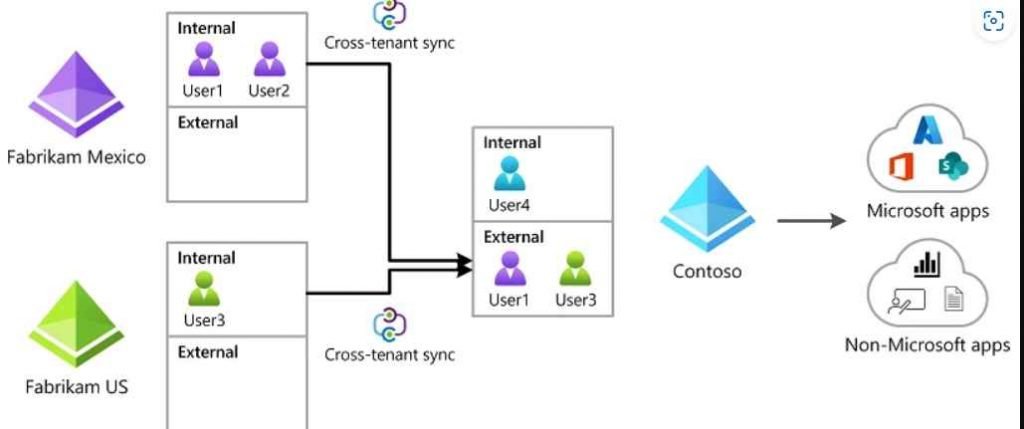
Attackers are still focusing their attention on Microsoft identities in the hopes of breaking into linked Microsoft apps and federated SaaS applications. In addition, attackers continue to advance their attacks in these contexts, however they do so not by taking advantage of vulnerabilities but rather by misusing core Microsoft features in order to accomplish their goal. It has been revealed that the attacker organization Nobelium, which has been associated with the SolarWinds attacks, used native capability such as the formation of Federated Trusts in order to provide permanent access to a Microsoft tenancy. CTS is a new technology offered by Microsoft that gives companies the ability to synchronize users and groups from various source tenants and then provide those users and groups access to resources in the destination tenant. These resources may include both Microsoft and non-Microsoft applications. The CTS features expand on prior B2B trust settings to enable automatic and smooth cooperation across various tenants. This is a feature that many businesses will wish to implement, and it is a capability that builds on past B2B trust configurations. CTS is a strong and valuable tool for organizations like corporate conglomerates with various tenants across related firms.
However, if it is not set and maintained effectively, it presents the opportunity for spying, lateral movement, and persistence assaults by malicious actors. CTS makes it possible to add people from another tenancy to a target tenant by syncing their user accounts.
It is possible to migrate laterally from a compromised tenant to another tenant of the same or a different company by exploiting a CTS setting that has been setup in a lax manner and that may be abused by an attacker. It is possible to install a malicious CTS configuration and utilize it as a backdoor approach in order to keep access to a Microsoft tenancy that is controlled by an external attacker.
Vectra AI, a cybersecurity company, recently produced a research in which it elaborated on how threat actors might use this capability to propagate laterally to related tenants or even employ this feature for persistence.
However, they also caution that in order to abuse this functionality, a threat actor must first either compromise a privileged account or acquire privilege escalation in a Microsoft cloud environment that has already been compromised. The first method detailed in Vectra AI’s paper entails evaluating the CTS settings in order to find target tenants linked via these policies and, more particularly, searching for tenants with the ‘Outbound Sync’ feature enabled, which enables synchronizing with other tenants.
After discovering a tenant that satisfies those requirements, the attacker finds the application that is used for CTS synchronization and adjusts its settings in order to include the compromised user inside its sync scope. This gives the attacker access to the network of the other tenant. Because of this, it is possible for the threat actor to accomplish lateral movement without the need for fresh user credentials.
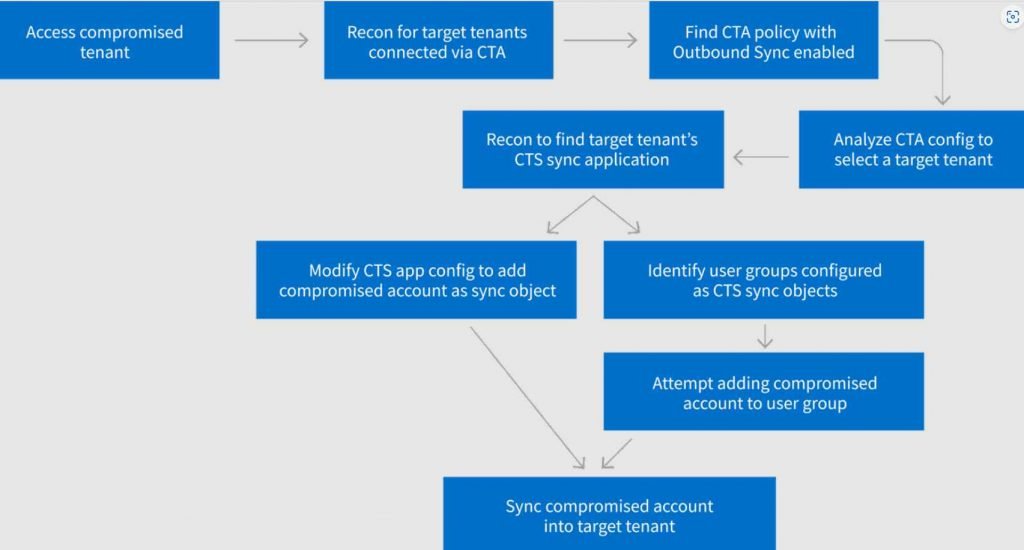
The second method that Vectra demonstrates includes establishing a rogue CTS configuration in order to maintain permanent access to the tenants that are the focus of the attack. It should be emphasized once again that in order for this strategy to work, the threat actor must have already succeeded in compromising a privileged account inside the tenant.
To get more specific, the attacker installs a new CTS policy and activates ‘Inbound Sync’ and ‘Automatic User Consent,’ which gives them the ability to push new users from their external tenancy to the target at any moment.
Because of the way this arrangement is configured, the attacker will always have access to the target tenancy via the external account.
Even if the rogue accounts are deactivated, the attacker may still create and “push” new users at anytime, obtaining instant access to the resources of the target tenancy. This is the reason why the researchers refer to this as a “backdoor.”
Defense
The methods of attack described in this article presume the presence of a compromise. The continued implementation and enforcement of security best practices inside businesses is required to continue lowering the chance of accounts being compromised.
CTS Target residents are required to:
It is best to steer clear of the practice of establishing a default inbound CTA setup if at all possible, since this would allow any users, groups, and apps from the source tenancy to sync inbound.
Implement an incoming CTA setup that is less inclusive, such as specifically designating accounts (if it’s at all feasible) or groups that can receive access via CTS.
In order to block access by unauthorized users, combine the CTA policy with any additional Conditional Access Policies.
Tenants of CTS Source are required to:
Ensure that all privileged groups, including those that are permitted access to other tenants through CTS, are subject to the appropriate levels of regulation and monitoring.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











