Researchers have discovered that malicious actors have been utilizing the phishing toolkit EvilProxy to gain control of cloud-based Microsoft 365 accounts belonging to leaders at well-known firms. These accounts are used to access sensitive company data.
According to a study on the events that was published on Wednesday by the cybersecurity company Proofpoint, the attacks demonstrated both the ubiquity of pre-packaged phishing-as-a-service toolkits as well as the increasing bypassing of multi-factor authentication in order to get access to accounts.
It was discovered that EvilProxy was sending 120,000 phishing emails to more than a hundred different companies in an attempt to obtain Microsoft 365 credentials. In the last five months, Proofpoint has seen a concerning increase in the number of successful compromises of cloud account credentials. The vast majority of the attacks were directed against high-ranking officials. According to the researchers’ estimates, the campaign targeted more than one hundred firms throughout the world, which had a total of one and a half million workers.
There were around 39% C-level executives among the victims, 17% of whom were Chief Financial Officers, and 9% of whom were Presidents and CEOs.
At least 35 percent of all users whose accounts were compromised in the previous year had MFA activated, which the researchers discovered to be a substantial rise in the number of account takeovers that occurred among renters who had MFA protection.
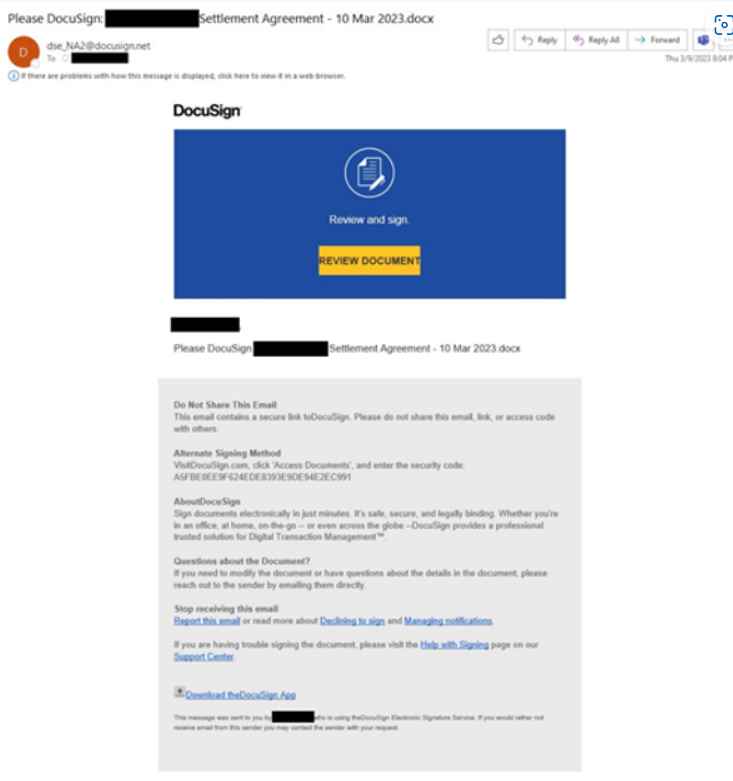
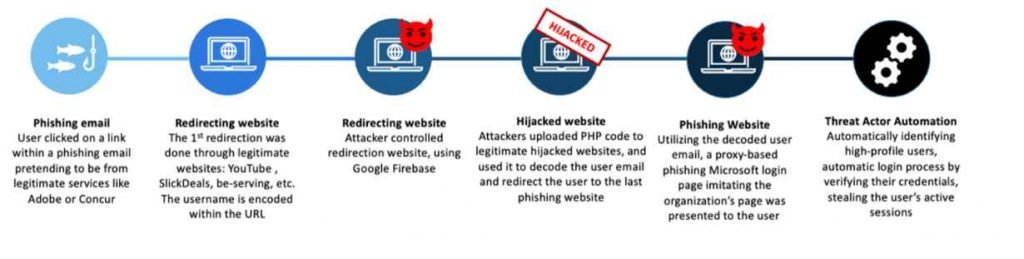
Threat actors operating at a very large scale relied heavily on brand impersonation, evasion strategies, and a multi-step infection chain (threat actors redirected traffic through open genuine redirectors).
Researchers from ReSecurity stumbled into the Phishing-as-a-Service (PhaaS) platform known as EvilProxy in September of 2022. The site was offered on the Dark Web. According to some reports, the alternate moniker is Moloch, which may have some link to a phishing-kit that was built by a number of well-known underground players who previously attacked financial institutions and the e-commerce industry.The bundle may be purchased anonymously on the dark web for a sum of four hundred dollars as of the autumn of last year.
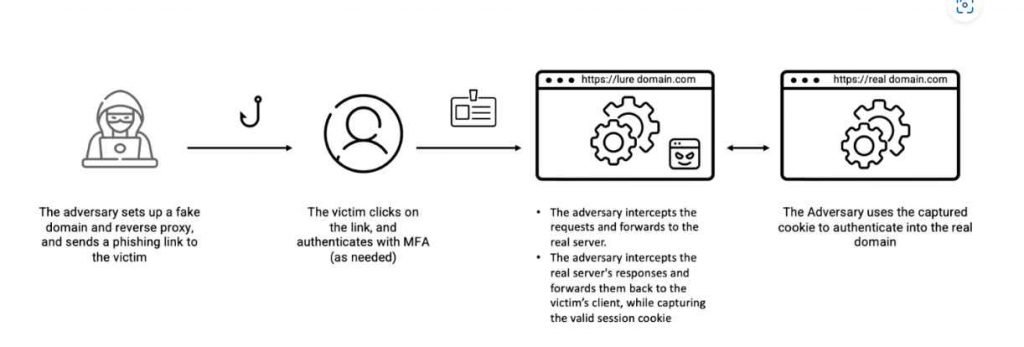
As per experts EvilProxy actors circumvent two-factor authentication by using the Reverse Proxy and Cookie Injection techniques. This allows them to proxy the victim’s session. However, now that these approaches have been effectively productized in EvilProxy, it emphasizes the relevance of the development in attacks against online services and MFA authorization systems. In the past, similar tactics have been observed in the targeted campaigns of APT and cyberespionage organizations.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











