard-coded, short shared secret (7.6 CVSS score, High severity)
Lack of randomness during symmetric encryption (4.6 CVSS score, Medium severity)
Insufficient message freshness (5.7 CVSS score, Medium severity)
The examination and testing carried out by the security experts indicate the proximity-based attacks that were carried out on the smart bulb that was the target.The attack scenario that causes the greatest concern is one in which an attacker impersonates a bulb and retrieves information about a Tapo user account by exploiting vulnerabilities.
After that, the attacker may extract the victim’s WiFi SSID and password by using the Tapo app, allowing them to obtain access to any and all other devices that are connected to the victim’s network.
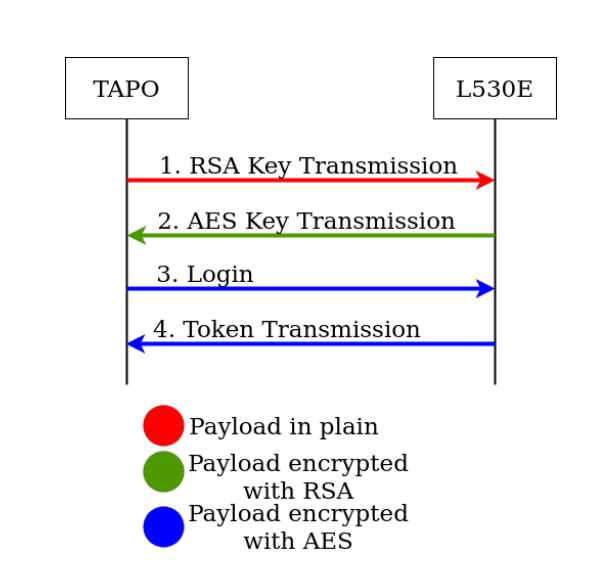
In order for the attack to be successful, the device in question must first be put into setup mode. However, the attacker has the ability to deauthenticate the bulb, which will need the user to re-configure it in order to get the light to work again.The researchers also investigated an MITM (Man-In-The-Middle) attack using a configured Tapo L530E device. This form of attack takes advantage of a vulnerability to intercept and control the connection between the app and the bulb, as well as to capture the RSA encryption keys that are used for further data transmission.
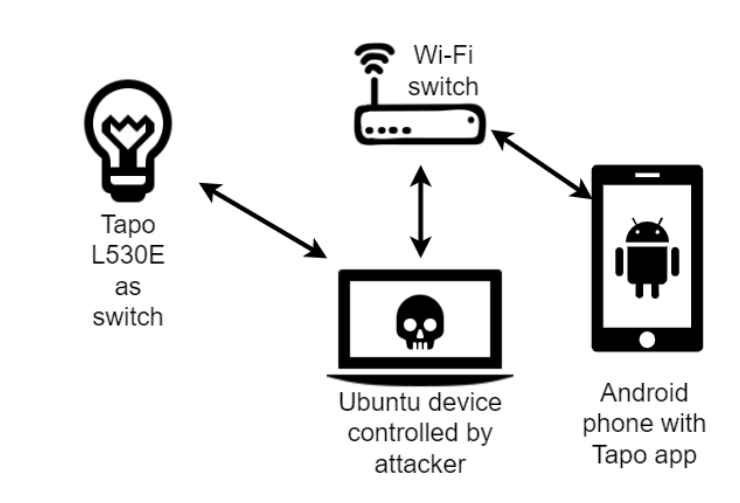
MITM attacks are also possible with unconfigured Tapo devices by leveraging a vulnerability once again by connecting to the WiFi during the setup process, bridging two networks, and routing discovery messages. This will eventually allow the attacker to retrieve Tapo passwords, SSIDs, and WiFi passwords in an easily decipherable base64 encoded form. Last but not least, a further flaw enables attackers to conduct what are known as “replay attacks.” These attacks involve recreating communications that have been sniffed in the past in order to bring about functional changes in the device.

In addition, the security analyst have previously alerted TP-Link about these discoveries in relation to their product the “Tapo Smart Wi-Fi Multicolor Light Bulb (L530E).”
In response, TP-Link gave the researchers their assurance that the issues that were found in their software as well as the firmware of the bulb will be fixed.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











